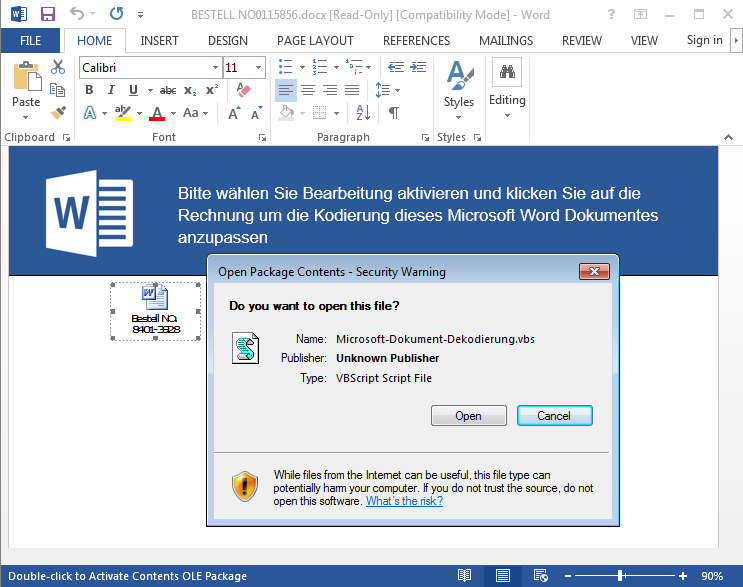
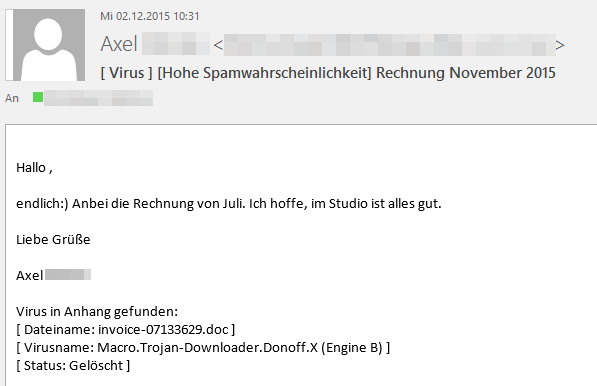
About a week ago first reports appeared about an unfixed vulnerability in Microsoft Office, which has been actively exploited by malware. A RTF-file is infecting the computer as soon as it is opened in Word. Millions of emails with malicious attachments were allegedly spammed via the Necurs botnet. Opening the attached file installs a variant of Dridex a notorious banking trojan. This is at least what can be read in the press and in forums.
Weak signals
According to our telemetry the picture looks different, at least in German-speaking countries. We have neither seen any significant rise in the activities of exploits nor in banking trojan's. It might be that the spam filter has kept away the malicious files from the computers or the campaign that has been reported about was prevalent in other geographic regions.
Counter measures
This does not necessarily stay this way. So you should be prepared. Your AV is able to block these kinds of attacks with behavior blockers or exploit protection technologies. The attack itself works only if "Protected View" is disabled. So you could change the settings of Word, that Outlook attachments are opened in protected view. This gives you one more opportunity to block the attack. The best option is of course to secure the system.
The current Microsoft update closes this critical vulnerability in Windows, and several others e.g. in Internet Explorer, Edge, .NET, Windows, and Office. Because there is malware in the wild that is actively exploiting these flaws, it is advised to update before cyber criminals grab your PC.
Overview
ID | Short description | Rating | Affected Software |
|---|---|---|---|
MS16-037 | Cumulative Security Update for Internet Explorer (3148531) Remote code execution with the current user's privileges if a web page is opened | Critical Remote Code Execution | Microsoft Windows, Internet Explorer |
MS16-038 | Cumulative Security Update for Microsoft Edge (3148532) Remote code execution with the current user's privileges if a web page is opened | Critical Remote Code Execution | Microsoft Windows, Microsoft Edge |
MS16-039 | Security Update for Microsoft-Grafikkomponente (3148522) Opening a specially crafted document or visiting website with embedded Open Type Fonts leads to remote code execution | Critical Remote Code Execution | Microsoft Windows, Microsoft .NET Framework, Microsoft Office, Skype for Business, Microsoft Lync. |
MS16-040 | Security Update for Microsoft XML Core Services (3148541) Remote code execution when clicking a crafted Link e.g. in emails or on web sites. | Critical Remote Code Execution | Microsoft Windows |
MS16-041 | Security Update for .NET Framework (3148789) remote code execution if an attacker with access to the local system executes a malicious application | Important Remote Code Execution | Microsoft Windows, Microsoft .NET Framework |
MS16-042 | Security Update for Microsoft Office (3148775) Remote code execution with current user's privileges, when opening an Office file. | Critical Remote Code Execution | Microsoft Office, Microsoft Office Services, and Web Apps |
MS16-044 | Security Update for Windows OLE (3146706) Remote execution of code, if user input is not properly validated in Windows OLE. A successful exploit requires the user to open a prepared application first. | Important Remote Code Execution | Microsoft Windows |
MS16-045 | Security Update for Windows Hyper-V (3143118) Running specially crafted code on a guest system can lead to arbitrary code execution on the host system (unless the Hyper-V role is enabled). | Important Remote Code Execution | Microsoft Windows |
| MS16-046 | Security Update for sekundären Anmeldedienst (3148538) Arbitrary code execution as administrator | Important Elevation of Privilege | Microsoft Windows |
MS16-047 | Security Update for SAM- und LSAD-Remoteprotokolle (3148527) Gain elevated privileges if an attacker launches a man-in-the-middle (MiTM) attack. An attacker could then force a downgrade of the authentication level of the SAM and LSAD channels and impersonate an authenticated user | Important Elevation of Privilege | Microsoft Windows |
| MS16-048 | Security Update for CSRSS (3148528) Bypassing security features, if an attacker logs on to a target system and runs a specially crafted application | Important Security Feature Bypass | Microsoft Windows |
MS16-049 | Security Update for HTTP.sys (3148795) Denial-of-Service-Angriff, a specially crafted HTTP packet is send to a target system | Important Denial of Service | Microsoft Windows |
| MS16-050 | Security Update for Adobe Flash Player (3154132) Resolvers vulnerabilities when installing Adobe Flash Player | Critical Remote Code Execution | Microsoft Windows, Adobe Flash Player |