Depending on how malware is counted, the resulting assertions can differ. Every way to count has its own characteristics and inaccuracies which should be considered when deriving conclusions. If files are counted (like e.g. AV-Test does) some types of malware are overrepresented. In this case e.g. file infectors or polymorphic malware. In order to compensate for this bias, our counts are based on malware specimen as they are represented by signatures. They are based on common shellcode and are robust against minor changes. The results are presented in the next paragraph. This count doesn't tell you anything about the prevalence of malware specimen and which malware is attacking computers most often. Our telemetry data can account for this.
New malware specimen
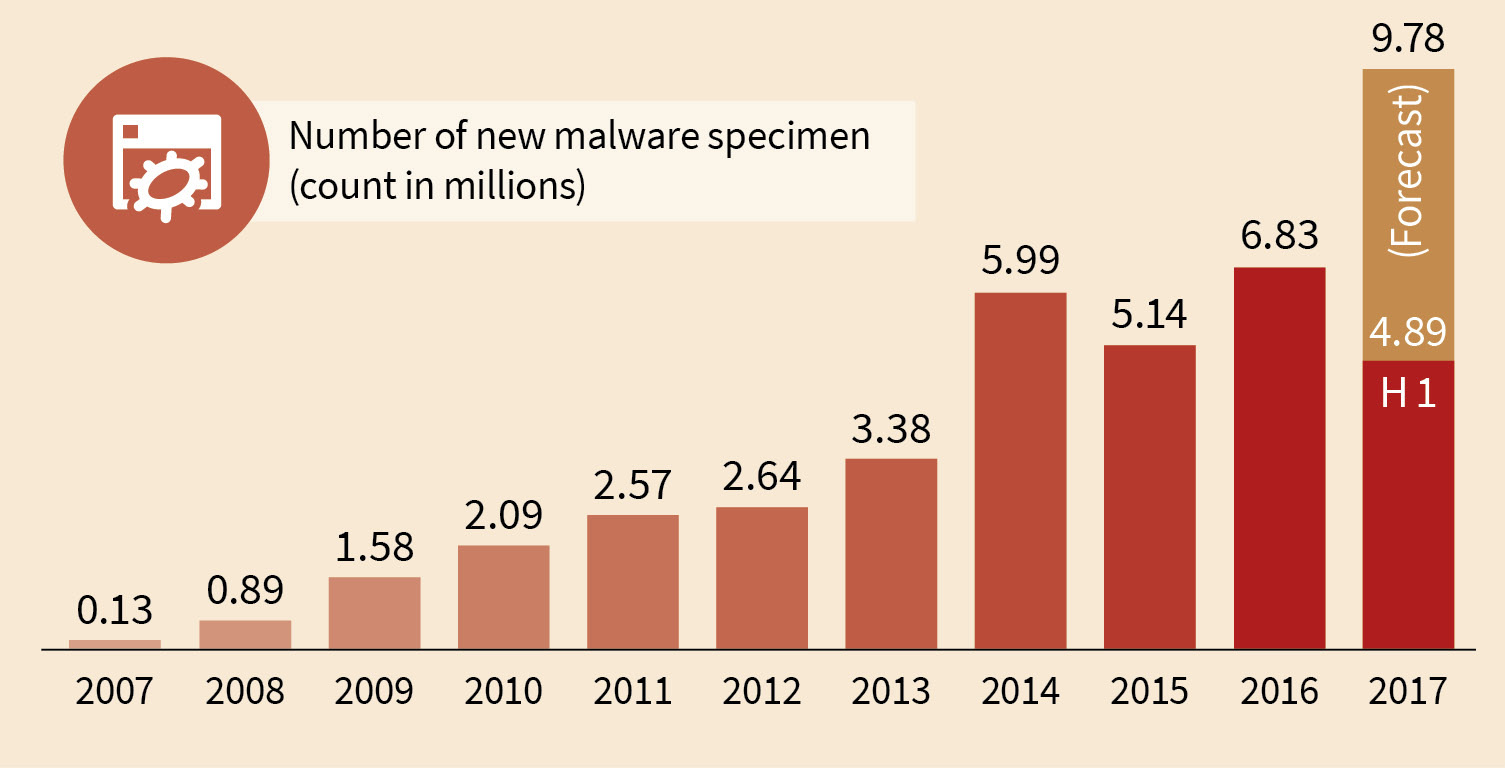
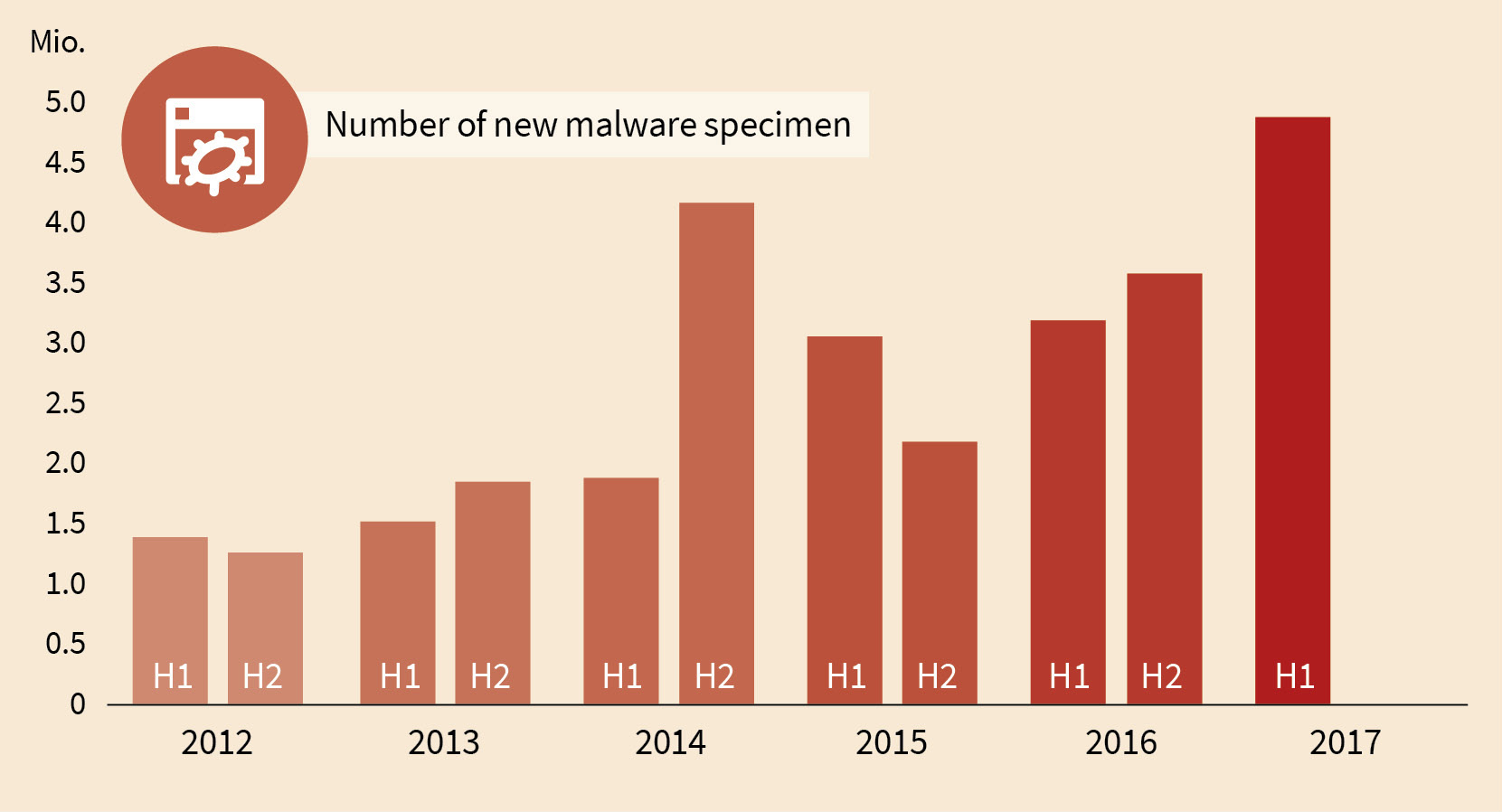
The numbers of the first quarter of 2017 gave indicated it already. The number of new malware specimen is increasing. Even after 30 years of statistics about viruses and malware this trend persists. 10 years ago we counted 133,253 new malware specimen (which was 3 times the number of the previous year). This number is with the current amount of new malware reached after 4 days. In 2012 the number rose to 20 times the amount compared to 10 years ago. And the numbers keep rising with variation but consistently throughout the last years. During the second quarter of 2017 the number of new malware specimen climbed to the 1.6-fold of about 3million. The first half year brought us 4,891,304 new malware specimen. In other words. Every day there are more than 27,000 new malware specimen. On average every 3,2 seconds. Even compared to the share of historic data this is a tremendous share. Every fifth malware specimen that we have ever seen, was created in the first half of 2017. If it goes on like this we will end up with almost 10 million new malware specimen in 2017.
