Who isn’t familiar with them: emails in which African princes, businessmen, or heirs promise gifts of millions. The senders are usually cybercriminals targeting personal data such as login information. They skillfully exploit human behavior, relying on helpfulness, curiosity, or greed. However, these so-called phishing emails are becoming increasingly sophisticated. In addition to mass emails, attackers also target victims individually. To do this, they collect information about their target in advance and craft a tailored phishing message. A spear-phishing email of this kind — one that at first glance looked like a legitimate message from G DATA — recently landed in the inbox of an experienced security expert at G DATA. In this blog, he explains how he uncovered the attempted fraud and what could have happened in the worst-case scenario.
Could you tell us what happened?
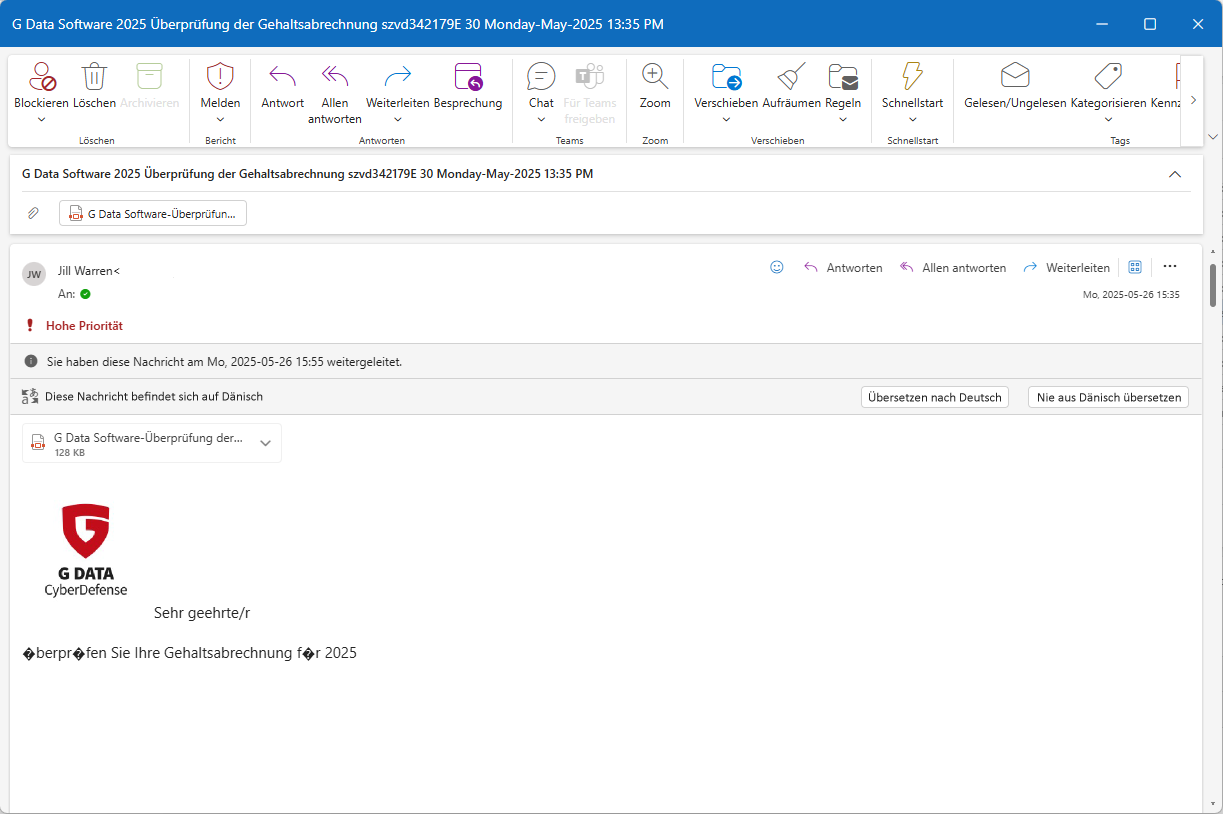
Alfred: I received an email that looked harmless at first glance. The subject line read “G DATA Software 25 Payroll Statement” — it sounded internal, confidential, important. There was also a PDF attachment. The email was marked as high priority, which is a classic pressure tactic in phishing attempts. The sender was someone named Jill Warren, whom I do not know. That also raised my suspicion.
What made you suspicious?
Alfred: At first glance, the email appeared legitimate because the G DATA logo matched the current corporate design. And I was addressed by name. But several things were immediately suspicious: The message was written in Danish, not German, causing umlauts to display incorrectly. The file name of the attachment resembled the subject line but included random characters — typically used to disguise malware. Additionally, the sender’s name and email address did not match, and it was not a G DATA domain. Finally, I had no connection to the person mentioned or the content.
How did you respond?
