Stressful preparation
After a three and a half hour drive, me and my colleague Stefan arrive at the conference hotel in Luxembourg. It is 11:30 am. We pick up our conference badges and head straight left - it is hard to miss the the table occupied by the FluxFingers team. Amidst a collection of Club Mate and water bottles we can see the team members working away at their computers. They are applying the final touches to the systems that await the players. The G DATA sponsored FluxFingers CTF team of the Ruhr University in Bochum organizes the annual CTF competition at hack.lu. Over several years, the hack.lu CTF has developed into a well-respected staple of the scene. Nobody here got any sleep last night. There are still a few bumps in the road that need smoothing out. "We usually have our own system that runs all the challenges - but unfortunately, that machine went belly-up two weeks ago and we were forced to get a few new servers lined up to migrate the entire CTF", explains Tobias. "Thankfully, though, the Computer Incident Response Center in Luxembourg (CIRCL) who also sponsors hack.lu has really helped us out by letting us use some of their machines. There's still lots to do and we're starting in half an hour." We take the hint and let the guys continue their work to have a look around. Across the hall, the Chaos Computer Club Luxembourg has a large booth. Over on the other side, a bug bounty company has set up shop. The place is packed with 3D printers, blinking lights and numerous DIY projects. I for one, feel right at home.
Some familiar faces appear in the crowd, some of which I had seen two weeks prior during the Virus Bulletin conference in London. We walk over and chat a little.
Countdown
A few minutes before noon we head back to the FluxFingers table. „Two minutes!“ shouts one of the guys at the far end of the table. The notebook display of Horst shows a process monitor. "Those are the load indicators for the challenge systems" he says, pointing to the upper left corner of the screen. "We hope they do not move all the way to the right at 12:00. That would be bad." I am told that at 12:00 sharp, the firewalls will go down and the players can log in to tackle the 30 challenges the team has brought. I want to know if right after the start, team members need to have a constant watchful eye on all the systems. "No, not really."
What is a CTF, anyway?
„CTF“ stands for „Capture the Flag“. Each party has got a flag that must be conquered by one of the other teams. It is a popular game mode in lots of computer games, where the objective is to conquer a virtual flag from an adversary's camp and bring it to one's own camp. The objective of a hacking CTF is very similar: a team is required to "conquer" a certain password or a sequence of characters. This may be hidden in a file, an encrypted text or a website. Only those who have the skills and the brains to achieve this will win what on a CTF is called a "challenge".
„We have automated almost everything. There's a panel that constantly shows us the status of every single challenge components. A script is constantly checking whether everything is working as it should. Unless something goes off the rails, we don't have to touch anything. If there's a hiccup anywhere in the system, all of us get a push notification to our phones. We are also having a constant eye on our chat window, so if anything starts to go wrong we're right on top of whatever it is. An indicator for each component will appear in green when everything is working as intended. Two of the indicators just turned red. It is 12:02. As if on cue, a message appears in the general chat room "I have login issues!". One line below that, another player asks how to change the team name. The verdict at this point: "Apart from really minor things, everything is running smoothly."
Calculating scores
Teams can earn points for solving a challenge successfully. The more difficult a challenge is, the more points are there to earn. The team with the most points is the winner. Sometimes, though, the race is so tight that a time factor must be added. This is called "first blood": the team that solves a particular challenge first will earn more points for solving the challenge than the teams who hand in their flag later.
What do CTF players have to bring to the table?
Overall, the mood is pretty relaxed. Many people stand around at the tables and are chatting away. Droves of open notebooks or frantic typing are nowhere to be seen. A CTF like this one is not comparable to a LAN party. Players are joining in from all over the world. Overall, more than 700 teams have registered, hailing from countries like India, Taiwan, Vietnam, the USA, the UK - it does not get more international than this. "Having a team register locally is relatively rare", I am told. A look at the roster shows only eight of them flagged as being "local".
The operating system you use does not really matter that much. Just use whatever you are comfortable with, whether it is Windows, Linux or MacOS.
