What is it about?
The current investigation explicitly deals with suspicious offers of very popular brand sunglasses – especially Ray-Ban and Oakley. Glasses by these two brands are particularly popular with spammers and, in keeping with the season, offers are sprouting up like mushrooms. In most of these cases, the ads reach computer users completely unintentionally and in some cases the mere use of Facebook even turns users into advertising vehicles without their consent.
Spam has undoubtedly been on the IT security experts' minds for a long time. In the past, computer users were only bothered by undesired emails but now cyber criminals have discovered newly created digital channels as well. Let's take a look at the different channels through which we have received advertising for suspicious sunglasses shops:
The Classic: Email
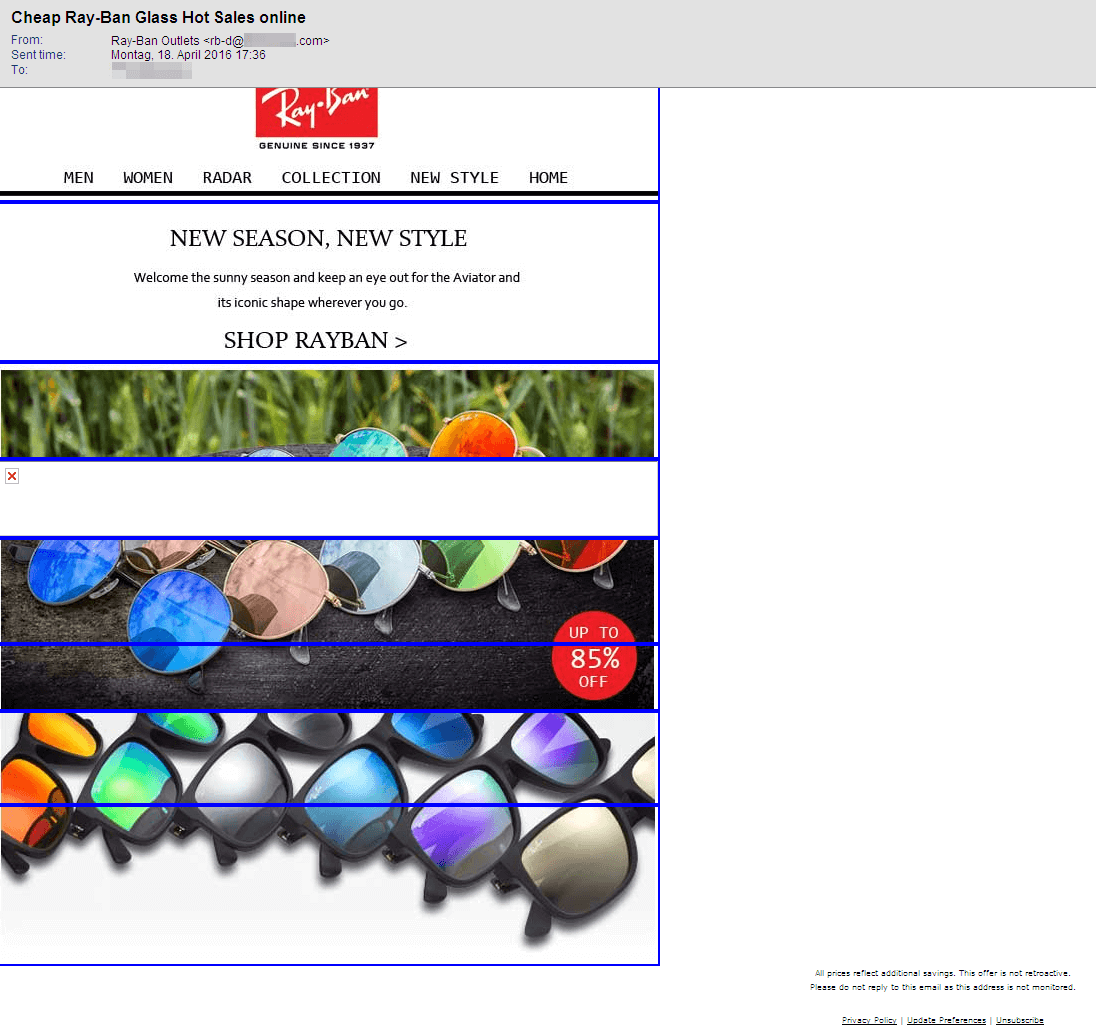
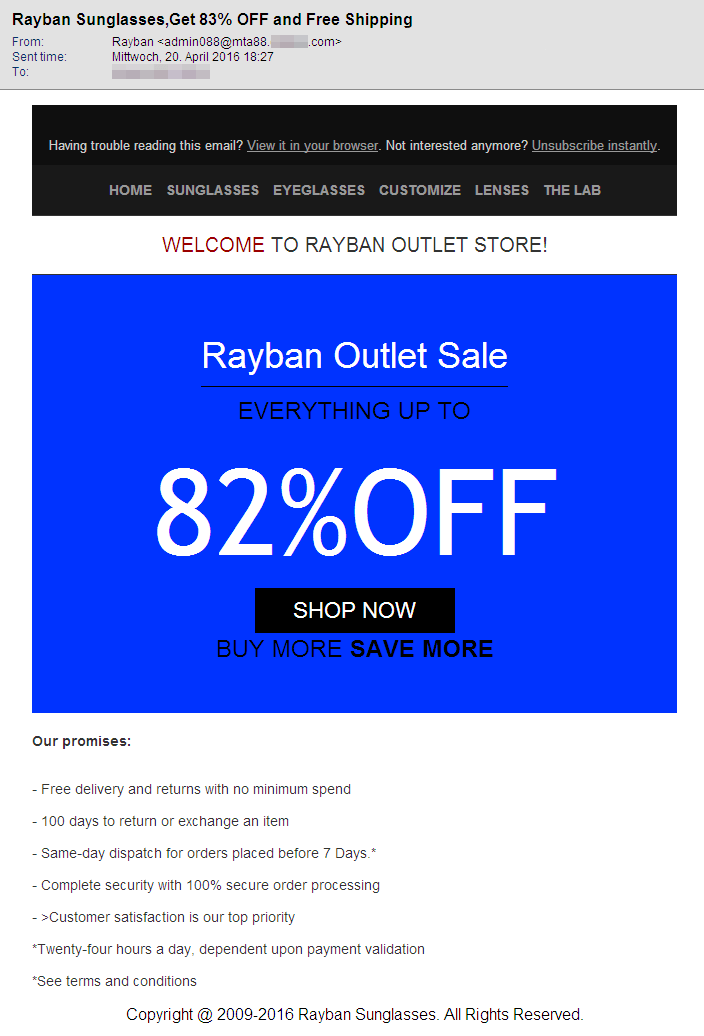
