The phishing email
The email that arrives in potential victims' inboxes is supposedly an order with an attachment called purchase-order.htm:
From: VOLTRANS TRADING CO., LTD <t[GELOESCHT]n@gmail.com>
Sent: Monday, 15 February 2016 15:00
To: Recipients <t[GELOESCHT]n@gmail.com>
Subject: Re:purchase order
Dear sir,
I sent you an email enquiry last week but i did not receive
any response from you regarding my order, so i have just sent
it again in case you did not receive it.
Please note my new purchase order list in my attached file,
and kindly send me your draft Quotation on the items.
Awaiting your reply.
Best Regards
With thanks & best regards,
Bu Emmi Pohan (Ms.) / Vice Accounting Manager
=====================================
VOLTRANS TRADING CO., LTD
No. 4/2, D2 Str., Ward 25, Binh Thanh Dist.,
Ho Chi Minh City, VIETNAM
There are several clues that expose the order as fake and potentially dangerous:
- A quick search reveals: The supposed company, VOLTRANS TRADING CO., LTD, does not exist under this name in Vietnam. There is a company that sounds similar: VOLTRANS LOGISTICS CO. LTD
- The sender's email address does not sound like an official company address and does not match the supposed sender's name: a free email address, is questionable for a company
- There is no nominated recipient for this message. The sender address is also the recipient address: <t[DELETED]n@gmail.com>
- The document attachment is an .htm file, which is somewhat unusual for an order form: purchase-order.htm – this is a very important clue. Neither HTM(L) attachments nor scripts promise anything good.
- The email contains a number of spelling mistakes. Of course, spelling mistakes can always occur, but they should be taken as a clue in forming an opinion: "Dear sir", "i did not receive" and "so i have just sent" as well as “Quotation”.
- The sign-off at the end of the email is duplicated: "Best Regards" and "With thanks & best regards", another carelessness we can notice.
The email attachment
The .htm file is identified by G DATA security solutions as Script.Trojan-Stealer.Phish.AG. This involves HTML code that has been coded using the Base64 process. This means that the contents cannot be read directly by humans; however, modern browsers are nevertheless capable of displaying the HTML document normally, as can be seen in the following screenshot:
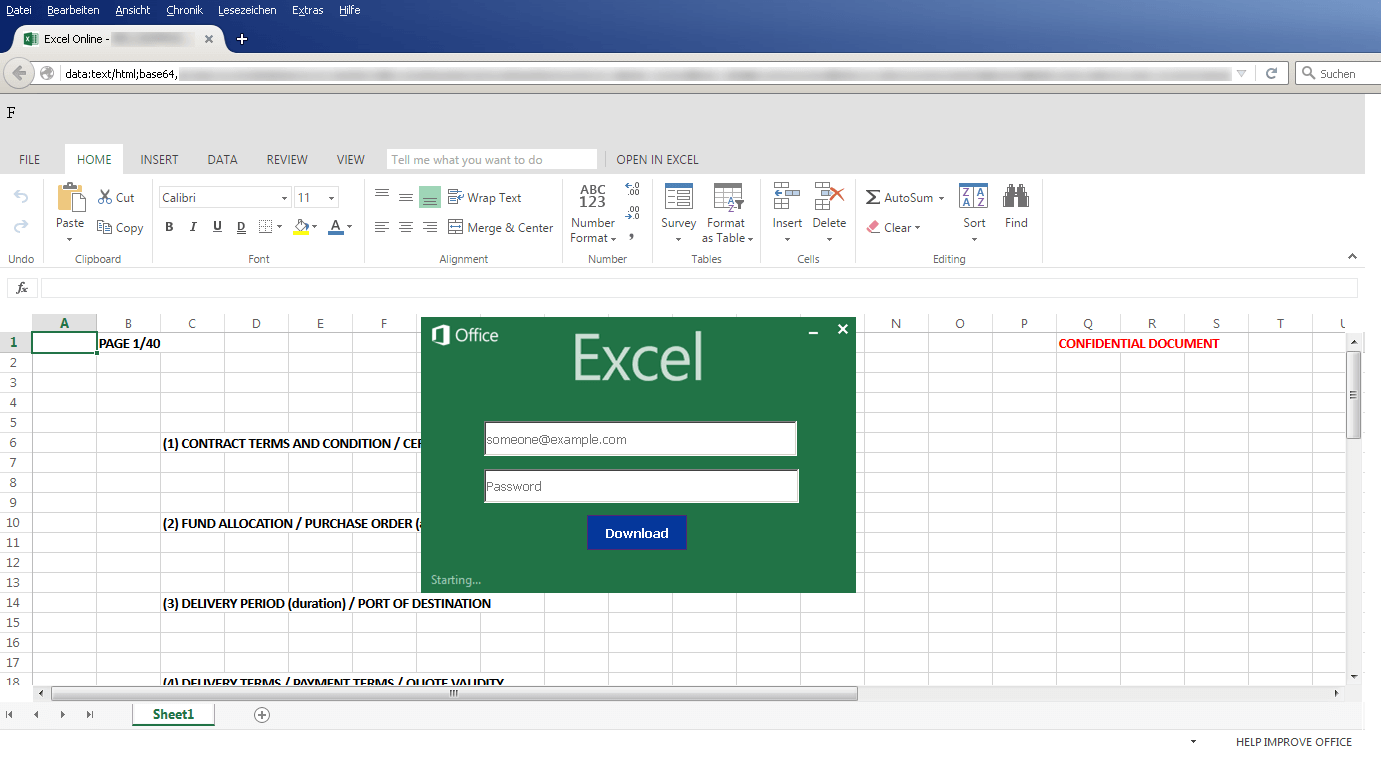
The file attempts to disguise itself as a type of Microsoft Excel online document. In the background, an Excel spreadsheet can be seen. However, this is just an image (order.png), not a spreadsheet that can be edited. This and other images are loaded from a server based in Hong Kong.
