G DATA released its DeepRay technology in late 2018. The rationale behind DeepRay is that cyber criminals typically use the same malware cores over and over again. In order to protect them from detection, they are encased in a kind of outer shell called a crypter or packer. The actual malware core is only unpacked in the main memory. DeepRay’s approach is to use a neural network to detect the presence of an outer shell. However, the presence of an outer shell is still not sufficient to conclude that there is an actual harmful effect. Even legitimate software sometimes uses comparable methods, for example in the context of copy protection systems. Therefore, after detecting an outer shell, DeepRay performs a deep analysis of the memory to look for known malware cores.
The main aim is to disrupt the cyber criminals’ business model. Replacing the outer shell is relatively inexpensive from the attacker's point of view. With traditional signature-based detection methods, each shell must be detected individually - an expensive process from the point of view of traditional AV providers. The attackers therefore have a clear advantage. With DeepRay, on the other hand, the attackers need to keep repeatedly changing their malware core to avoid detection - a complex and costly process for attackers. Advantage G DATA!
After more than nine months it is time to take stock: has DeepRay proven itself in practice?
Trends and tendencies
Many publications in the field of malware analysis talk of an exponential growth in malware. However, security researchers at G DATA have long suspected that the number of simultaneously active families remains relatively constant; the number of new malware families is increasing slightly. Only the total number of malware files is increasing exorbitantly. This diagram illustrates the theory:
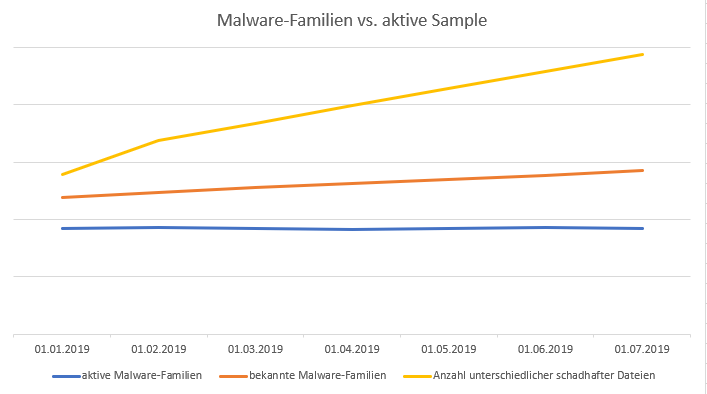
In fact, after six months of DeepRay being released, it can be said that, while our analysts are aware of and track over 200 individual families, only about 80 of these families are active at any one time. This confirms the thesis put forth by our researchers in the run-up to the development. Only a few of these families are then reported on in mainstream media, including individual ransomware families such as GandCrab or Trojans such as Emotet.
Mode of action split into several elements
In total, as the last line of defence in the protection technology in G DATA products, DeepRay has successfully prevented almost 2000 different new types of attack in the first half of 2019. The mode of action of our proactive protection components is split into several elements. At the endpoint on which the proactive protection component is triggered, it reliably provides protection against further damage to the infrastructure of the affected user. However, the malware's harmful features are then transferred to the G DATA Cloud, where the protective effectiveness is mapped. This means that, after an average of eight minutes, the malware cannot be executed on any other clients because a Cloud update is already available that successfully prevents execution. For this reason, DeepRay protection is usually only triggered with one customer; subsequent infections are reliably prevented via the Cloud and also via our G DATA CloseGap engine. For comparison, any requests directed towards other protection components outnumber those made by DeepRay by a factor of 75.
On any one day, approximately 5% of our malware requests in the G DATA SecurityCloud are based on a DeepRay detection. Even if we subsequently transfer our detections to both the Cloud and engine signatures, the Cloud is of course much faster due to its rapid availability, and it prevents execution, especially with fast-moving malware campaigns, while signature-based engines first have to wait for an update from us and the customer.