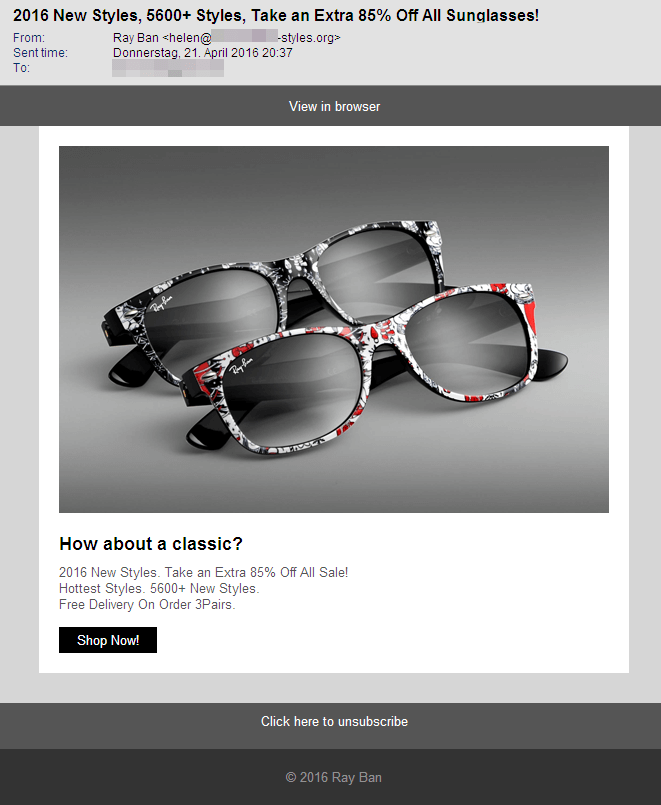
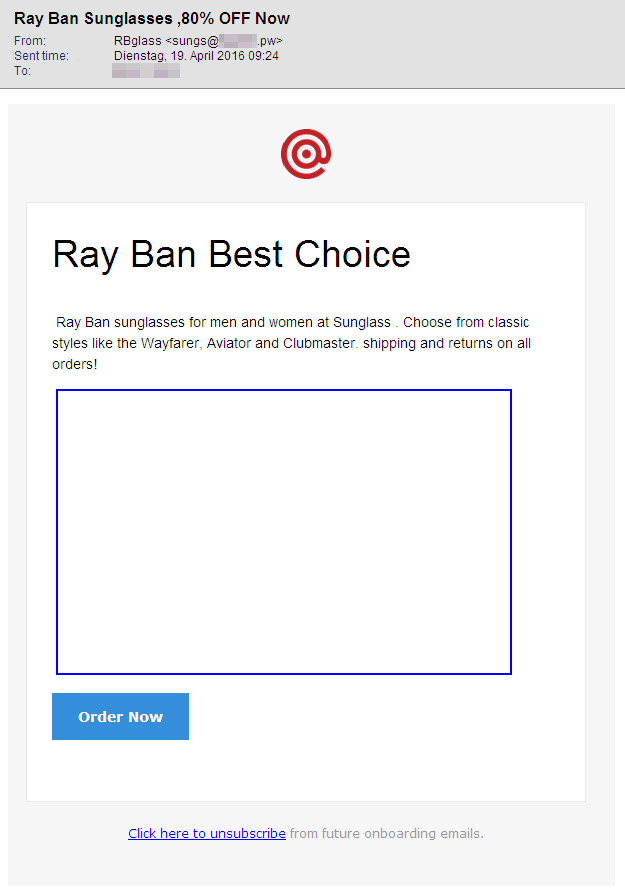
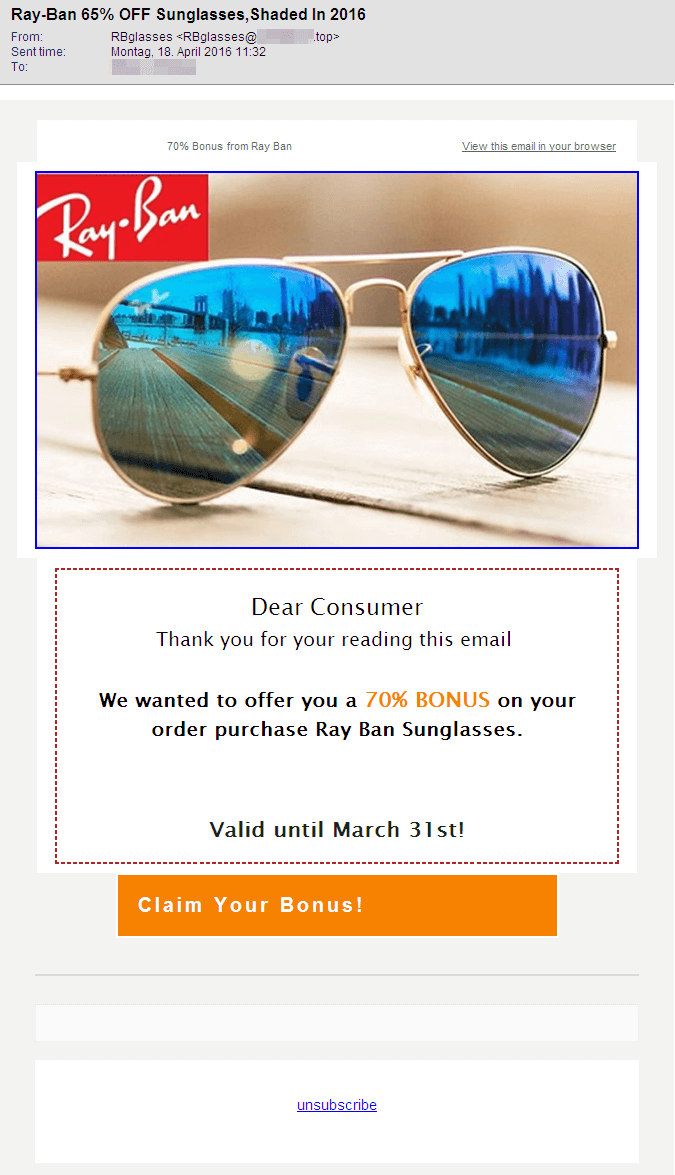
As expected, there is a wide range of promises. In the emails we have analysed, we were promised discounts ranging from 65% to 85% for sunglasses. None of the analysed emails contained an attachment. However, each of them contained references to web shops in which the advertised glasses could apparently be bought.
