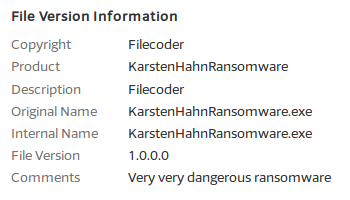
Malware researchers do collaborate quite extensively in fighting malware in general ransomware in particular. Two of them who go by the names Elise and MalwareHunterTeam, have discovered several samples on VirusTotal that use the HiddenTear ransomware source code. These samples do not try to disguise the fact that they contain malware code. Their file properties comment describes them as "Very very dangerous ransomware".
One of the samples is called "KarstenHahnRansomware.exe" which might lead anuninformed user to believe the ransomware was written by Karsten Hahn. This is definitely not the case. Karsten Hahn is G DATA's member in a very vivid ransomware analysis community. Naming the file after him could be an attempt to put Anti-Malware researchers into a bad light.
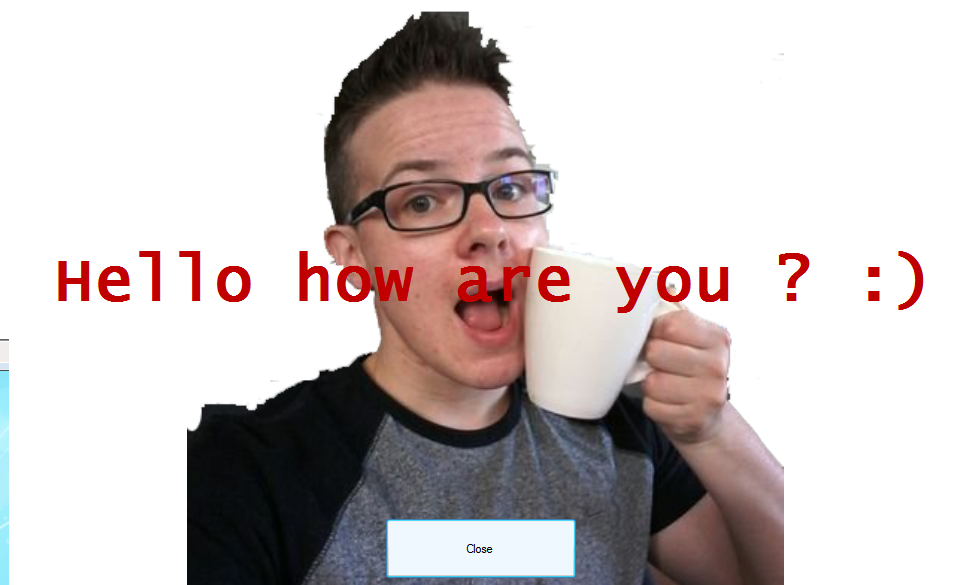
Actually the malicious code is never called and the file doesn't do any harm to the system. It is just used to attract attention. The samples pop up a screen with a modified picture from Karsten Hahn's Twitter profile. It contains a "Close" button and the message "Hello how are you ? :)". Pressing the close button will simply close the window and no further harm is done to the system.
This is not the first time that malware researchers were mentioned in ransomware samples. E.g., Fabian Wosar from Emsisoft and MalwareHunterTeam have been featured in ransomware before with the result that victims sometimes believe they are responsible for the infection. This rather unusual way to approach a researcher can be easily misinterpreted.
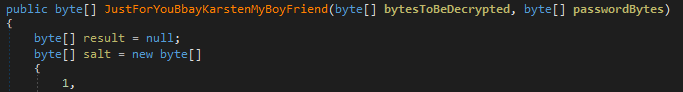
Looking deeper into the source code reveals a personal "greeting" to Karsten. One of the classes in the source code handling the encryption is named "JustForYouBbayKarstenMyBoyFriend".
We detect the sample as "MSIL.Trojan-Ransom.Cryptear.KH". The Cryptear Family is of course quite large, but the "KH" version is of course not a coincidence.
Karsten Hahn is sending back the message: "I am fine, thanks."
Technical detail for fellow researchers:
SHA256: 93a843d28f7e7b38579a6a410594d360a993f610c59437e742c9256c57de659d (MSIL.Trojan-Ransom.Cryptear.KH)