Since mid-February, the attention on this new form of ransomware has been enormous and it is truly a form of malware that packs a punch. Not only does Locky render files unusable on afflicted computers – it also prevents restoration of the files by deleting the shadow copies. Locky also accesses files on the network and is even capable of encrypting files shared on the network. Furthermore, the malware is aggressively distributed via various routes.
How Locky gets onto computers
Locky has been and still is often distributed via emails containing manipulated Office documents, as with the attacks by banking Trojan Dridex. The documents, which have been charged with malicious macros, download the ransomware onto the PC once the macros have been activated. Running macros is disabled by default in modern Microsoft Office products for security reasons.
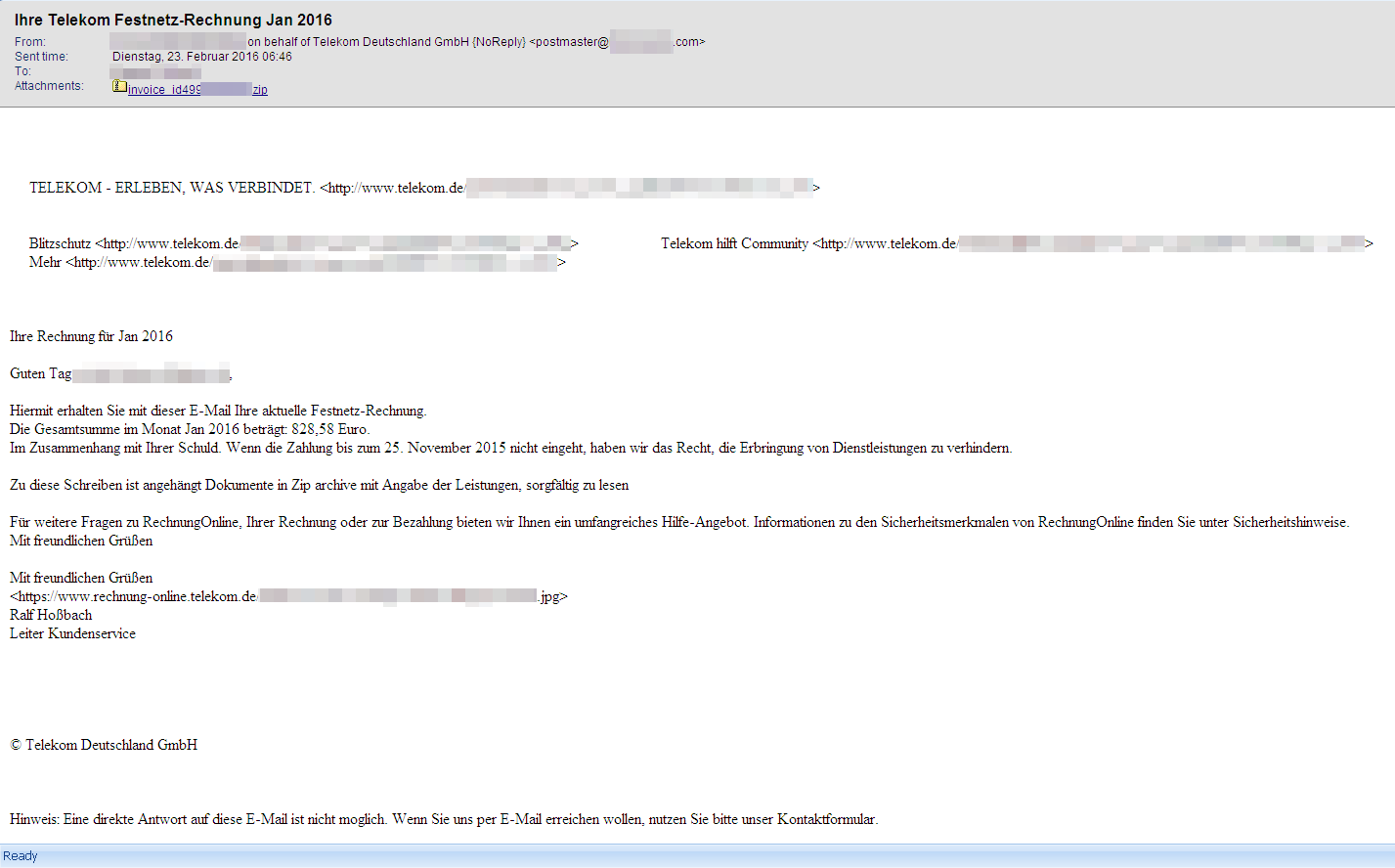
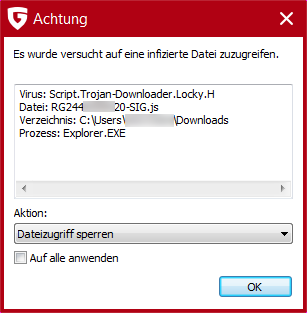
However, the latest observations indicate that the attackers have taken recourse to another strategy. Instead of using macros as active download components, they are now using JScript files as well that are also distributed via email. The .js files, which are packed in .zip containers, contact servers once they have been activated. From there, they load Locky onto the computer in order to run the malware. We have been observing this type of attack since late last year with the TeslaCrypt ransomware.