As the selection of screenshots illustrates, there are quite a few differences in the design of the emails in HTML view. Some of them appear quite professional and look like they could be legitimate advertising by a popular brand. Others, in contrast, are quite drab and should immediately arouse suspicion. Further indicators for such spam:
- The subject promises 65% discount but the text outbids it with 70%. The senders allegedly combined parts from two spam campaigns and did not pay too much attention to the texts.
- The officially registered trade mark is Ray-Ban. But emails and websites analysed offer rather interesting variations, such as Ray_Ban, Ray.Ban, RayBan, Ray Ban, RaYban, Ra y*ban…
- The emails very often contain dates to suggest that the offers are limited until a certain date. But some of those offers had already expired when we received the emails.
They all have one thing in common: They contain links to websites of suspicious shops, which we will later cover in the context of potential risks.
Web 2.0: Facebook Links
The function for tagging friends in photos has been around for a long time. Facebook has now enabled tagging for status updates as well. Spammers are using this function. To do this, they use hacked Facebook profiles but also accounts created specifically for this purpose as well as repurposed accounts that once served a different purpose.
Example 1 – Invitations to events
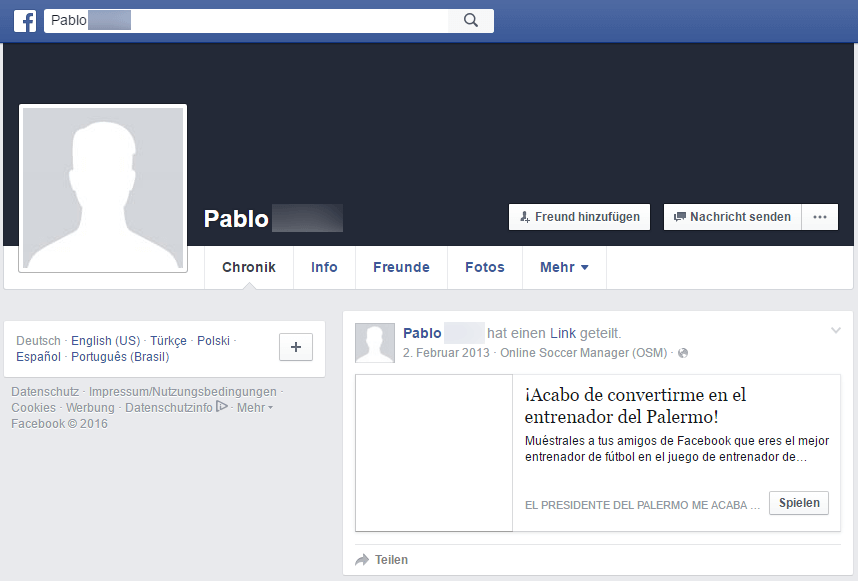
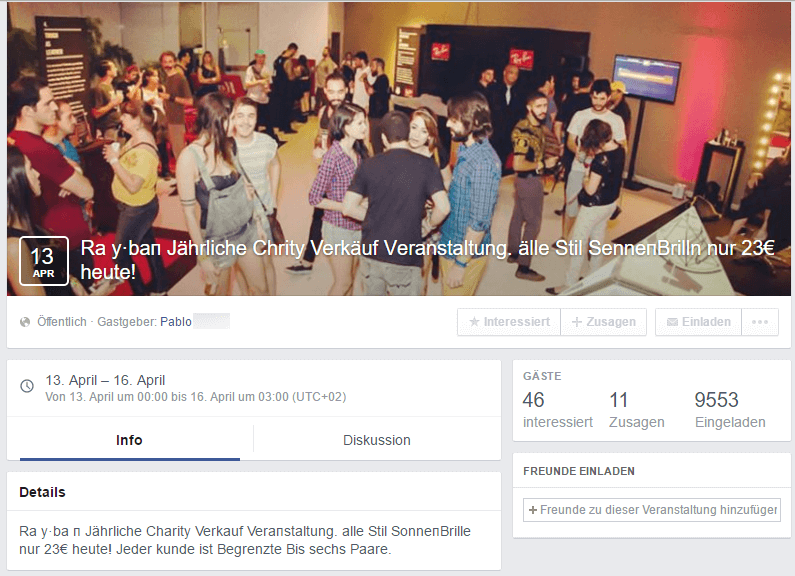
They use a profile to create an event with photos and information on Ray-Ban bait advertising and then invite unsuspecting users to this event.
As you can see in the screenshots, it looks like an account that has been inactive for an extended period of time has been abused here – unless the attackers specifically deleted all timeline posts except for one from the year 2013. In total, 9,553 people were invited to this event and some actually accepted the invitation!
The purpose of the event is to publish and spread the URL to one of the suspicious shops. The URL appears over and over in the entries for this event, as illustrated by the screenshot (on the right). The events as such do not pose a risk to Facebook users, but the people behind them can present their potentially dangerous websites.
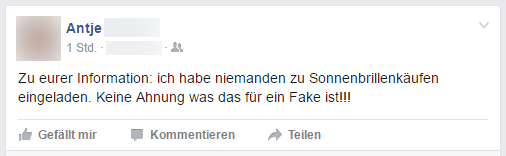
Users who find out that their good name has been abused often inform their friends quite quickly and can only hope that nobody has fallen for the scam:
There are various ways of spreading event invitations:
