In the second year of the coronavirus pandemic, companies still have a lot of catching up to do when it comes to securing their IT. The ongoing situation with working from home is playing into the hands of cyber criminals and they are capitalising on it. IT managers ultimately need to act and replace hastily implemented makeshift remote working structures, with a secure IT infrastructure.
G DATA threat report: Qbot supersedes Emotet
Cyber attacks on companies rise sharply
The latest threat report from G DATA shows that cyber criminals have already found a successor to Emotet - Qbot. The malware was involved in almost one in four averted attacks. The figures show that companies in particular were being targeted by cyber criminals in the first quarter. Within a year, the number of averted attacks rose by more than 60 percent.

The current threat report from G DATA CyberDefense shows that companies are being targeted more strongly by cyber criminals. While the number of averted cyber attacks on private users has only changed slightly - an increase of 1.9 percent when comparing the first quarter of 2020 to the first quarter of 2021 - the number of attacks on companies has increased significantly. The number of attacks averted between January and March of this year was 61.7 percent higher than in the same period last year. This period also includes numerous attacks on Exchange servers, which have caused - and will continue to cause - problems for many companies.

Emotet is dead! Long live Qbot!
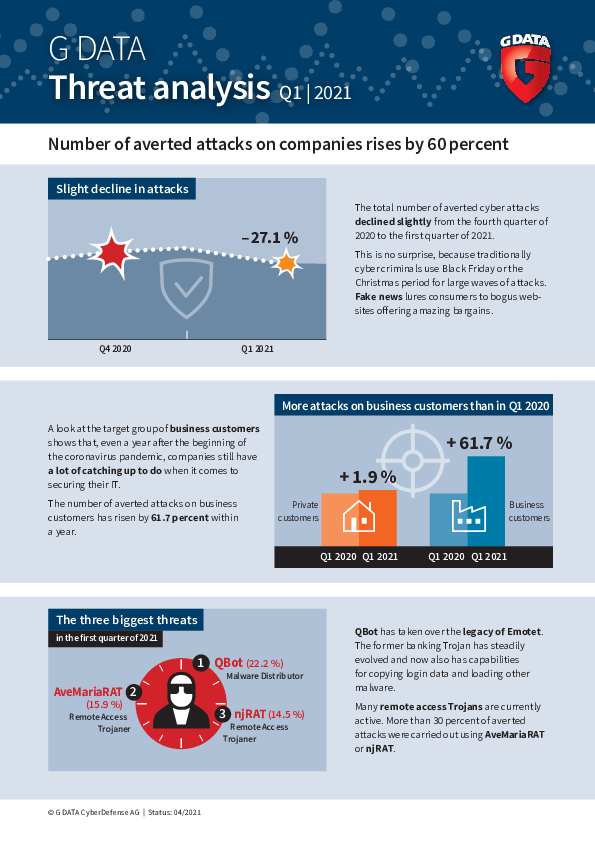
When Emotet was shut down in an internationally coordinated effort at the end of January, one question was quickly raised: which malware will succeed the all-purpose weapon of cyber crime? The answer is Qbot. Current figures show that Qbot is involved in 22 percent of all averted attacks. Originally a banking Trojan, the malware has been gradually developed in a modular fashion by the attackers. It now has additional worm elements and acts as a credential stealer and a loader. The criminals are currently exploiting existing email conversations and adding a new message containing a link to a compromised website with a .zip archive. Qbot then downloads this .zip and installs the malware on the computer. Qbot's attack list currently includes health organisations, government agencies, financial institutions and retail companies.
Attacks are becoming more and more professional
In addition to Qbot, a noticeable number of remote access Trojans (RATs) are currently active. More than 30 percent of averted attacks were carried out using AveMariaRAT or njRAT. RATs enable remote control and administrative monitoring of a third-party computer without the user noticing. Among other things, attackers can view the victim's desktop, log keystrokes, access the camera, steal the login information stored in browsers or upload and download files.
Current RAT campaigns especially show that the trend is moving towards ever more professional cyber attacks. Criminals are increasingly acting in a division of labour and assemble individual components into a modular infection chain and market those in a malware-as-a-service model. Detailed analysis of a current campaign by the Aggah group shows that the attackers try to deactivate protection and detection mechanisms on the infected computer after the user has activated a malicious macro in a phishing email. The initial script looks to see which endpoint protection solution is installed on the system and then selects the next script to trick the protection solution. In addition, the attackers are also modularising their infrastructure by storing malicious code on text-sharing platforms like Pastebin and calling it from there.

Now more than ever, companies have to pay attention to the human factor in IT security. The remote working situation and the pandemic have put employees under stress, making them more vulnerable to attack attempts. Due to the physical proximity between work and private life, many employees are less on their guard than they would be otherwise, so they are more likely to click on a fake email. Also, there is often no direct exchange with colleagues who they would normally ask for advice.
