Production in full swing
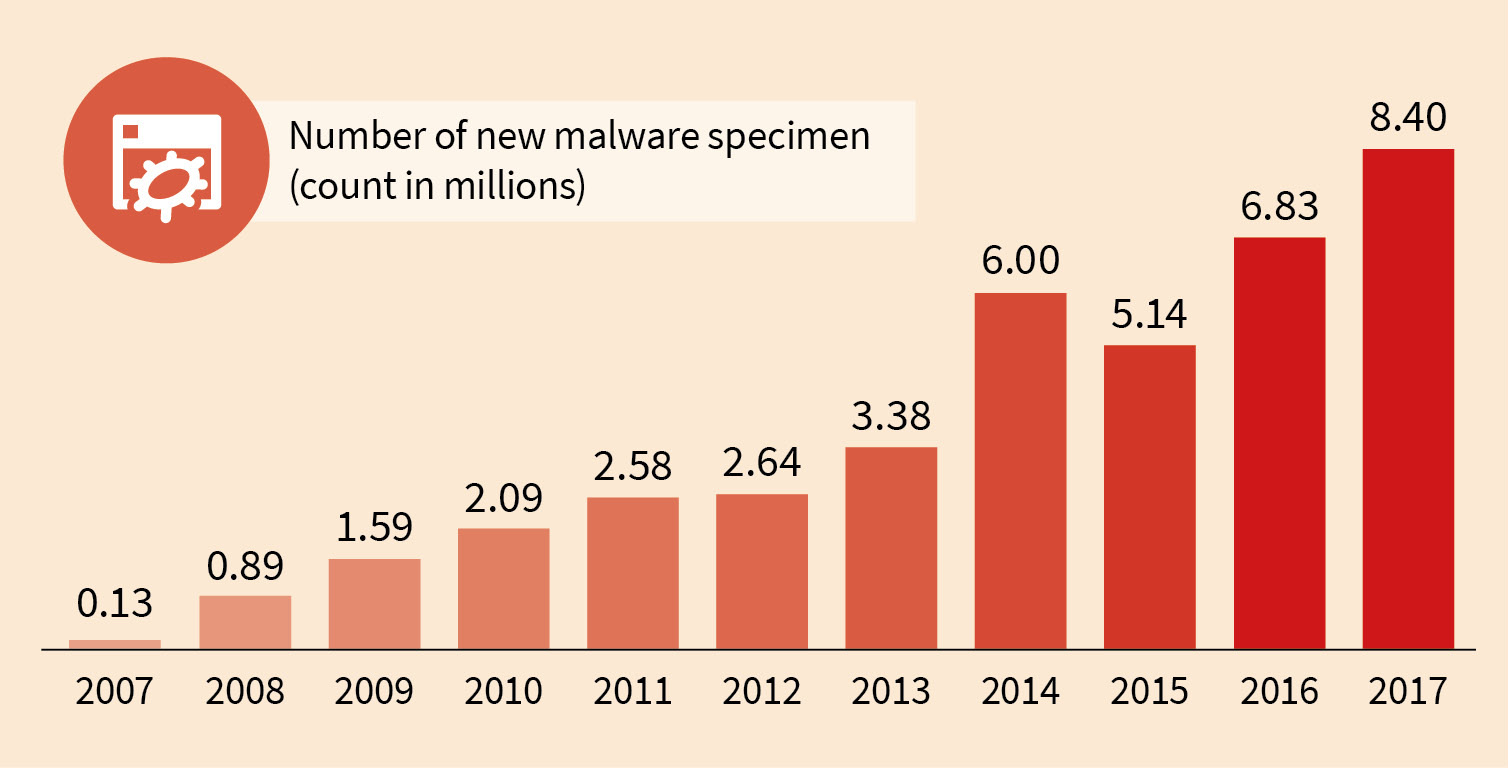
In order to get an overview of the quantitative evolution of malware, we are counting malware types as they are represented by signatures. This goes beyond counting malware files and considers only variants which share the same chunks of malicious code. Since the early days of malware the number of new versions is continously growing. Only in 2015 it was below the mark set by the record-beating year 2014. In 2017 the number of new malware increased by 22,9% over 2016 to 8,400,058. The second half of 2017 did not reach the magnitude of the first (especially that of the second quarter). The share of H2 of 2017's volume is 41.8% with a total number of 3,508,754. This is also slightly less (3%) than the same period of 2016.
