The U.S. Department of Health and Human Services (HHS) reports, that two multi-state hospital systems are bothered with infections related to WannaCry. WannaCry was the most striking worm of the last years. A security researcher found a way to deactivate its encryption functionality. When the malware starts its activities it checks whether it can access a website with a very odd domain name, which is not registered and hence not publicly accessible. Requesting this site was probably meant to identify analysis systems of security researchers. These systems often run unconnected from the internet (in order to avoid damage to the public) but simulate responses to standard web services like websites or email. The standard response is "connection established". As WannaCry knows that the domain does not exist, it deactivated itself to hide his traces. By publicly registering the domain, the encryption functionality of WannaCry was deactivated worldwide and the damage it caused was contained.
This mechanism prevents that data on infected systems is encrypted. But the propagation part of the malware is still active. I.e. WannaCry continues to comb through the internet looking for computers with the EternalBlue vulnerability in the SMB service and infecting them if applicable. This also concerns systems in US hospitals. HHS recommends affected hospitals to restore infected machines from clean images to be sure that the malware is no longer active. In order to avoid reinfections the systems should be updated to the most recent version of the operating system. This is particularly necessary for systems running Windows 7, Windows 2003 Server, and Windows 2008 Server. They were mostly affected by WannaCry, whereas Windows XP and Windows 10 were mostly unaffected. Since next breed of malware might implement exploits for XP and Windows 10, we recommend to install the patches for Windows 10 and Windows XP, too. Cudos to Microsoft for publishing a patch for XP, although its support is abandoned. There is some malware in the vicinity of WannaCry, some harmless others indicating what might come next.
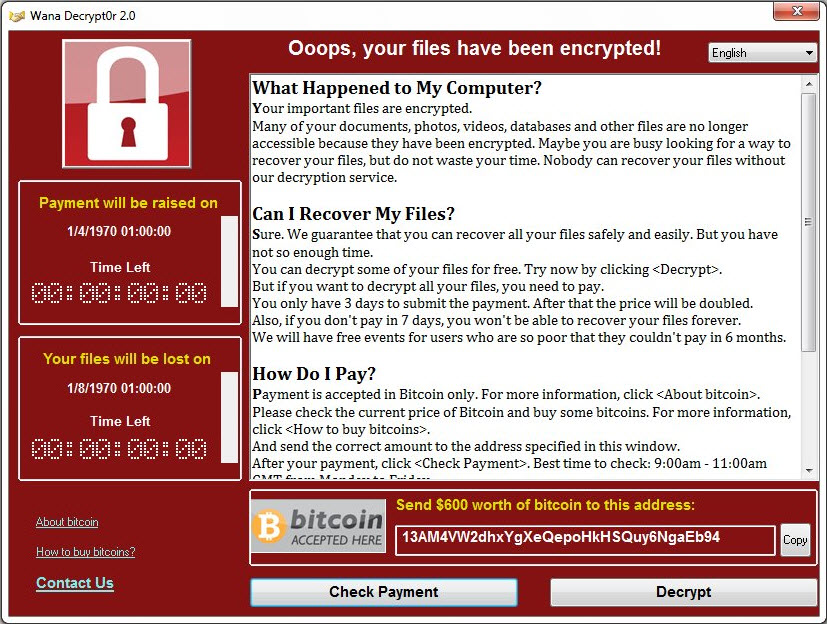
WannaBe-WannaCrys
Successful infection waves often evoke copycats. Also in the case of WannaCry there are some variants mimicking WannaCry and its lock screen. DarkoderCryptor seems to be under development, as it only encrypts files on the desktop. Aron WanaCryptor Generator creates a screen locker, which makes the computer unaccessible. It is visually close to WannaCry. The Generator does not (yet) create files. Also, WannaCrypt and Wana Decryptor incorporate different versions of the ransom screen in a WannaCry look and feel. In fact no files are encrypted and only message are displayed. Wanna Subscribe is different. It is written in Java and only has a similarity in the naming.
EternalRocks and the NSA's arsenal
WannaCry utilized two vulnerabilities from the leaked arsenal of the NSA: EternalBlue and DoublePulsar. Another malware called EternalRocks, discovered by Miroslav Stampar from the Croatian CERT, is a worm that adds five more vulnerabilities from the ShadowBroker pool: EternalChampion, EternalRomance, EternalSynergy, ArchiTouch, and SMBTouch. EternalRocks is silently acting since early May. In a first stage the computer is attacked and compromised, and it downloads some files that are needed for the second stage (e.g. a TOR browser for the communication with the Commnand and Control-server (CnC)). The second stage starts after a 24 hour break. EternalRocks then searches for other vulnerable systems und infects them if they are vulnerable. It does not load or activate any malicious payloads like ransomware or spyware. This raised some eyebrows. In 2009 and 2010 there was a similar case. Conficker created a multi-million botnet with a huge damage potential which has never been activated for seriously malicious purposes. With EternalRocks it turned out that the concerns were unfounded. The person who was running the CnC-server posted a message on the server as a reaction of the wide publicitiy. He pointed out that EternalRocks is no ransomware and claimed that he only wanted to firewall the ports that were used by the NSA tools and that he wanted to figure out how the NSA tools work. The tools that were used for the second stage are meanwhile replaced by harmless dummies.
Potential damage
So, it looks like WannaCry and ShadowBroker's NSA leaks are not causing any harm and everything is fine again. Most of the affected parties got of fairly lightly. Those who were hit harder may learn the lesson and consider it as an indicator that their IT security efforts need to be taken more seriously. But, if you look at WannaCry in a bigger scale it can be seen as a (probably last) warning. WannaCry was not well prepared. The restriction to e.g. older operating systems and complex payment process indicate that things ran out of control. The approach of EternalRocks was way more canny although it turned out harmless. I.e. there is much room for (ab)using the potential. If the attack were planned and executed in a military, strategic way, cyber terrorists and cyber saboteurs could have caused way more damage. Whether the new NSA leaks that are offered by Shadowbroker in a subscription are suited to setup similar attacks is open. But the stage is prepared, the props are built. We should be prepared, that we don't experience the performance with an end in catastrophe.
Be prepared
In enterprises software support for patch management turns out to be very useful. An efficient anti-malware product can also prevent a lot of damage. Those who didn't do it already should now patch their systems - including the old ones. But that's not enough. Malware protection is to be part of a bigger concept of IT-security and/or information security, which comprises basic protection for all publicly available services, and identifies areas where higher protection levels are needed. Once this concept is in place you should not hesitate to realize it. Next time is payback time.