| Click-jacking is one of these options. Here, initiators might integrate invisible Like buttons on websites, place them over a legitimate button and thus "force" users to make a positive click for the bad guys. We must not forget about actual organic spreading from one person to another as a distribution method either. "Dirty" Facebook apps are another option: Sometimes the event organisers claim that a Facebook app must be installed in order to participate in an event or competition designed in a similar fashion. This method is also referred to as sharebaiting. The advertised app generally requires all sorts of permissions to the user's social media account and can then distribute new spam to friends and friends of friends – the digital snowball keeps rolling on and getting larger. |
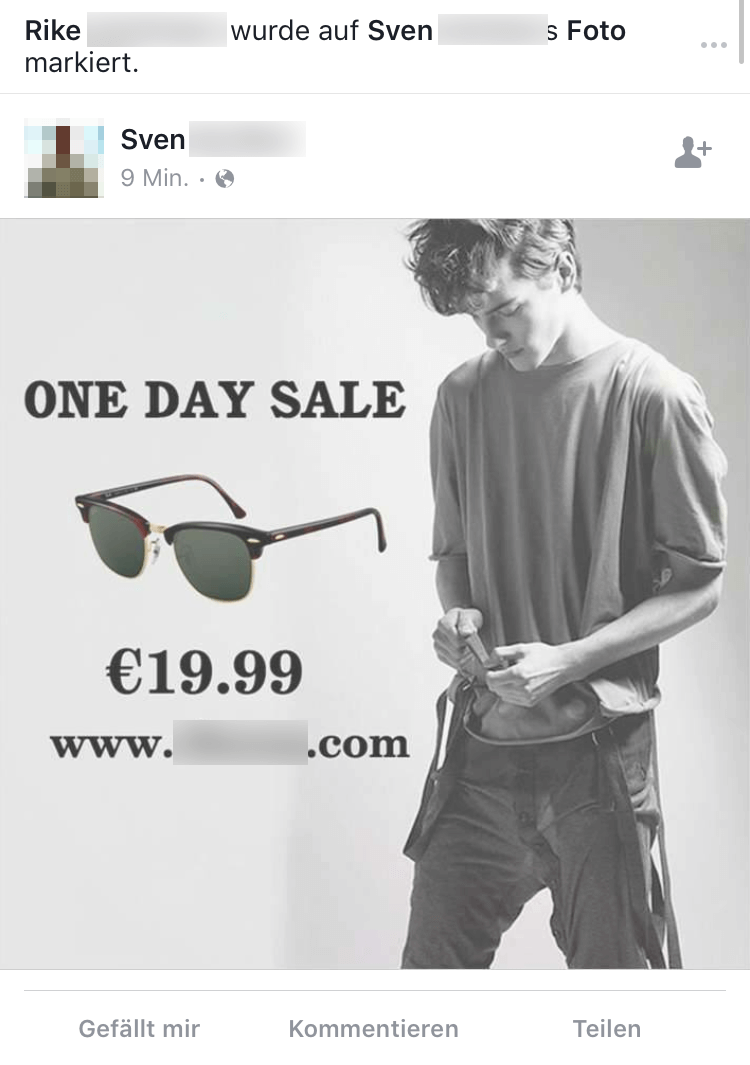
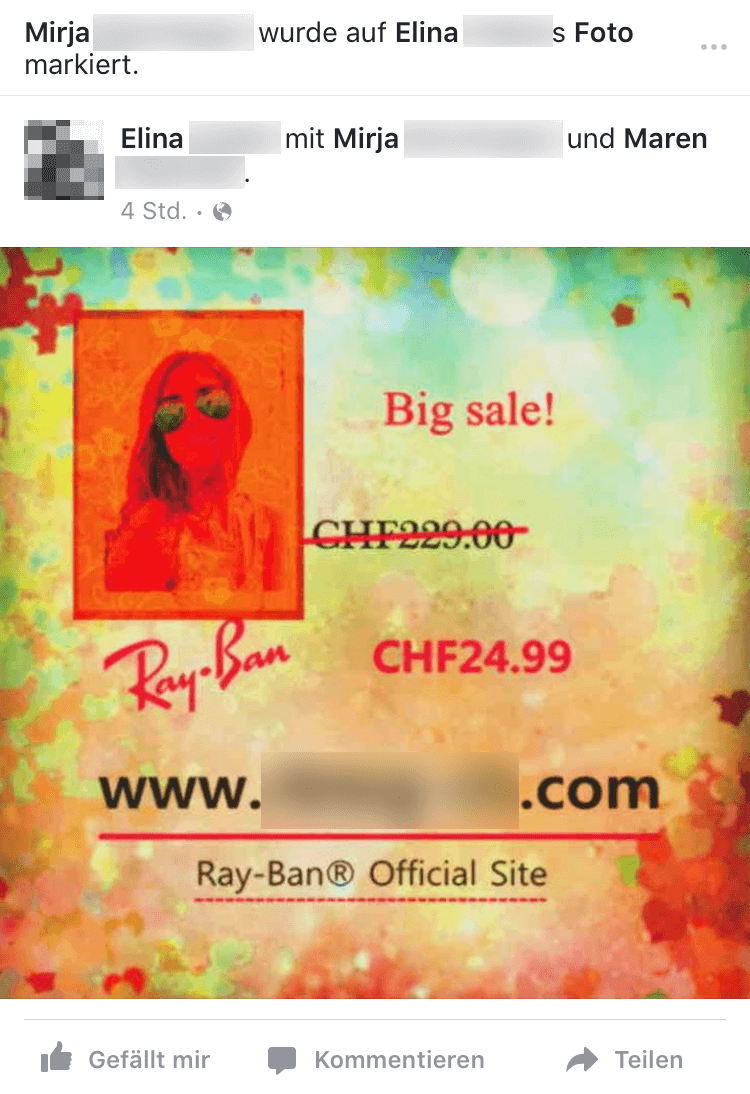
Example 2 – Tags on photos
They hack the account of an existing Facebook user and post intrusive advertising images in the user's name. To do this, they tag persons in the list of friends because it is a well-known fact that a recommendation by a friend is much more trustworthy than a recommendation by a stranger. To avoid being discovered immediately, spammers usually tag only a few friends in order to make the advertising appear more authentic. Furthermore, using only a few tags might make any existing spam protection mechanism of the portal act less aggressively.
