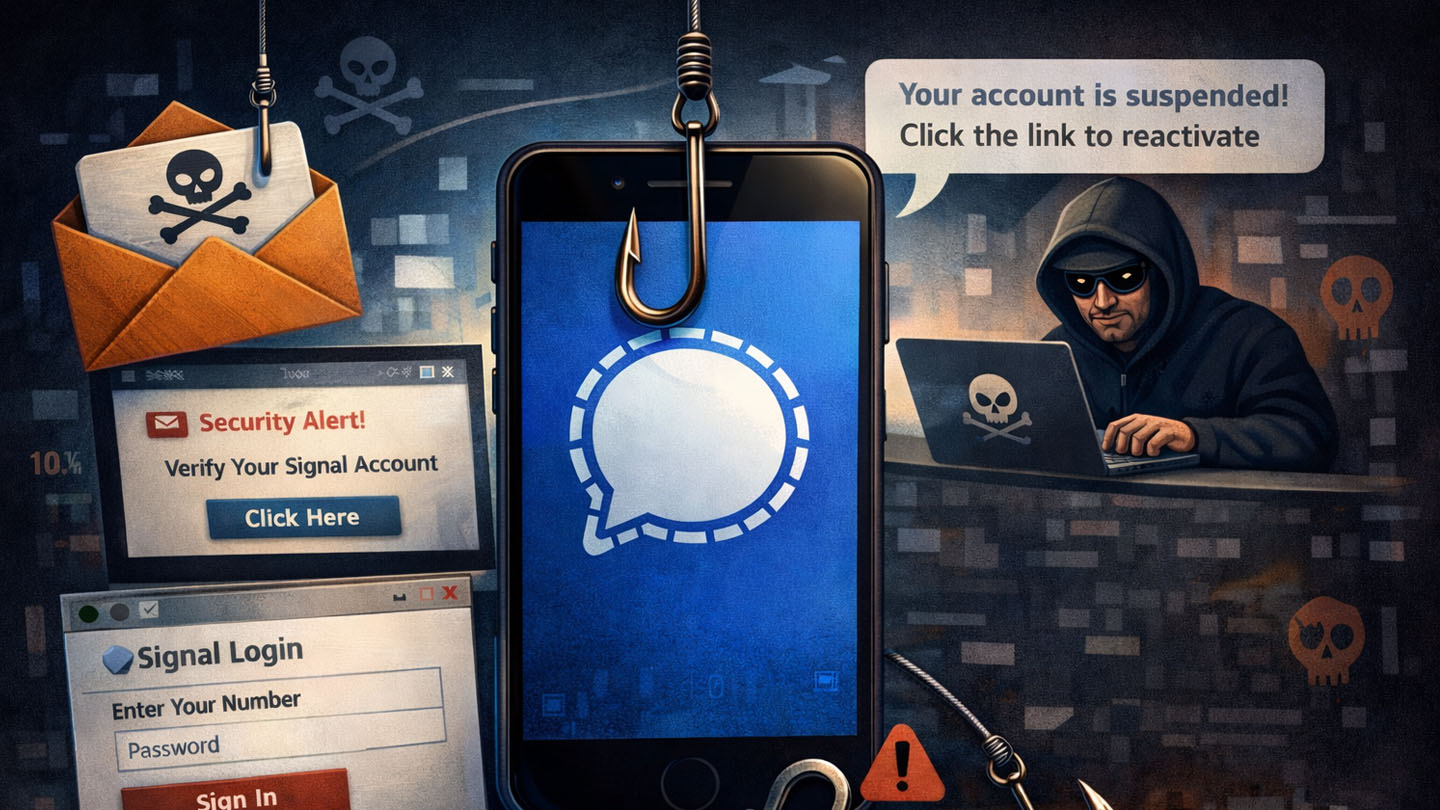
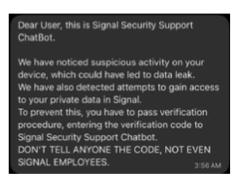
Even a messenger widely regarded as secure, such as Signal, is not immune to social engineering. This is highlighted in a recent warning issued by the German Federal Office for the Protection of the Constitution (BfV; source material in German). The perpetrators attempt either to take over the account entirely or to authorize an additional device in order to covertly read messages.
What are the attackers trying to achieve?
The objective of these suspected state-directed actors is to gain intelligence insights. Anyone who falls victim to this phishing scheme risks the loss of confidential information. It is therefore crucial to become immediately skeptical when users receive unusual messages or notice suspicious activity on their smartphone. This is especially important if Signal is being used in a business context and to share potentially confidential data.
Most effective protection: Being aware of the risks
Against the backdrop of these current attacks, it is extremely important to train employees in leadership positions accordingly and to make this information readily accessible to them. Even the best security software in the world cannot prevent social engineering attacks. Appropriate training measures, combined with clear classification of (corporate) data, can make data loss significantly more difficult. This is particularly critical in areas such as politics, journalism, and the military. If attackers gain access to confidential or classified information, this can have not only political and societal consequences, but may also place individual people in immediate danger to their lives.
To check whether or not other devices were linked to your Signal account, open the Signal app, tap on your profile ppicture and the navigate to Setting / Linked Devices.