The community is pretty international and teams join from all over the globe. Still, there is no "World CTF association", or any other associations of that kind. There are also no selection games, semi, or quarter finals in the classical sense. There are no national or international leagues like a "Champions League" or a World Cup. Almost, anyway. Some CTFs are seen as a sort of "unofficial world championship", such as the one that takes places at DefCon in Las Vegas. I ask Carl: "Can anyone take part in a CTF?" The answer: "Sure, basically anyone is welcome to join. Usually it is a whole team that registers for a CTF, though, as rarely any one person has all the required skills for all the challenges during a CTF. For some events you need to qualify first because they are at a pretty high level to begin with. That's not something a complete beginner should be trying. You can qualify if you have, for example, won another specific CTF prior to that."
"Is there something like a list of items that I need to have? Like certain programs or operating syetems like Kali Linux?", I ask. "No, not really. Just bring whatever you feel comfortable with. It doesn't matter if you are a Windows, Linux or Mac user. Many use some flavor of Linux. But then, one of the best CTF players in the world is running Windows. In the end it comes down to what you can handle best. Tools...it depends on what you want to do, but a decent text editor is a good start." When asking what skills I need to take part, one of the team members cracks a joke and says "Skills? All of them, of course!". But then Tobias interrupts the giggle: "Seriously, though - everyone has their own area of expertise, from web security to cryptography, reverse engineering or forensics. This category (author's note: he is referring to forensics) is not that popular, because the challenges in that area really take a long time and often involve a lot of guesswork."
What kinds of challenges are there?
Generally speaking, there are five types of challenges: binary exploit, Reverse Engineering, Web Exploit, Cryptography and Forensics. In exploiting, the objective is to collect the flag that is hidden in a specific application and that can only be retrieved be finding a weakness and taking over the system. In Crypto challenges you get a string of characters that holds your flag and that you need to decipher. In forensics, players sometimes get a memory dump of a system where they need to locate their flag. This category requires a particularly big amount of patience and a certain tolerance towards frustration because those memory dumps can be several GB in size.
One of the beginner challenges of this is called "ShinyCode". The material consists of a 10 minute long video which shows a Fluxfingers logo that flashes in different colors. The accompanying text only hints at a very old technique being used which is based on short and long signals.
Striking a balance

The competition is now well underway. After making sure we don't get in the way of anything important, we wanted to know what the rules are for a CTF like this. "There are no real rules per se. This would kind of defeat the purpose of a hacking contest. We want people to come up with good and creative solutions to our challenges. That way there's even the possibility for us to learn something. We don't tell anyone how to tackle a challenge", Carl explains. There are, however, a few things that are very much frowned upon during a CTF and that must be kept in mind when developing a challenge: Nobody should have an advantage over other players because they have a specific tool. Having an excellent and expensive commercial tool is nice and all, but the purpose of a CTF is not to determine who has the best tools or the most "oomph" when it comes to raw computing power. That would be terminally boring". Speaking of computing power: Another factor that needs to be taken into consideration is what hardware is accessible to a player. Some players use their laptop while they are waiting at the airport. When it comes to computing power, a roughly two year old laptop computer should be able to handle a challenge without any issues." This makes perfect sense - if, for instance, the challenge requires you to decrypt a piece of text, one way of going about this would be to either bring the most powerful hardware money can buy or simply to purchase some computing time on a cloud platform. Automating logins in order to try out passwords are not really an issue: "We added a couple of mechanisms that deliberately slow you down, so nobody is getting any funny ideas. The use of automated tools is unfair towards other players, because those tend to eat up a lot of ressources on our end, like computing power and bandwidth. And it is, again, boring."
Boredom during a challenge is something that needs to be avoided at all cost. If the challenges are too easy, it frustrates the more experienced players. If, on the other hand, a challenge is either "unsolvable" during the time frame set by the CTF or if the solution requires a completely convoluted and illogical approach, then that's a sign of bad challenge design. This is both frustrating for newcomers and it scares players away." It is important to make sure that every player finds something to do. Therefore there have to be challenges that are more easy and that appeal to beginners. "This year, we brought 30 challenges. Nine of them are still unsolved." A glance at the watch - it is just before midnight. Even at this time, the entire FluxFingers crew is right there at the table.
