We think that numerous companies fell victim to an attack last year due to the hasty move to working from home - but have yet to notice this. Cyber criminals continue to mercilessly exploit any weakness in IT security. Critical security gaps, missing updates or careless employees are usually the cause of a successful attack. And people’s current insecurity is significantly accelerating this development
G DATA threat analysis 2020: cyber attacks every second
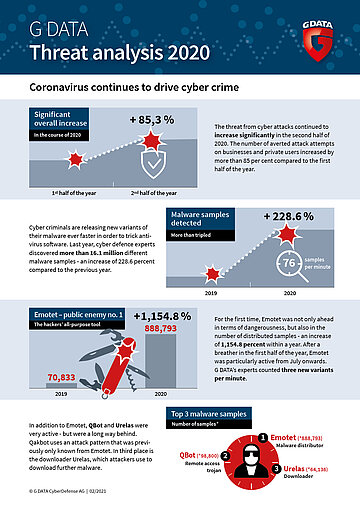
The number of averted cyber attacks rises by more than 85 per cent from the first half of the year to the second
The pandemic is still high season for criminals, as they exploit people's uncertainty to mount attacks. According to the latest threat analysis from G DATA CyberDefense, the number increased by 85 percent in the second half of the year. Cyber criminals released 76 new versions of malware every minute last year. Security vulnerabilities such as Shitrix and Sunburst also served the attackers well for their malicious activities.
The threat from cyber attacks has continued to increase significantly in the past year. The current threat analysis from G DATA CyberDefense shows that the number of averted attack attempts increased by more than 85 percent within six months, when comparing the first half of 2020 to the second. While the number of prevented attacks almost doubled from the second to the third quarter, the number of attacks declined slightly in the fourth quarter.

Old malware in a new guise
The striking thing is that cyber criminals are relying on tried and tested malware, some of which has been in use for several years but is constantly being redeveloped. The following figure shows how great the danger is at this point: more than 16.1 million different malware samples were discovered by cyber defence experts at G DATA. This is an increase of 228.6 percent compared to the previous year. On average, 44,135 new malware samples threaten IT systems in Germany every day. This means that cyber criminals published 76 new versions of malware every minute.
For the first time, Emotet, the all-purpose weapon of cyber crime, is not only ahead in terms of dangerousness, but also in the number of distributed samples, with a grand total of 888,793 different versions in 2020. In the entire previous year, there were only 70,833 samples - this constitutes an increase of 1,154.8 percent. Emotet was largely inactive in the first half of the year, so only 27,804 new samples appeared in this period. This means that more than 860,000 versions appeared in the second half of the year. To add a sense of scale - the criminals released three new variants every minute. Emotet acts as a door opener and provides cyber criminals with access to IT networks. The malware automatically downloads other malicious software such as Trickbot and Ryuk to spy on other access data and encrypt the system.
The Malware Top Ten at a glance
| Position | Name | Variants | Type |
| 1 (6) | Emotet | 888.793 | Malware Distributor |
| 2 (-) | QBot | 98.800 | Remote Access Trojans |
| 3 (-) | Urelas | 64.136 | Downloader |
| 4 (2) | njRAT | 63.969 | Remote Access Trojans |
| 5 (10) | NanoCore | 52.736 | Remote Access Trojans |
| 6 (-) | Trickbot | 50.043 | Malware Distributor |
| 7 (-) | AgentTesla | 47.739 | Information-Stealer |
| 8 (-) | RemcosRAT | 43.902 | Remote Access Trojans |
| 9 (-) | Dridex | 43.563 | Malware Distributor |
| 10 (7) | Shifu | 36.892 | Banking-Trojans |
| Vorjahresplatzierung in Klammern |
The development of cyber crime is highly dynamic. This is confirmed by the fact that six out of ten most frequently detected malwares have not previously made an appearance on this list. Way behind Emotet are QBot and Urelas. Qbot currently uses an attack pattern that was previously only known from Emotet. The attackers send a fake reply to a actual legitimate email conversation which already taking place. For the recipient, this fake email is very hard to distinguish from a legitimate message, so the victims open the email attachment or click on the link. Originally a banking Trojan, it has additional worm elements and acts as a credential stealer to copy users’ login data. Thus, Qbot is another multi-purpose weapon for cyber criminals. In third place in the malware Top 10 is the downloader Urelas, which attackers use to download further malware once they have infiltrated a system.
The king is dead - long live...well, who?
A lot of movement can be expected in the area of digital door openers like this, especially in 2021. At the end of January, there was an internationally coordinated strike against the operators of Emotet, which for years was dubbed the “king of malware”. Large parts of the infrastructure behind Emotet were put out of action - some of this was done with technical support from G DATA. This is likely to leave a gap in the underground market, at least in the medium term, which other groups of perpetrators are now trying to fill.
Holes with serious consequences
But it is not only well-disguised malware that opens the door to private computers or corporate networks for attackers. As every year, numerous security holes in applications and operating systems also make it easy for attackers to infiltrate IT systems. Two of the biggest are mentioned here as examples - Shitrix and Sunburst. Shitrix was one of the most dangerous vulnerabilities of the past few years. It made it possible to remotely execute arbitrary applications in Citrix ADC, and thus is classified as highly critical. In Germany alone, more than 5,000 companies were put at risk, including operators of critical infrastructure such as hospitals, energy suppliers and public authorities.
At the end of the year, government agencies and private companies discovered that their networks had been compromised. The origin of this compromise lay in network management software from network management manufacturer Solarwinds. Over a period of months, criminals kept assembling new individual components into spy software that was tightly integrated into the network management system’s development process – all without ever being noticed. The contaminated software updates raised no red flags and were installed in numerous companies worldwide. The attacks were mainly concentrated in the USA, but there were also vulnerable systems in Germany.

The fight against cyber criminals requires companies and private users to take decisive action,” says Tim Berghoff. “This is because cyber criminals are taking advantage of the current push towards digitalisation for their own purposes as well and are stepping up their attack efforts. In doing so, they are also starting to rely on automated attacks to infiltrate networks. Anyone who does not invest in IT security now will carelessly gamble away the benefits of digitalisation.
Companies must be prepared for increasingly sophisticated attacks because, with malware-as-a-service, criminals can carry out complex attacks that are difficult to fend off. What is needed here is not only up-to-date endpoint protection, but also attentive employees who can nip attack attempts in the bud by acting in a more careful manner.