G DATA experts see illegal cryptomining as a new trend
G DATA publishes malware figures for the current Top 10 greatest threats in the first half of 2018
G DATA analysts identified a total of some 2.4 million new malware strains in the first half of the year. The threat situation is currently chang-ing dramatically - nine of the ten most frequently identified malware strains of the past year were no longer to be seen in the first half of 2018. One of the trends among crooks in 2018 is “cryptomining” - the secret and illegal mining of cryptocurrencies. The experts have presented this and other discoveries in the G DATA Security Blog.

Malware for mining cryptocurrencies on Windows PCs - called Miners - are in vogue with cyber criminals, according to the latest analyses by G DATA experts. Such malware is frequently hidden on websites. In these cases, the computers of visitors to the sites are misused to generate a financial profit for the criminals.In their analysis of the first half of 2018, security experts at German IT security provider G DATA have determined that WebAssembly, a new web standard, is especially being exploited by criminals with increasing frequency. This standard is regarded as an enhancement of Javascript and provides faster execution of code. This kind of approach is ideal for cryptominers.
Current Top 10 threats for users
Not all cryptominers are classified as malware by G DATA, as it is not always apparent if the user has agreed to the mining. Hence they are sometimes categorised as malware and sometimes as potentially unwanted programs (PUPs). Among the Top 10 averted malware threats are no fewer than three miners, and four among the Top 10 averted PUP detections.
“Traditionally, malware has primarily been distributed via executable files. However, we are seeing a significant increase in web-based attacks that sometimes occur without any files at all,” says Ralf Benzmüller, Executive Speaker for G DATA Security Labs. “Attacks are also being spread via macros in documents that invite users to interact.”
Increase in fileless malware
Malware normally leaves behind traces on the computer’s hard disk. So-called fileless malware behaves differently. This malware frequently hides on primed websites and embeds itself completely in the compromised computer’s main memory. Once on the system, fileless malware can exploit the user permissions for the current user. In this way, sensitive data can be stolen or more malware subsequently downloaded. Conventional virus scanners find it too hard to detect this type of malware. However, users are comprehensively protected with modern security solutions and proactive technologies, as supplied by G DATA. G DATA security experts are currently seeing another trend with this type of malware.
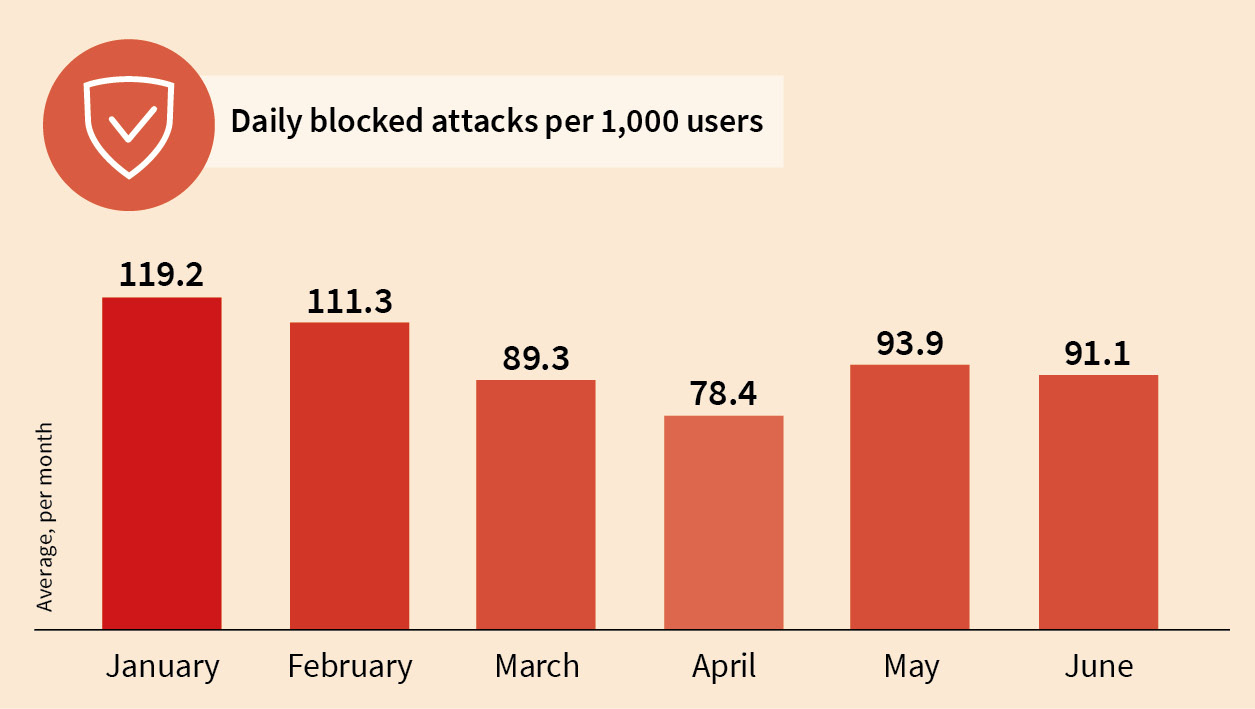
13,000 new malware samples every day
G DATA Security Labs have classified a total of 2,396,830 new samples as malware. The number of new malware types has declined slightly in the first half of 2018 compared to the previous year. On average, the analysts discovered around 9 new samples a minute.
The article "Malware figures for the first half of 2018: The danger is on the web" is available in the G DATA Security Blog.