Figure 1: Number of new malware specimen since 2007
In the second half of 2017 on average 795 new malware specimen were discovered per hour i.e. 13 per minute. The average for the whole year 2017 is slightly higher: 959 per hour and 16 per minute, respectively. The historic comparison with 2007 reveals that 2017 comes up with more than 63 times more malware. Although the numbers of the second half of 2017 did not gain new records, we still expect the amount of new malware to continue rising.
The bigger part of malware types are with 82.7% covered by Trojans. Their ratio stepped down 6.1%. A stronger second place is achieved by Adware (13.0%) and Potentially Unwanted Programs (PUP, 3.3%). Their share grew by 6%. These are followed by backdoors, worms, an ransomware. While ransomware was hardly measurable (<0.1%) in the first half 2017, their number increased six-fold to a share of 0.2% in the 2nd half. This might not sound overwhelmingly high. But ransomware families are the most productive in the second half of 2017.
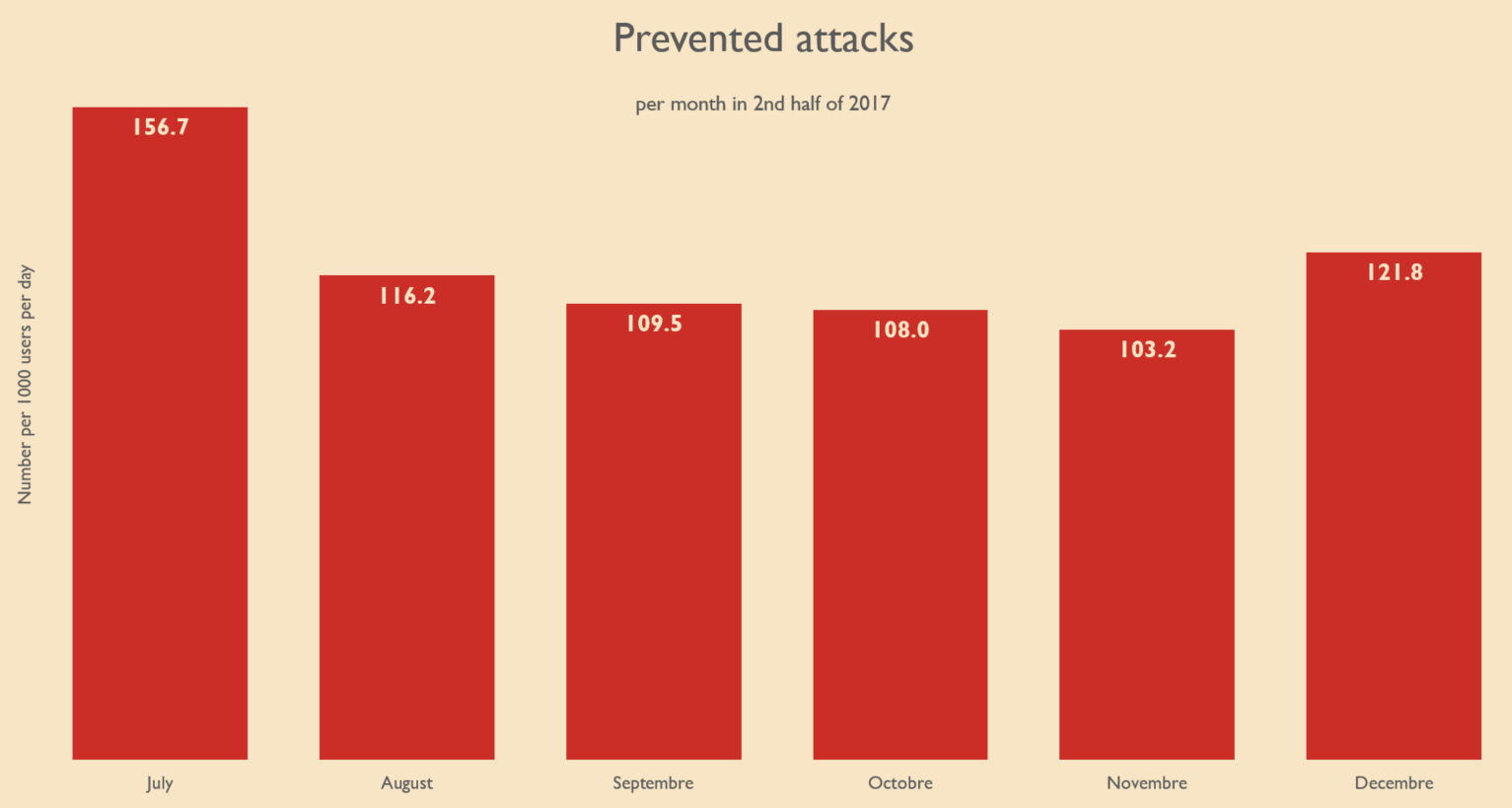
Prevented attacks in H2 2017
The number of new malware specimen tells little about the number of executed attacks. A single malware can attack thousands or even millions of computers. But most of the attacks are part of small campaigns often in far away countries. The counting is based on notifications about incidents, that we receive from users of our product, if the participate in G DATA's Malware Information Initiative (briefly MII). We are counting each file that our scanners are blocking. Since this file cannot do any harm to the system the attack is prevented. Hence we are subsequently using the term prevented attacks.