A CTF isn't about who has the best tools. That would be boring.
Sleep is somewhat important
Meanwhile, Tobias and Simon have left to to get a couple of hours of shut-eye. They plan on taking the night shift. It is important to make sure that the players have a point of contact at all times, because this CTF is a global event. Looking at the score board shows that the Asian teams are starting to call it a night, while the European teams are just getting started. "It's early in the morning for our Asian players, so some of them just use that opportunity to catch some Z's". There is no real "shift plan" that the teams stick to. Everyone works at their own pace - and it is easy to lose track of time. It is rare for players to power through the entire CTF without sleep. This only happens at CTFs that last for 24 hours. "Sleep is somewhat important. When you get tired, you lose focus and start making mistakes. You're not doing yourself and your team a favor by forcing yourself to stay awake", says Carl. "Mate or coffee can help a little, but there's only so much it can do and you need to know when to call it for the day". I learn that there are some CTFs that go over 72 hours or longer. During those CTFs it is not uncommon for the firewalls to be enabled again every now and then and forcing a break. The players can use that time to rest and the organizers can make repairs and adjustments where needed.
Sleep is somewhat important - otherwise you lose focus and start making mistakes.
Enforcing some rules
The second day is here. When arriving at the FluxFingers table, the mood is tense. Niklas explains: "There are some teams that have started using automated tools on some of our web challenges. You know, tools like Nessus. Of course that's not what teams are supposed to do and we need to step in here.". The way in which a team tackles a challenge also tells something about how difficult it is: "Usually, teams only start using automated tools when they are either running out of time or out of ideas. But their use of such tools drains resources on our side that other teams need." When asked what you can do about this, Paul shrugs his shoulders and says "There's not much you can do about this. Sure, you can call the team out and even put an IP ban in place if nothing helps. But if you ban, say, the hotel's IP address, you've slammed the door in the face of every team playing locally. So that is not an option. I think we'll post a note in our IRC channel and on the public CTF portal, too".
When a challenge is proving too difficult, there is no other way that to drop a few hints that point players in the right direction. I learn that it can be incrediubly frustrating for players when they are forced to poke around completely in the dark for hours on end. Meanwhile, the number of yet unsolved challenges has shrunken down to three. At this point, the CTF has been running for 26 hours.
We do not want to frustrate players by having them poke around in the dark for hours on end. If things are too difficult, we also give hints that point them in the right direction.
Unsolved challenges
The rest of the day passes in relative calm. Stefan and I use the time to attend some of the conference talks. The next morning, Simon and Tobias look pretty tired when I drop by shortly after 7:00 a.m. "We'll do another two hours maybe, then we'll be relieved and we can get some sleep."
Only one challenge has not been solved yet: the "Contiki-NG" challenge. "ContikiNG is an IoT framework that is used by many manufacturers. I've provided a version that has a security flaw in the network stack", the author of the challenge, "Sceptic", tells me. "The flaw exists in the current version, but a patch is about to be released for that. It isn't easy to find, though. But I think I've dropped enough hints." I then retreat to my hotel room to work on my weekly YouTube video.
