Malware
Malware 

04/20/2021
To patch or not to patch
Malware 

10/21/2020
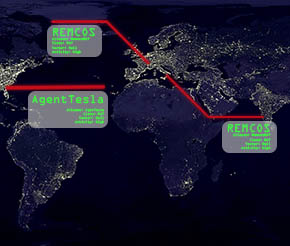
T-RAT 2.0: Malware control via smartphone
Malware 

10/09/2020
A modern Sample Exchange System
Malware 

09/01/2020
DLL Fixer leads to Cyrat Ransomware
1
 Writing Signatures for .NET Malware
Writing Signatures for .NET Malware2
 Unboxing Anubis: Exploring the Stealthy Tactics of FIN7's Latest Backdoor
Unboxing Anubis: Exploring the Stealthy Tactics of FIN7's Latest Backdoor3
 Smoked out - Emmenhtal spreads SmokeLoader malware
Smoked out - Emmenhtal spreads SmokeLoader malware4
 Unveiling AsyncRAT
Unveiling AsyncRAT5
 Exploring GenAI in Cybersecurity: Gemini for Malware Analysis
Exploring GenAI in Cybersecurity: Gemini for Malware Analysis6
 BBTok Targeting Brazil: Deobfuscating the .NET Loader with dnlib and PowerShell
BBTok Targeting Brazil: Deobfuscating the .NET Loader with dnlib and PowerShell7
 A Kernel Land Rootkit Loader for FK_Undead
A Kernel Land Rootkit Loader for FK_Undead