Alfred: I did not open the file, of course. Instead, I classified it as potential malware and forwarded it directly to our security lab via our internal ticket system for analysis. At the same time, I shared my observations in an internal chat and issued an initial warning. In Outlook, I disabled the preview pane to reduce the risk of automatic script execution. I generally treat emails with caution, even those that appear to come from trusted sources.

What did the analysis of the attachment reveal?
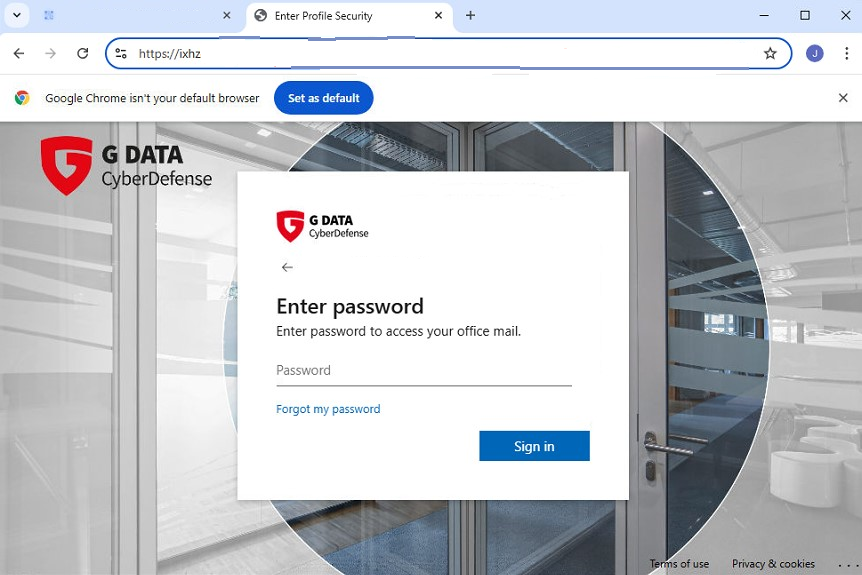
Alfred: The analysts examined both the G DATA logo and the PDF. The PDF attachment was identified as a phishing trojan, and detection for the file was added to our antivirus databases. The file contained an image with a QR code but no links. Inside the document was a message instructing me to scan the QR code with my phone's camera to view all materials. I was asked to confirm and sign the document electronically. There was also a personal note in red text stating that the material was confidential and intended only for me. All of this looked very realistic — like a legitimate G DATA file. The ISO-9001 certificate was particularly noticeable. It was probably meant to underline the credibility of the PDF. However, the QR code led to a fake Spanish login page in G DATA design, with my email address prefilled. It was an almost perfect replica of our internal login page. Had I entered my password, my login credentials would have ended up in the wrong hands — and the cybercriminals could have taken over my account. We shared these findings on the intranet and informed all colleagues so they would be prepared for this targeted spear-phishing attack.
What could have happened in the worst-case scenario?
Alfred: With my login credentials, the attackers would likely have attempted to log into the corporate network. At some other companies that don’t take security seriously, this might have succeeded. An attacker with access to the internal network could place malware, steal internal documents, take over accounts, or spy on internal communication.
Were you specifically targeted?
Alfred: Yes. The email and the PDF were clearly tailored to me — personalized, with my email prefilled, and the fake website looked very convincing. I’ve been active in the IT security field for over 30 years; my name appears in professional forums and old virus descriptions. I’m sure that for some malware developers, my name is a red flag. Anyone researching G DATA might identify me as a potential target — especially if they want access to sensitive information.
Were other colleagues targeted as well?
Alfred: That’s still unclear. I looked for signs of additional login attempts on my account — for example, from unusual IP addresses or using unusual clients — and found one suspicious login attempt. The attacker tried once to log in using an incorrect password, but the attempt failed. Our IT department found that other users had also recorded login attempts from a similar client. We are currently checking whether they also received phishing emails.
What recommendations would you give others for handling suspicious emails?
Alfred: These five tips can help protect against phishing:
- Treat all emails from unknown senders as potentially dangerous. Even if a message comes from a known sender, verify the content, context, and the sender’s email address. Is the language, style, and timing correct? Did the sender inform you ahead of time about an attachment?
- Stay alert — even with seemingly trivial emails. Social engineering combined with curiosity can be particularly insidious. “Payroll statements” or “internal information” are classic bait to attract attention.
- Do not open attachments or links you are not expecting. This also applies to seemingly legitimate PDFs or QR codes.
- Ask questions. If something feels off, speak with IT or the security department. A quick check can prevent major damage.
- Use internal reporting channels and established reporting processes. At G DATA, we have central contact points for suspicious content.
Conclusion: Mistrust is helpful
A single click on the wrong link can have serious consequences – even for experienced IT security experts. It is crucial to remain calm, check carefully and never act out of pure routine or haste. What's more, security is a team effort. By sharing your observations, you are not only protecting yourself, but also the entire company.
*Name changed