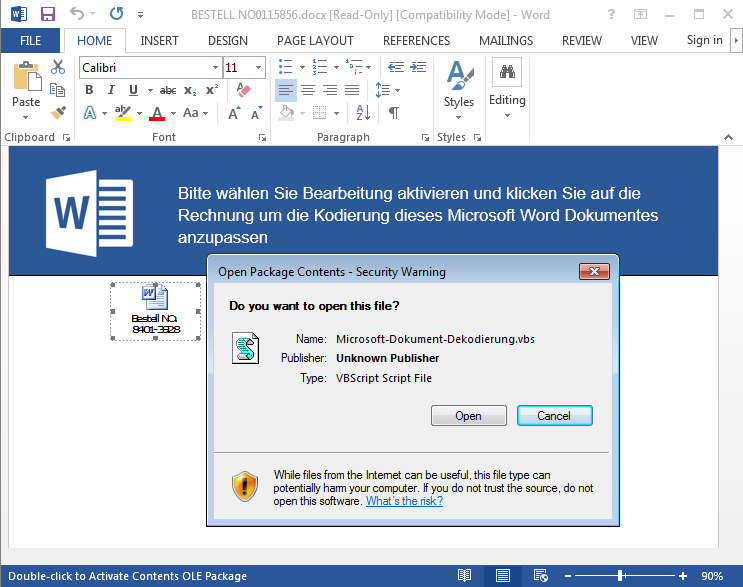
How do victims know they are infected?
The bad news is: once an infection is present on an unprotected machine, it is nearly impossible to detect by just looking at the contents of the screen. The screen output is manipulated in a very clever way so it blends in perfectly with the look and feel of a particular banking or payment website. Users could be lured into making a donation to a charity or tricked into returning a payment which they have received in error – some even add more pressure by hinting at criminal investigations for money laundering by the “German Finance Police” (there is no such thing in Germany, at least not under this name). In addition to grabbing data entered on the website and modifying what the user gets to see, ZeuS Panda also manipulated some security settings and alarms inside the browser, which might otherwise give away its presence.
There is some good news, too, though: there are technologies which can still detect an infection even if a malware signature is not present, such as G DATA BankGuard.
What makes Panda special
While there are many malicious applications out there that try to evade detection as well as analysis. ZeuS Panda goes to exceptional lengths regarding the latter: It checks for indicators that it runs in a VM – including VMWare, VirtualBox, Wine or any HyperV-type environment. Many analysts run malware samples in virtual environments, therefore this approach is a first attempt at thwarting analysis. In addition, many tools which are used by analysts are also checked for: ProcMon, Regshot, Sandboxie, Wireshark, IDA and the SoftICE debugger. If the presence of any of those programs is detected, the malware will not run. Other malicious programs mostly rely on a basic check which only looks for Things like VMWare and OpenBox; the functions are often just copied&pasted from others. On top of all this, different packers are used to create the malicious file, all of which need to be sifted through manually. You get the idea: the makers of ZeuS Panda made their creation a very tough nut to crack.
There are other pieces of malware out there that employ similar techniques but in many cases the implementation is shoddy or the malicious program contains errors, which make it unable to function in the first place. I have seen some examples of this first-hand in the past: when peeling back the various layers of protection, it turns out that the URL, which the malware was supposed to contact contained a typing error, which left the entire malware dead in the water.
Not so with ZeuS Panda: it keeps collecting data until it is told otherwise. Unless the Command and Control (C2) server is taken out, the collected data piles up on the system until it can be offloaded to a different C2 server.
A malicious “Swiss Army Knife” from Eastern Europe
What makes Panda so exceptional other than the evasion mechanisms and quality of the workmanship that went into it, is its versatility. While ZeuS Panda is first and foremost a Banking Trojan, it is also capable of stealing other types of data from a system. This also includes clipboard contents (i.e. what you have copied in a file in order to paste it somewhere else – password managers often make use of the clipboard when transferring data from the password manager to an application / website), making screen shots and providing a full-on backdoor into a system using VNC. The latter would be the same as if you had someone sitting behind you and looking over your shoulder 24/7.
Which function is activated depends on the configuration of the malware, which is downloaded automatically at regular intervals. So in effect, ZeuS Panda can morph from being a banking Trojan to being a spyware & remote control for a PC in the course of a few minutes, at the sole discretion of the attacker.
There are very clear indications as to ZeuS Panda’s origin: the malware will not run if it detects that the system is based either in Russia, The Ukraine, Belarus or Kazakhstan.
Detailed Analysis
If you are interested in the technical details of ZeuS Panda, you can download the analysis report from the website of G DATA Advanced Analytics and read the blog posts on it on their website (Part 1 and Part 2 ).