To compare the number of prevented attacks between countries and time intervals, we have normalized the numbers. We state how many attacks were prevented per day per 1000 users. The values for the second half of 2017 vary around the arithmetic mean of 119.4. I.e. on avearge every day almost every eighth user is facing a successfully prevented attack. Throughout the second half this sums up to 22 prevented attacks in 2017's second half. The number of attacks is also fluctuating by month between 103.2 and 156.7 daily attacks per 1000 users (c.f. Figure 2 below).
Malware categories
We distinguish two kinds of attacks: Malware and Potentionally Unwanted Programs (briefly PUP). Malware is executing malicious or fraudulent activities on a computer in an unauthorized way and mostly unnoticed by the user. For PUP the line is not so clear. There are tools and applications, that allow e.g. system adminstrators to manage computers and networks. In unauthorized hands these tools can be (ab)used to do harm. In many cases it is also about advertising programs and toolbars. Their questionable use might be legalized by displaying license agreements. In most cases a user is duped.
The bigger proportion of attacks in H2 2017 is accounted for by PUP (67.6%). For malware remain 32.4%. During the fourth quarter the ratio of PUP climbs up to 73.5% and the malware's drops down to 26.5%. Simply put, the ratio of PUP and malware for the second half is 2:1 rises to 3:1 for Q4. Due to this imbalance of PUP and malware, PUP is covering the majority of the Top 10 for all incidents. The subsequent differentiation between Malware and PUP allows to look into the groups separately and reveal their individual characteristics. We provide the top 10 specimen for each category together with their percantage and a short description.
