Emotet is one of the most long-lasting and professional cybercrime tools of recent years. First discovered as a banking Trojan in 2014, the malware has evolved into a comprehensive go-to solution for cybercrime over the years. The malware acts as a door opener on a computer which prepares it for further infections.
"Emotet has been developed very professionally and continuously for years," says Anton Wendel, Security Engineer at G DATA Advanced Analytics. "On individual days, we discovered up to 200 new variants of Emotet. This rapid development is a way to try and hide the Malware from antivirus-solutions.” Even on quiet days, an analysis by Wendel shows at least 25 new versions of the malware. G DATA counters these new types of threats with its AI-powered solution DeepRay.
Spread via Word documents
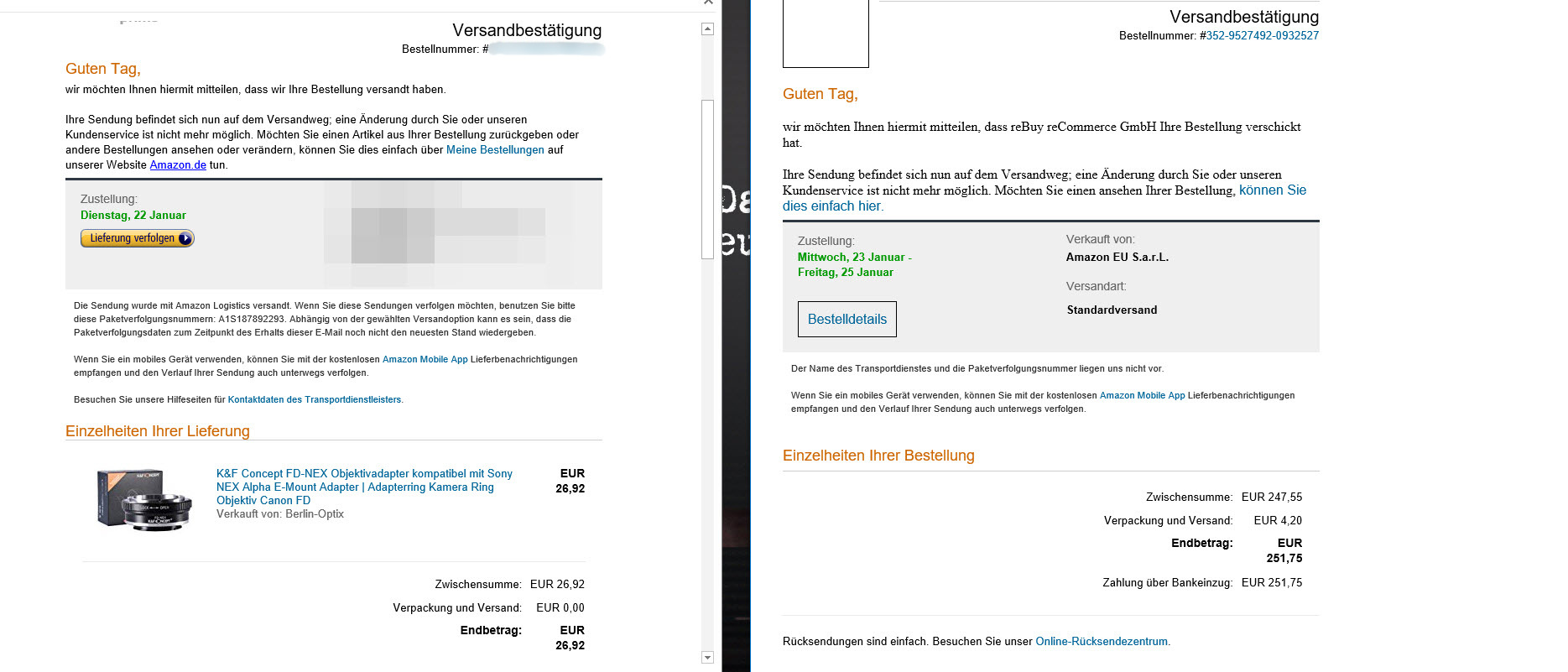
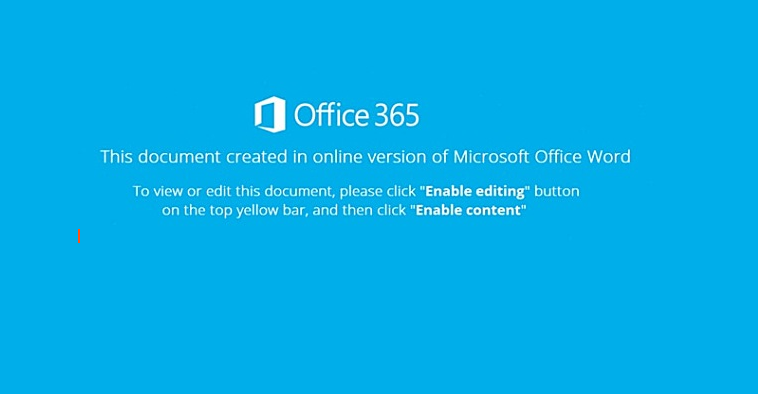
The malware is usually delivered to the victims' computers via infected e-mail attachments in Word format. The criminals are constantly trying to send new messages to victims in order to trick them into allowing the active content of the document - usually macros. The path of infection therefore always relies on the user. Unlike other malwares, Emotet is not distributed via exploit kits or the browser. The criminals always come up with new reasons why users should click on the "allow active content" button. For example, they claim that a document has been created "with an online version of Office" or point to alleged compatibility problems.
"Companies could very easily protect themselves against infection with Emotet," says Wendel. "The execution of macros can be completely disabled using a Group Policy. If macros are absolutely necessary for business operations, it is a good idea for companies to sign their own macros and only allow those signed macros to run.” For private users there is usually no need for macros at all, so they should never activate them.
What can Emotet do?
Emotet comes with very extensive espionage functions. For example, information about all processes running on the computer is transferred to the criminals. This allows conclusions to be drawn about the use of the PC - e.g. if accounting software is found to be running on it. Emotet also features a number of moduels that can be remotely activated. It should be noted, however, that not all of the functions mentioned below are executed on every infected computer. The Command-and-Control-Server decides which modules are activated.
Password stealing