The attackers are trying to use social engineering techniques to make the potential victim even more curious about the supposed document. For example, the highlighted red text on the right hand side suggests that this is a confidential document.
But the appearance of the web page might give the user an indication that this is a fake. For example:
- The upper edge of the web page contains a mistake in the grey bar: the F here is in the wrong place. The attackers have placed it outside of the <div> segment in the HTML code.
- The logon screen does not look like it would when logging on to the Microsoft live.com platform to work on a document online. Things such as the fact that, when opened, the .htm file looks like an Excel 2013 file and not the latest product, Excel 2016, hint at this. And finally, because of the word "Starting...", we assume that this login window is a modified screenshot of the Excel 2013 start window. As it seems, the attackers are mainly aiming at users who are working with online Microsoft Office tools.
- The language in the Excel image and the login form is English. This is another warning signal for users who actually use their system and software in a different language. The user is presumably meant to enter his login data into the form to start the download. But this involves a form that uses a background image (excel.png) downloaded from the same server in Hong Kong, and from the same domain, as the previous background image.
The attackers have very probably deliberately left the precise type of data being requested vague. Potential victims might therefore enter data for a Windows account, or perhaps even the login data for their company's domain, or some other data that might seem plausible to them at that moment. The form only checks whether the email address field contains an @ sign; no other checks are made.
After clicking on "Download", the data entered – the email address and password – are sent to the same server in Hong Kong from which the images were downloaded – albeit to a different domain. This now suggests that the entire server is under the attackers’ control. After the data has been sent, a web page opens containing an error message.
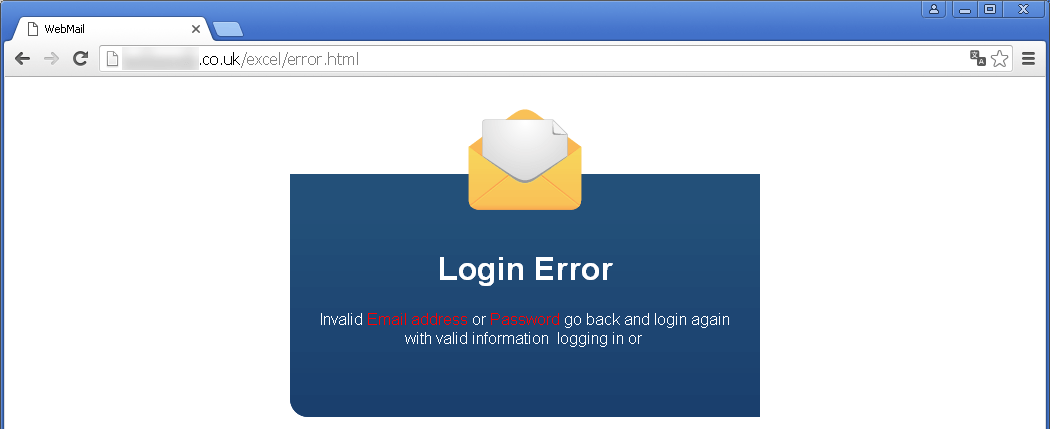
This web page is on a server in London, England. Here again, it looks like the attackers have seized the server to store their own data there, as this is a website that is actually legitimate but that now contains a subdirectory in which the attackers' data resides.
