What's the Flipper Zero about?
Flipper Zero's features
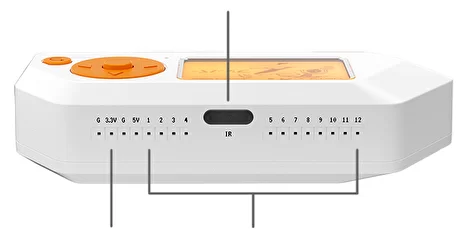
433/868 MHz Transceiver
125kHz RFID
Infrared transceiver
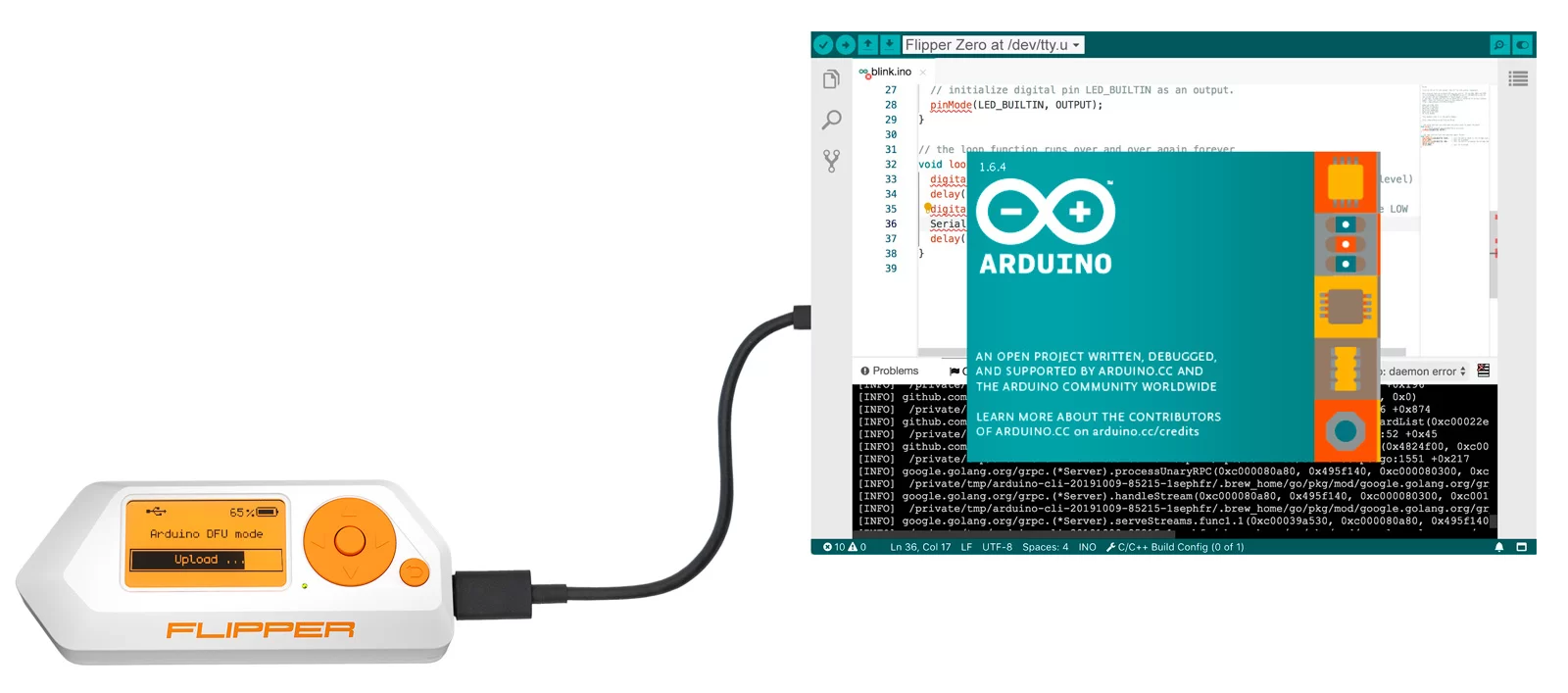
Arduino compatibility
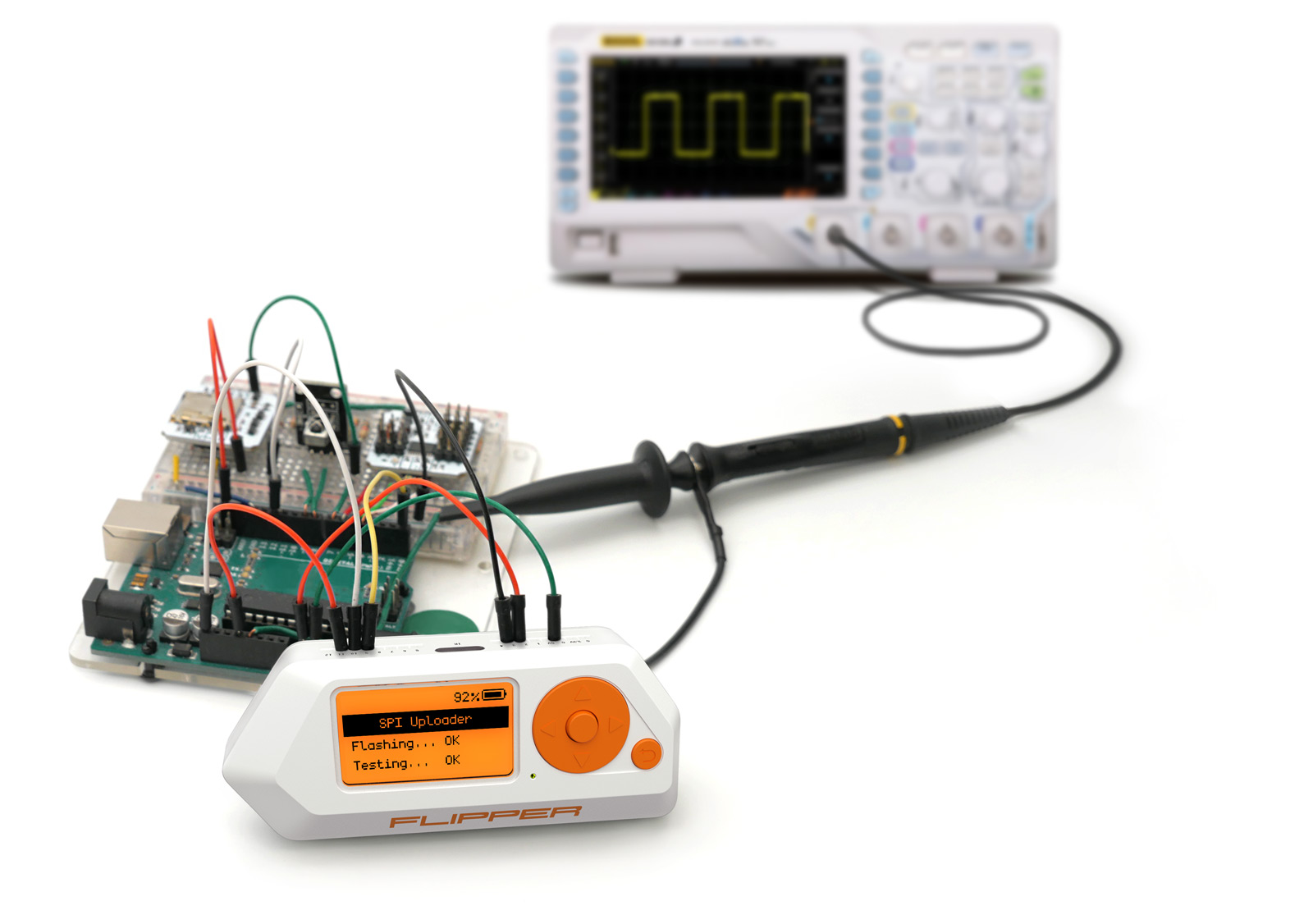
Hardware hacking
Bad USB
iButton
Flipper Zero vs. Flipper One
The Flipper Zero is a lightweight and compact version built on the STM32 microcontroller. It's able to work with basic remotes, radios and access control systems. The functionality can be expanded with programs.
The Flipper One is an advanced version with all the functions of Flipper Zero plus a seperate ARM computer running Kali Linux. This tool can be seen as a more serious tool for pentesting access control systems and networks.

How the Flipper Zero project started
Pavel Zhovner's history contains experiments with DIY hacking tools that were functional but not beautiful. He noticed that many tools he needed just weren't available. After discovering the pwnagotchi, he walked through the streets for several days in a row because he liked it so much. He realized that he wanted a device that delivers joy in tamagochi style, aesthetics of a retro game console and enough evil to hack everything around.
His friends suggested him to make a fully-fledged device with real factory production vs. yet another homebrewed DIY craft.
He documented all of this at his blog.
Flipper Zero's inventor - Pavel Zhovner
Pavel Zhovner lives in Moscow and is responsible for the local hackspace Neuron. Since his childhood, he loves to explore things around nature, technology and humans. His main focus is on networks, hardware and security though.
He tries to not use the word "Hacker". Instead, he prefers to call himself "Nerd". According to him, it's more honest. In life, he values excited people who are emotionally strong involved into things they like.
Flipper Zero is his try to make something really cool, massive and at the same time beautiful. He believes in open source software, hence the project will be completely open. He has a small team, but hopes to reach more people that would like to join the project.

Social links
If you want to stay updated about it security, be sure to follow these accounts:
RansomBleed - Personal Twitter account from Ransombleed.
G DATA CyberDefense – G DATA CyberDefense Twitter account.