About malware
| Rank | Malware Specimen | % | Description |
| 1 | Trojan.BAT.Poweliks.Gen | 13,0% | This script is part of an infection with Poweliks. As a small helper script (BATCH file) it starts another randomly named file. Poweliks is a fileless malware and acts with data stored in the registry. It commits click fraud by constantly clicking ad banners, which could lead to the execution of malicious code in the case of malvertising. |
| 2 | JS:Trojan.JS.Agent.RB | 5,6% | This is a JavaScript-based, heavily obfuscated Trojan-Downloader |
| 3 | Trojan.Html.Iframe.NA | 2,6% | Websites infected with a hidden iframe that loads a malicious binary disguised as a screensaver. |
| 4 | Gen:Variant.Graftor.369975 | 2,5% | Generic detection for Trojans that abuse folder icons to get executed. Depending on the variant it may contain functionality of worms, backdoors, or downloaders. |
| 5 | Script.Trojan.Redirector.BA | 2,1% | Redirector -as the name suggests - redirects web surfers to unwanted websites. Usually found on adult content websites |
| 6 | Exploit.Poweliks.Gen.4 | 2,1% | This exploit detects links which use Windows' HTML help function (mshta.exe) to execute JScript code stored in the registry. Poweliks is a fileless malware and acts with data stored in the registry. It commits click fraud by constantly clicking ad banners, which could lead to the execution of malicious code in the case of malvertising. |
| 7 | HTML.Trojan-Ransom.TechSupportScam.I | 1,7% | Scam websites which use some scripts to make it appear that the computer is locked on this fake warning page. Scams users into calling a fake tech support number. |
| 8 | JS:Trojan.Cryxos.1164 | 1,1% | Detection for websites that are related to Tech Support Scams. Tools offered for download are often detected as "HTML.Trojan-Ransom.TechSupportScam" |
| 9 | JS:Trojan.Cryxos.1018 | 1,1% | Detection for websites that are related to Tech Support Scams (c.f. above). |
| 10 | Win32.Worm.Autorun.A@gen | 1,0% | Worms from the autorun family become active, when removable storage drives like USB sticks, foto cameras etc. are connected to the PC. It abuses routines from the operating system to spread the worm. |
| ... | Andere | 68,2% | n/a |
Table 1: Top 10 malware specimen of prevented attacks in 2nd half of 2017
The Top10 for malware contains several scripts. Most of them are working in the context of websites. The leading malware Poweliks and the related exploits are working without accessing the filesystem. Poweliks relies on Powershell scripts, that may be safed in registry entries. It was the leader in H1 2017 and still quite strong throughout the third quarter (1st place), but dropped down to place 12 in Q4. Besides the typical downloaders (as their name suggests they download and execute files from the internet) and worms, we find on place 7 - 9 malware that is used in scam campaigns involving support hotlines. There are numerous reports about alleged Microsoft security staff (mostly from India). The websites that are covered by these malware specimen are pretending that the visiting computer is infected or badly configured - very much like former Fake AV scams. But in this case the user is asked to call a support hotline. The scammers on the other end of the line talk their victims into allowing remote access to the computer and install dubious software. They are well trained to play down notifications of AV software as false alarms. You should trust your AV's judgement in this case.
Currently, the most striking and serious threat for computers is still ransomware. We learned that they belong to the most productive malware specimen. With places 30, 163, and 194 in the Malware Top 250, they play a minor role concering the number of related attacks.