By using Nirsoft's software, Emotet is also capable of copying numerous passwords stored on the computer. These include in particular the e-mail password stored in Outlook or Thunderbird as well as any passwords stored in the browser. The use of a password manager offers a better security here.
Another Emotet module is used to send spam. The makers of the malware do not distribute classic spam messages for drugs or sexual enhancers, but use the victims' resources to continue their own campaigns. Emotet is an out-of-the-box solutions for delivering said messages. As they have knowledge of the address books and also try to recreate relationship networks they can cater these messages individually. Emotet uses MAPI (Messaging Application Programming Interface) to do so.
These functions are loaded as a module in the same process as Emotet itself and are executed without saving a file to disk. This tactic makes detection more difficult. You could say that Emotet uses the concept of file-less malware for its different modules. After the work is done, the code is removed from memory to avoid scrutiny.
Emotet also has a worm component. This allows the malware to implant itself on other computers in a company network, for example, without other users having to click on an attachment and activate it. The software uses Microsoft's SMB protocol (Server Message Block) for this purpose. This protocol was also used by WannaCry to infect hundreds of thousands of systems worldwide. However, WannaCry used additional vulnerabilities in Windows to spread.
The malicious software reads the logon tokens from the local Windows memory for distribution and uses them to log on to other computers. If the user has elevated privileges - eg. administrator permissions - the attack is particularly effective. Emotet can also be configured to perform brute force attacks agains accounts using its own stored password list.
Emotet can also set up a proxy server on infected systems to better camouflage its own activities. This allows you to better hide your command and control infrastructure. In addition, any existing blocks in the IP range of their own infrastructure can be bypassed in this way.
Binaries instead of processes
In addition to the aforementioned modules, Emotet can also reload classic malware files. The criminals usually use banking Trojans like Zeus Panda, Corebot, Trickbot or Gozi. Recently, however, there have been more and more reports that Emotet also reloads Ransomware such as Ryuk and activates it after an in-depth analysis of a company. This includes gathering information which can determine whether or not further attacks are worthwhile and how high a ransom can be without breaking the victim's bank.