Furthermore, Locky is also distributed as a payload by the Neutrino exploit kit after an attack. Exploit kits infect computers via so-called drive-by infections. As the name indicates, this type of attack happens in passing and generally without the user realising. Manipulated websites first scour the computer's configuration for attackable applications (browser, operating system, software etc.). If a suitable hole is found, an applicable exploit that can misuse the security hole is sent to the client and run. This then enables more malware to be downloaded onto the stricken computer and executed, for example FakeAV, backdoors, spyware, ransomware etc.
Examples of current email subject lines (not exclusive)
German original:
- ATTN: Invoice J-[8 Ziffern]
- Ihre Telekom Festnetz-Rechnung Jan 2016
- Per E-Mail senden: Rechnung-[2 bis 4 Stellen]-[4 bis 6 Stellen].xls
- Rechnung Nr. 2016_[3 Ziffern]
- Rechnung 2016-[5 Ziffern]
- Rechnung Nr. [5 bis 6 Ziffern] vom 15.02.2016
Translations:
- ATTN: Invoice J-[8 digits]
- Your Telekom landline invoice Jan 2016
- Send via email: Invoice-[2 to 4 characters]-[4 to 6 characters].xls
- Invoice no. 2016_[3 digits]
- Invoice 2016-[5 digits]
- Invoice no. [5 to 6 digits] dated 15/02/2016
Files targeted by Locky
When searching for files that the ransomware can encrypt, Locky targets the following types (sorted alphabetically):
.123, .3dm, .3ds, .3g2, .3gp, .602, .7z, .aes, .ARC, .asc, .asf, .asm, .asp, .avi, .bak, .bat, .bmp, .brd, .bz2, .c, .cgm, .class, .cmd, .cpp, .crt, .cs, .csr, .CSV, .db, .dbf, .dch, .dif, .dip, .djv, .djvu, .DOC, .docb, .docm, .docx, .DOT, .dotm, .dotx, .fla, .flv, .frm, .gif, .gpg, .gz, .h, .hwp, .ibd, .jar, .java, .jpeg, .jpg, .js, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mml, .mov, .mp3, .mp4, .mpeg, .mpg, .ms11(Securitycopy), .ms11, .MYD, .MYI, .NEF, .odb, .odg, .odp, .ods, .odt, .otg, .otp, .ots, .ott, .p12, .PAQ, .pas, .pdf, .pem, .php, .pl, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .PPT, .pptm, .pptx, .psd, .qcow2, .rar, .raw, .rb, .RTF, .sch, .sh, .sldm, .sldx, .slk, .sql, .SQLITE3, .SQLITEDB, .stc, .std, .sti, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tar, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .vb, .vbs, .vdi, .vmdk, .vmx, .vob, wallet.dat, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .XLS, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .zipHowever, if the path or file name contains one of the following character strings, the file is not encrypted: tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows
Connections between banking Trojan Dridex and Locky? Who is behind it?
Besides the similar distribution methods via invoice emails, there is now apparently more evidence of a connection between the two malware families.
The way in which Dridex and Locky obfuscate the downloaders (macros) is similar, but the files that are downloaded are very different. There are some Locky samples that use the same packer as CryptoWall and TeslaCrypt. But there are other Locky samples, primarily those that access the computer via a .js file, that have been packed with the Krypton packer (v15 and v16).
Then again, more Locky samples use completely different packers and there is yet another group that is not packed at all. This variability leads us to suspect that the attacks involve the activities of multiple groups that are accessing dedicated services in the underground market.
Another connection: Our analyses showed Dridex samples which downloaded Locky ransomware into the TEMP folder and executed it.
For experts: Restrict user rights
UAC (User Account Control) is a security mechanism that prevents the execution of administrative processes and procedures that can be launched by a user with restricted access rights. This means that certain actions cannot be executed on the PC without administrator access rights. Some actions that crypto-ransomware carries out require administrator rights on the PC; if these are denied, the malware will ideally be unable to carry out all the actions needed for the attack.
For experts: Disable administrative shares
To restrict the range of the Locky Trojan to a single network, so-called administrative shares (e.g. \\hostname\C$) should be disabled.
But if it still happens:
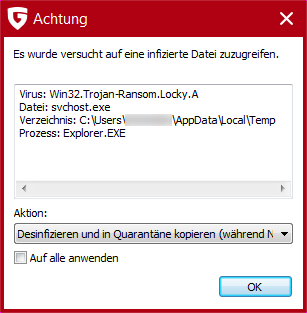
To prevent the potential distribution of the infection and/or the encryption of files across the entire network, the afflicted computer must be isolated from the network, attached storage media and the Internet immediately. Furthermore, we advise you to contact IT specialists as quickly as possible if you suspect an infection.
In the event of a Locky infection, the data filed in the registry by the malware under HKCU\Software\Locky together with the encrypted files should be stored in a secure location. It should NOT be deleted. This data is absolutely essential for being able to decrypt the afflicted files again in due course.
IT experts are managing to hack the encryption mechanisms of various ransomware families more and more often, and they can then create tools for restoring the files again. Furthermore, the work done by criminal prosecution services is repeatedly ending in success. Following successful investigations, the authorities are often gaining access to the attackers' servers so they can then provide afflicted users with the necessary keys to decrypt files.