The colourful images and outrageously low prices are designed to tempt the tagged persons to visit the specified websites and shop there.
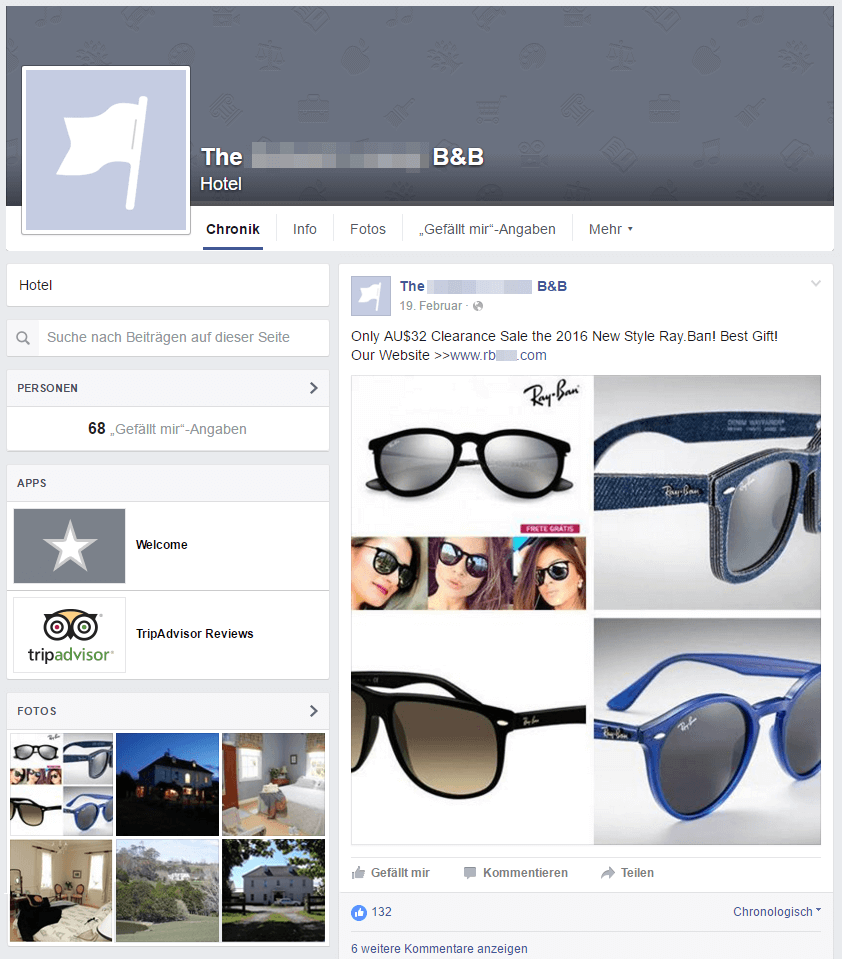
Example 3 – Posts on walls
There are again two possibilities for spreading the content: Attackers can vreate new accounts and spam walls of accounts that do not restrict the possibility to post on walls. Furthermore, attackers can hack accounts of Facebook users and also Facebook sites and can then spread the ads on the respective wall or on other walls in the hacked accounts’ names. Such a case of a hacked account overtook a New Zealand Bed & Breakfast account which then involuntarily served dubious ads for a few weeks. Interesting fact: The ad gained 132 Likes, more than the site itself was able to accumulate!