The order of malware categories did not change seriously. Trojan horses make the bigger part followed by adware and potentially unwanted programs (PUP). The proportion of adware slightly decreased in relation to Q1 2017, but is still well above the level of 2016. The number of ransomware is growing, too. With a share of much less than 0.1% it is hardly measurable.
The major platform for new malware remains Windows. The next places go to scripts, Java, Android, macros, and MacOS, with a very low volume.
The number of productive malware families in the first half of 2017 is 749. This is 3.3% above the figure of H1 2016 but 16.3% below the amount of the last six months of 2016.
- On average in the first half year of 2017 there were 47.4 attacks on computers
- In 2017 the total amount of 2007 is reached within 4 days
- Every sixth signature from our current stock was created in 2017
Prevented attacks
The numbers from the last paragraph tell you how often malware is updated by malware actors and how productive certain groups are. They don't tell us how prevalent a malware is. This is covered by other data. The G DATA Malware Information Initiative allows us to count the number of attacks on computers and which malware is involved. The way we collect these numbers is different from previous reports. The resulting numbers are interesting, but unfortunately not comparable to previous data.
On average there were 47.4 attacks on computers during the first half of 2017. 78.2% of it were related to PUPs. Other malware accounted for 27.2%. Die most prevalent malware for these two groups are listed in table 1 and 2 respectively. One malware stands out here: Poweliks. It is the only malware in the top 10, but in the leading position. For years now the most prevalent malware is either adware or PUP. This also holds for this year. If you look at the number of attacks per 1000 users, you see, that PUP and adware is most frequently beat off. Poweliks is categorized as malware, but it is acting in the area of advertising. It constantly clicks on ad banners and is downloading material from advertisements. If it encounters a malicious ad, it can lead to the execution of malware (malvertising). Poweliks became notorious as a fileless, targeted attack, which is only active in memory and stores its routines in the registry. It still does so. But during infection it now utilizes files. Their detection is now leading the infection rank.
| Rank | Malware specimen | % | # per 1000 users | Description |
| 1 | Trojan.BAT.Poweliks.Gen | 25,2% | 3252 | This script is part of an infection with Poweliks. As a small helper script (BATCH file) it starts another randomly named file. Poweliks is a fileless malware and acts with data stored in the registry. It commits click fraud by constantly clicking ad banners, which could lead to the execution of malicious code in the case of malvertising. |
| 2 | JS:Trojan.JS.Agent.RB | 3,5% | 452 | This is a JavaScript-based, heavily obfuscated Trojan-Downloader |
| 3 | Exploit.Poweliks.Gen.4 | 2,9% | 379 | This exploit detects links which use Windows' HTML help function (mshta.exe) to execute JScript code stored in the registry. Poweliks is a fileless malware and acts with data stored in the registry. It commits click fraud by constantly clicking ad banners, which could lead to the execution of malicious code in the case of malvertising. |
| 4 | Win32.Trojan.Binder.A | 1,5% | 199 | Detection for a binder which is usually used to bind a malicious PE file to a clean one (e.g. add a backdoor/trojan to a clean file) |
| 5 | Gen:Variant.Binder.1 | 1,5% | 198 | Detection for a binder which is usually used to bind a malicious PE file to a clean one (e.g. add a backdoor/trojan to a clean file) |
| 6 | JS:Trojan.Cryxos.261 | 1,0% | 126 | Detection for websites that are related to Tech Support Scams. Tools offered for download are often detected as "HTML.Trojan-Ransom.TechSupportScam" |
| 7 | Script.Trojan.Redirector.BA | 0,9% | 119 | Redirector -as the name suggests - redirects web surfers to unwanted websites. Usually found on adult content websites |
| 8 | Exploit.JAVA.CVE-2013-0431.G | 0,9% | 110 | This one exploits a vulnerability in Java versions of JRE7 update 11 and before, in order to download and execute malware while visiting prepared websites. |
| 9 | Trojan.Snifula.Gen.1 | 0,7% | 89 | Snifula is a spyware, which is integrated into the processes of browsers and other software. It creates screenshots, steals passwords and banking credentials, collects cookies and certificates, and sends it to a command and control server. |
| 10 | Win32.Worm.Autorun.A@gen | 0,5% | 64 | Worms from the autorun family become active, when removable storage drives like USB sticks, foto cameras etc. are connected to the PC. It abuses routines from the operating system to spread the worm. |
| ... | Others | 61,4% | n/a | n/a |
Almost every fifth detection happens while the computer is active (On Access). 20.8% is found while a disk is scanned (On Demand), which is the first contact for malware that is downloaded via a browser.