About PUP
| Rank | Potentially Unwanted Program (PUP) | % | Description |
| 1 | Application.BitCoinMiner.SX | 8.5% | BitCoinMiners utilize the computing capacity of the device, in order to mine BitCoins. In most of the cases they are delivered via websites. |
| 2 | Win32.Application.DownloadGuide.T | 5.0% | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 3 | Win32.Application.OpenCandy.G | 3.7% | This variant of OpenCandy is a Potentially Unwanted Program (PUP). It is installed alongside various legitimate freeware like DVD player, PDF reader, archiver and more, which have been bundled with the unwanted extra. The software detected as Win32.Application.OpenCandy.G is developed by SweetLabs, a company based in San Diego, USA. This PUP modifies the browser’s behavior, by changing its home page and search engine settings, it redirects the user to potentially unwanted websites and also displays pop-ups. The purpose of the modification: generate revenue by displaying advertisements. |
| 4 | Win32.Application.DownloadSponsor.R | 3.2% | DownloadSponsor.R comes as a bundled installer. The distributors take legitimate free software, bundle it with their PUP installer and distribute these bundles online for the sake of monetization. Offers and offer dialogues are downloaded dynamically from the DownloadSponsor servers. Each and every ad impression results in earnings for the distributors of the manipulated software. |
| 5 | Win32.Application.Uniblue.A | 2.2% | Uniblue offers several products which are mostly similar in functionality, basically they are registry cleaners which are supposed to speed up the computer. Trial versions are often installed via third party installers without proper user consent. A typical initial scan finds irrelevant entries that need "fixing", fixing these entries requires a paid subscription. |
| 6 | Win32.Application.DownloadSponsor.S | 2.2% | DownloadSponsor.S like the "R"-variant above take legitimate free software and bundle it with their PUP installer. |
| 7 | Application.BitCoinMiner.UB | 2.1% | BitCoinMiners utilize the computing capacity of the device, in order to mine CryptoCoins. In most of the cases they are delivered via websites. |
| 8 | Application.Alphaeon.1 | 1.9% | Alphaeon is a PUP installer using InstallCore. It tries to avoid detection by encrypting its payload. Tries to trick the user into installing various other PUP during installation. |
| 9 | Gen:Variant.Application.Bundler. DownloadGuide.24 | 1.9% | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 10 | Script.Application.FusionCore.B | 1.9% | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| ... | Others | 69.3% | n/a |
Table 2: Top 10 of Potentially Unwanted Programs for the second half of 2017
The Top 10 is dominated by typical occurances of advertisers and software-bundlers. In Q3 2017 a newcomer entered the Top 10: "Application.BitCoinMiner.SX" on rank 10. During Q4 its prevalence grew constantly and made it to the first position. Moreover it is accompanied by a similar variant on place 3. This shows that throughout the last quarter of 2017 a new kind of abuse has been established: CoinMining. When either visiting a website or when installing a bundled file, the malware is abusing the machines computing power to make money by mining crypto currencies. The most widely spread service is Coinhive, which is mining Moneros. The increased energy cost has to be paid by the victim, while the provider of this "service" is taking the money for the coins. We will look deeper into this topic shortly.
What a colorful world
There is substantial variation of the type and the number of prevented attacks in different countries. We measured most of the daily incidents per 1000 users in Israel, Norway, and Mexico. Table 3 below summarizes the countries with the highest rates of incidents for the different types of malware. The scenario differs widely. While in France PUP and Malware are on a similar level (places 5 and 6 respectively), many countries show some variation. Germany is on place 27 for both "All Attacks" and "Malware", whereas PUP is settled on place 19. Switzerland is more into trouble with Malware (place 10) as with PUP (place 23). Israel is seeing many PUP attacks, while Norway is more affected by Malware.
All Attacks
| MALWARE
| PUP
|
At last
The look at the most productive malware specimen and the number of prevented attacks reveal the business fields, methods, and structures of the cybercrime economy - at least the part that is related to a wider audience. Much money is made in the advertising environment. The new area CoinMining is trending. The case of tech support scams shows that cyber criminals are no longer concentrated on the immediate infection of a system. They rather "convince" people to call a hotline, where the fraudulent work is accomplished. The ransomware business is slowing down, but it is still actively moving. We also see malware that is related to establish and maintain botnets as a core infrastructure, send spam mails, or run denial-of-service attacks. Every country has its own conditions.
Most of the malware specimen are executable files for Windows. Many attacks though, are carried out with scripts or macros in websites, PDFs, and documents. You should be cautious when opening unknown files or websites, and run a good Anti-Virus solution that protects you from current threats.
Further information
Figure 2: Prevented attacks per month during the second half 2017
Malware report ofthe first half of 2017: https://www.gdatasoftware.com/blog/2017/07/29905-malware-zahlen-des-ersten-halbjahrs-2017