It is obvious in this error message that the attackers have copied together multiple texts without deleting duplications – as with the sign-off in the email. The last part of the message, "logging in or", does not fit the sentence. Even so, the attackers are using another social engineering technique here to encourage the user to enter data into the fake Excel document once again. As mentioned, the appearance is rather unprofessional. Presumably they also do not want to cause any more waves at this stage of the attack, as they have received at least one data set.
What can happen?
The loss of personal login data is always associated with risks!
If the attackers gain access to an email account – whether a private individual's or a company's – this can be used for sending more spam. For this reason, access to a company account is more attractive, of course, as it provides a trustworthy sender address as well as a trustworthy sender server.
This current scam, even though it does not ask for any log-in data in particular, suggests that Windows Live data are the focus. This data is valuable, because it offers access to a lot of services at the same time. Attackers can simultaneously spy on online Office documents, send emails, browse through the online files server and much more. They can gain access to a broad variety of tools and services as well as information. This can be misused as well – especially in the corporate environment.
If the data is lost in a company context, far-reaching problems can develop, such as unauthorised access to internal company data and emails. Such misuse can be carried out secretly by the attackers and, potentially, over a long period of time, e.g. until the affected user needs to reset his password due to corporate policy, or if irregularities occur in the system logs.
The data can also be sold on in underground markets by the attackers, subsequently bought by criminal buyers and misused for a wide range of activities.
Conclusion
The attackers have chosen a rather unknown scam for their attack and have used a new lure– this can be dangerous for inattentive readers. Vigilant and educated computer users can spot the scam quite easily: the email comes with a suspicious attachment, contains errors, as do the phishing page and the error message.
The HTML code suggests to us that they have copied together elements from various sources, presumably using different phishing kits, and have made mistakes when doing so as well.
Using the same server for delivering the images and collecting the phishing data is risky from the attackers' perspective. On the one hand, they are trying to cover up their tracks by visiting different domains, which would not immediately be suspicious in network data traffic, but on the other hand, with this attack, the server is a single point of failure for them.
This scam using a fake Excel document is entirely worth mentioning; however, luckily for the user, it can easily be revealed just by using your eyes.
Tips on handling such email securely
- Use a comprehensive security solution and keep it up to date!
Use email and spam protection to block tedious email.
Protect your computer against malware by using a combination of reactive and proactive technologies. - Check emails for their plausibility. Ask yourself:Have I/has my company a reason for receiving this order from abroad?
Am I the recipient of the email or is there a different address there?
What impression does the email make on me? Is the language OK or unusual in some way? - As a general rule, treat emails from unknown senders with suspicion! If an email looks very strange, here's what to do: ignore it, delete it, but under no circumstances open attachments or click on links.
- Opening file attachments harbours risks. Attachments should first be scanned with a security solution and, if necessary, deleted without being opened. If you are uncertain, send the file to G DATA SecurityLabs for investigation without opening it.
Links in emails should never be clicked on without thinking. Check the URL. Many email programs permit the actual target of the link to be seen by hovering the mouse over the visible link without actually clicking on it – the so-called mouse-over function. If you are uncertain, send the URL to G DATA SecurityLabs for investigation without clicking on it. - Emails with HTM(L) attachments should be looked at with great skepticism. The file format is commonly used for websites but not as a format to exchange information between individuals. The same is true for .js files (JavaScript).
- Never respond to spam email!
All a response does is indicate to the fraudsters that the address they wrote to is actually valid – and hence even more valuable to them. - Do not disclose any personal data – either via email or in dubious forms or on suspicious web pages!
- In a corporate environment especially, it is worth speaking to your admin manager or even the CISO if something looks suspicious to you!