| Rank | Potentially Unwanted Program (PUP) | % | # per 1000 users | Description |
| 1 | Win32.Application.DownloadGuide.T | 9,0% | 3118 | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 2 | Gen:Variant.Application.Bundler.DownloadGuide.24 | 7,8% | 2687 | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 3 | Script.Application.FusionCore.B | 4,0% | 1367 | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 4 | Script.Application.InstallCore.FE | 3,4% | 1186 | Bundle installer which are changed frequently to avoid detection. Installer usually does not have proper dialogs for user consent. |
| 5 | Win32.Application.Uniblue.A | 3,0% | 1028 | Uniblue offers several products which are mostly similar in functionality, basically they are registry cleaners which are supposed to speed up the computer. Trial versions are often installed via third party installers without proper user consent. A typical initial scan finds irrelevant entries that need "fixing", fixing these entries requires a paid subscription. |
| 6 | Win32.Application.DownloadSponsor.R | 2,9% | 987 | Bundle installer where offers are controlled server side. |
| 7 | Application.SearchProtect.BS | 2,4% | 817 | Browser-addon which locks the search site and startpages to its own and preventing change of these. |
| 8 | Win32.Application.FusionCore.C | 2,1% | 708 | Bundle installer which has detection for virtual machines. Offers during installation will be less aggressive if a virtual machine was detected. On a physical machine fraudulent behaviour is the usual case. |
| 9 | Gen:Adware.BrowseFox.1 | 1,9% | 665 | Browser-addon which injects advertising and gathers information on the users. Usually installed without proper user consent. |
| 10 | Script.Application.InstallCore.HL | 1,6% | 569 | Bundle installer which are changed frequently to avoid detection. Installer usually does not have proper dialogs for user consent. |
| ... | Others | 61,9% | n/a | n/a |
Obvious observations
There are some remarkable,but hardly explainable observations in the data. The number of attempted attacks on computers running Windows 8 is twice as much as the average. In the case of PUPs it is even higher. Whether some malware is reaching out for computers with Windows 8 or whether the users of Windows 8 are particularily unwary or whether there are other reasons, cannot be clarified here. This is similar with the outstanding amount of attacks on computers in USA and Mexico. It looks like the risk of being attacked is much higher there. We'll stay tuned.
No trace of ransomware
Ransomware is still a hot topic. Malware asking a ransom to release data and/or systems, create a lot of attention both at victims and in the press. Unfortunately there is nothing to see about this in the prevalence data. There are some downloaders, which are known for sometimes spreading ransomware. But the number of attacks with ransomware is very rare. It does not even appear in the top 75 of the malware. This might be attributed to the uncovered counting of other detection components like behavior blocker, exploit protection etc. (if e.g. the behavior blocker stops a malware when it is making itself persistent or if it connects to a botnet server, it doesn't know what it would have downloaded and executed). But it looks like ransomware is perceived much more dangerous than it is reflected in the numbers. But sitll. Ransomware is currently the most severe payload of malware. And it is good to be prepared with a good malware protection and a suitable backup solution.