When looking at some of the „old hands“ of the ransomware scene, you will quickly realize that a lot of development work and quality assurance has gone into them. Those often very elaborate pieces of malware deliberately make the life of an analyst more difficult by either leaving fals trails or leading analysts down one dead end after another.
In the case of “Crypt888” you might argue that it is not even a ransomware in the classical sense of the term, as no money is demanded for decrypting the data.
Subscribers desperately wanted
Not only high-profile YouTube channels always strive for a larger number of subscribers. Using ransomware to achieve this goal, however, is an idea that not many have had so far.
Someone used the AutoIT scripting framework to create a ransomware which seems to have exactly this in mind. If a machine is infected, the user – supposedly – is instructed to subscribe to a particular YouTube channel. A screenshot is to be submitted as proof via email.
That’s a solid F. Sorry.
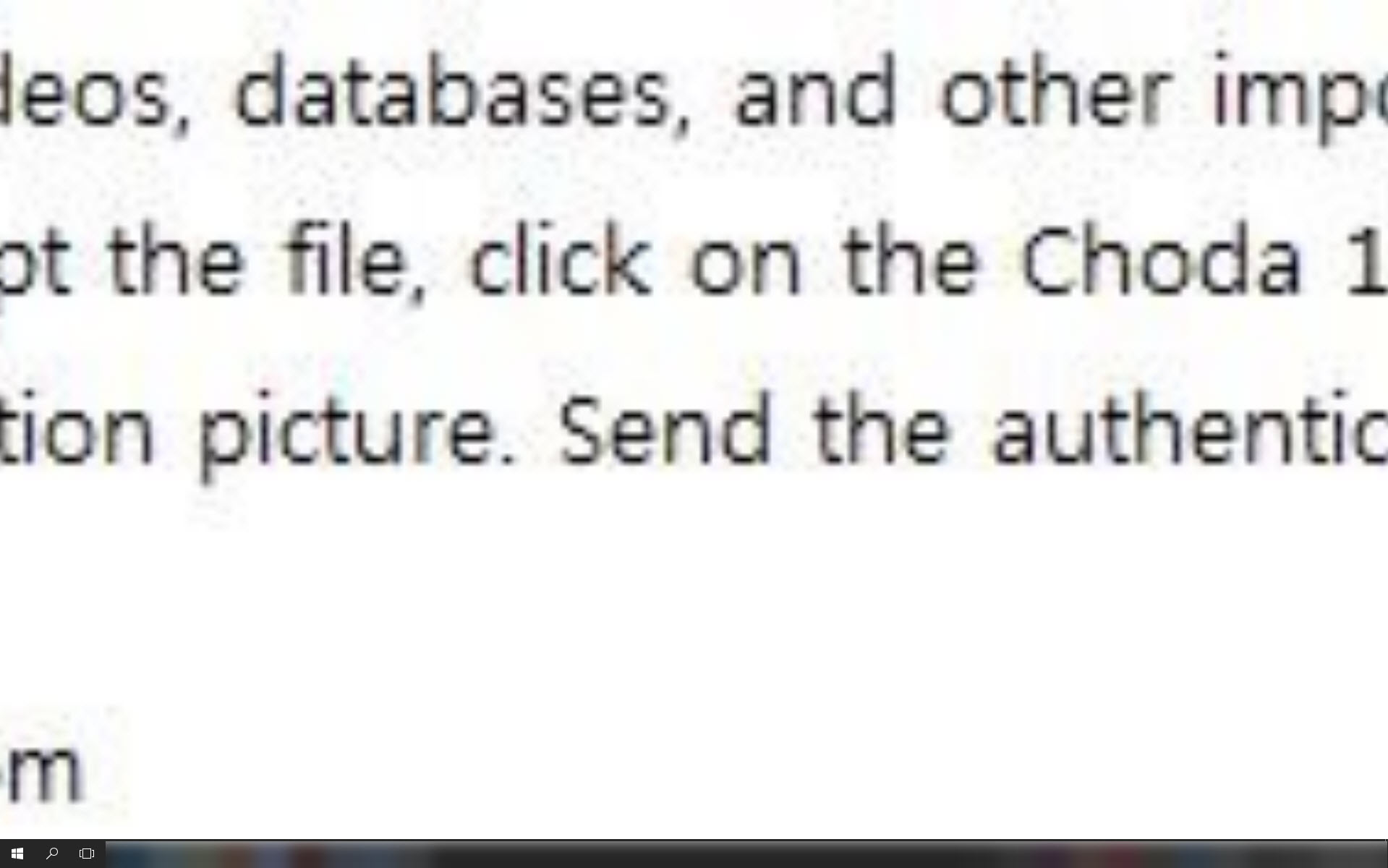
When ransomware instructs its victims on how to make a payment, the instructions are always formulated very clearly and in a way that is easy to understand, unlike in the case of Crypt888. For one, the instructions are put on screen in a way that partly obscures the ransom note, and even if the text was visible in full, the demands are not immediately obvious.
When doing a web search on some of the terms from the ransom note, you come across one particular YouTube channel. Let’s just say that successful ransomware looks different.
Even the encryption of the files has been implemented in a way that is best described as shoddy and haphazard. According to our analyst, the developer has at best spent a few hours cobbling his ransomware together.