AsyncRat is a well-known malware family that has been tracked by security companies since 2019. It is a remote access trojan (RAT) designed to give cybercriminals control over compromised systems remotely. It is often distributed through malicious links or phishing campaigns, allowing attackers to execute commands, steal data, and monitor user activity stealthily. Due to its modular architecture, AsyncRat can be customized with additional features, making it a versatile tool for cyber threats.
Rewritten in Rust
The family as it is known until now has been written in C#. Interestingly, we encountered a few recent malware samples written in Rust. The configuration options, the CnC communication and the supported commands indicated that this is a variant of ‘AsyncRat’. While the language is still not extensively used for malware development, there is a growing trend of cyber criminals adopting Rust in their malware campaigns and tooling. A few reasons can be attributed to the choice which include
- The recent overall popularity of Rust
- The increased difficulty to reverse engineer binaries produced with Rust, due to lack of support for Rust in current analysis tools. Features like IDA library code recognition are not yet robust enough yet for languages like Rust.
- Cross platform malware development opportunity
Employing languages that make reverse engineering challenging is not a new trend. While C++ has been the go-to language for malware development for a long time, using a programming language to complicate reverse engineering has been a long prevalent technique. More than a decade ago, visual basic binaries containing pseudocode (VB bytecode was not officially documented by microsoft) were used by malware authors very much for the same goal. The use of obfuscated .NET binaries came a few years later. In the same vein, a bunch of newer programming languages have been used in the past few years which include Go, Nim, Node.js, Electron etc.
Functionality
The new samples do not reveal any change in functionality compared with the C# based variant. The malware has the ability to install plugins, run code from them and persist itself.
Installation
Depending on whether the malware runs with or without admin privileges, the sample either installs a scheduled task or copies itself to the temporary directory and starts itself via a batch file. Compared to the .NET variant, this step is the same.
Plugins
Plugins are installed not as binaries on disk but are stored in the registry under HKCU\Software\C2C\Plugins\ and are loaded and run dynamically by the malware. Once again, this behavior is similar to the .NET based variant. This was documented by Sonicwall in their blog in 2022.
C2 and Config
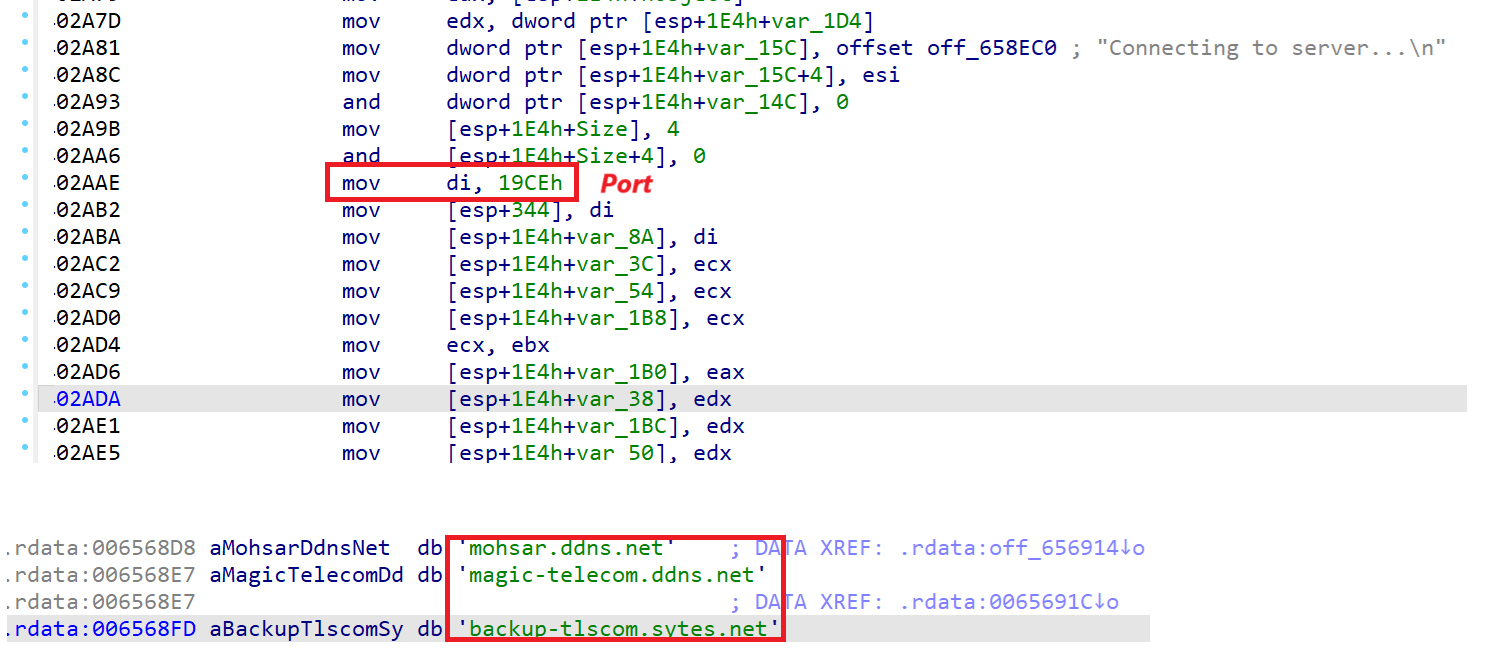
The binary holds a list of CnC servers and tries connecting in sequence based on success or failure. Communication between the client and the server happens over TLS.
The list of CnC servers is hardcoded. In the sample we analyzed three servers are used (see list of IOCS). The connection port is hardcoded as well as observed in the code.
Commands
Compared to the full-fledged .NET variants, only a few commands are implemented in the Rust variant. The set of supported commands are listed below:
- savePlugin <plugin bytes> - save a plugin that is being sent to registry
- sendPlugin <plugin-hash> - request plugin with hash to be sent
- plugin <plugin-hash> - execute a plugin identified by the hash if installed; if not, a ‘sendPlugin <plugin-hash>’ is sent to request for the plugin
- pong - sent to server after a specified time interval
Sending system information
- The malware collects and sends the following information to the server.
- HWID – A hardware id, so the server can track the client
- Operating system information
- Antivirus software installed on the system
- Whether running as admin
- Client version (1.0 in this case)
- Performance information (CPU usage)
Notes
Interestingly, the samples we analyzed incorporated debug strings. This fact hints that the Rust variant is under active development. The rudimentary set of supported commands in contrast to the C# variant also supports this hypothesis. The samples that we have observed are not recognized by other security vendors as ‘AsyncRat’ family yet.
Indicators of Compromise
eb12c198fc1b6ec79ea4b457988db4478ee6bc9aca128aa24a85b76a57add459 - Win32.Trojan.RustyAsyncRAT.B
Servers
mohsar(.)ddns(.)net
magic-telecom(.)ddns(.)net
backup-tlscom(.)sytes(.)net