The final stretch
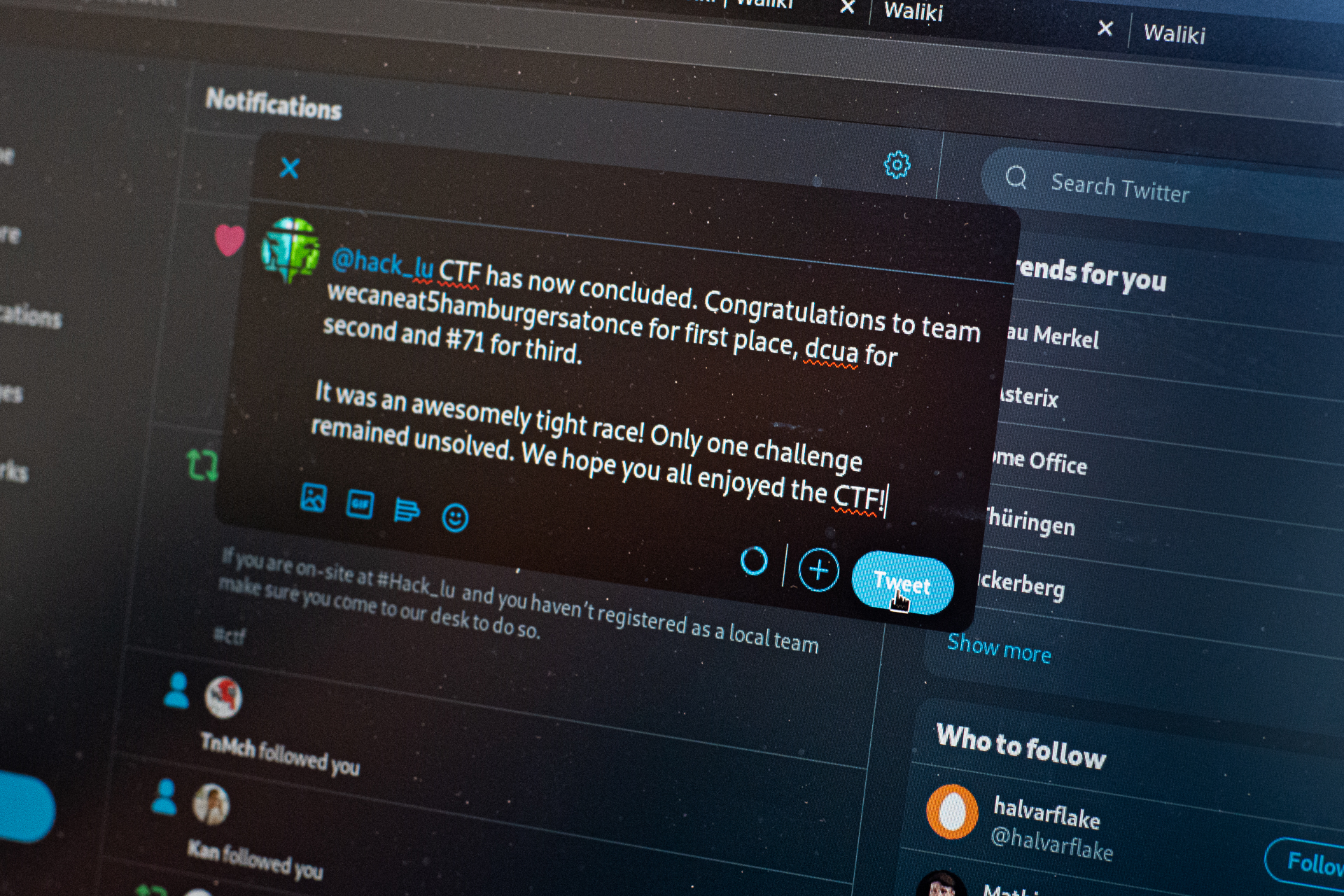
Shortly before 12 noon I am back downstairs. There has been quite a bit of movement on the score board. A South Korean team by the name of „wecaneat5hamburgersatonce“ is leading the field, closely followed by "dcua" from the Ukraine and "#71" aus Israel. At this point, it is a head-to-head race. When the checkered flag drops, the "burger" team has come in first and won the CTF. A Twitter post congratulates the winners. The FluxFinger team then spends the next hours gathering feedback and keeping track of the tweet storm. Players and teams thank the FluxFingers team for the challenges. They are full of praise - one of the players writes "Solving your TreesForFuture challenge has been quite a journey, but it was worth it".
After the last talk of the conference there is a short award ceremony for the best teams who registered as "local": "Flat Network Society", "teambi0s" from India and "We0wnY0u" from TU Vienna. All those who played locally and accept prizes on behalf of their teams, are members of larger teams who played from home. As mentioned previously: a CTF like this is a global event.
As for Stefan and myself: after three days of conference, many interesting discussions (and a lot of banter) as well as little sleep and loads of Mate we are ready to head home. The FluxFingers team will stay another night to break down their camp, to relax - and maybe catch up on some sleep.