Advertising by SMS and (Instant) Messenger
In the summer of 2014, US Americans experienced a remarkable wave of this type of spam for fashionable eyewear. The iMessage service by Apple, in particular, was abused by spammers using short scripts. Senders could quickly write code on a Mac for sending a bait message to what felt like every single user. Prior to sending a message to a phone number or email address, the iMessage service provides information about whether or not the recipient is registered for iMessage. This leads to a very high success rate!
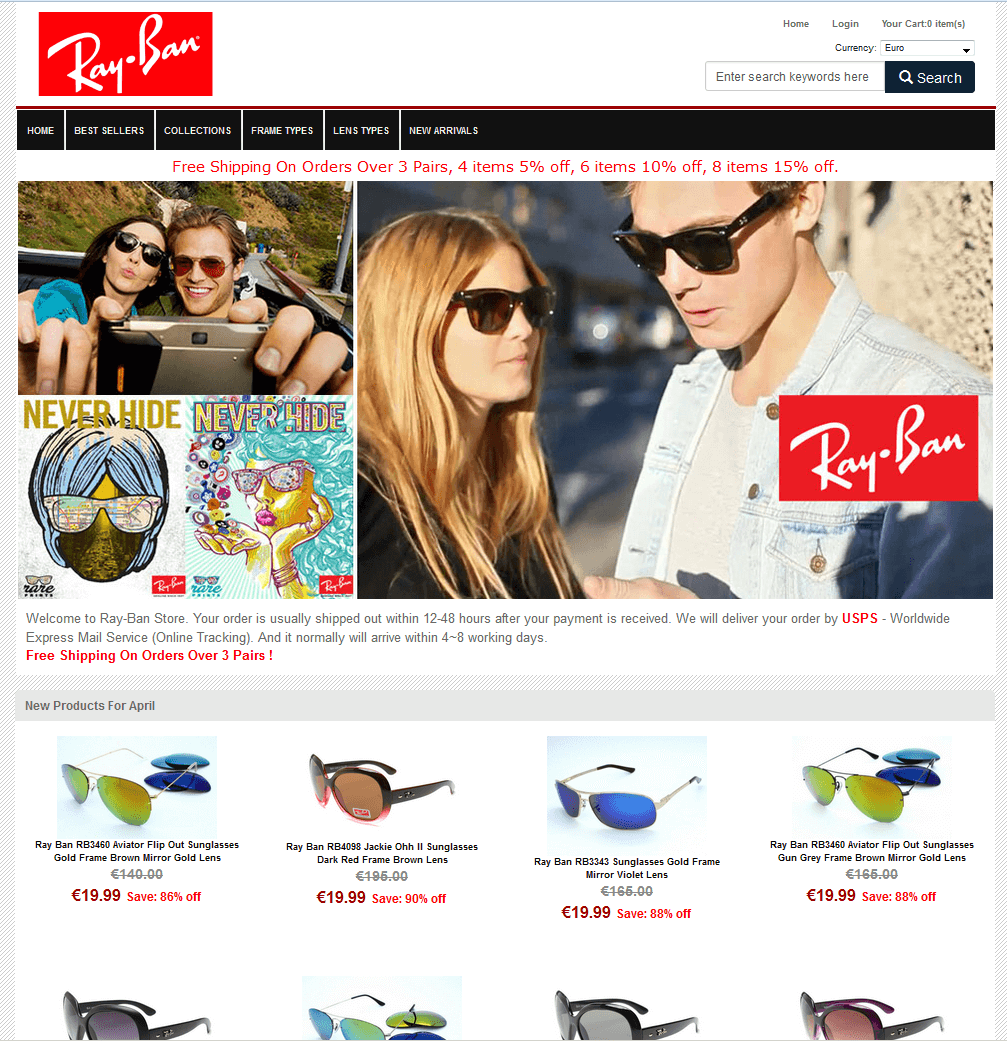
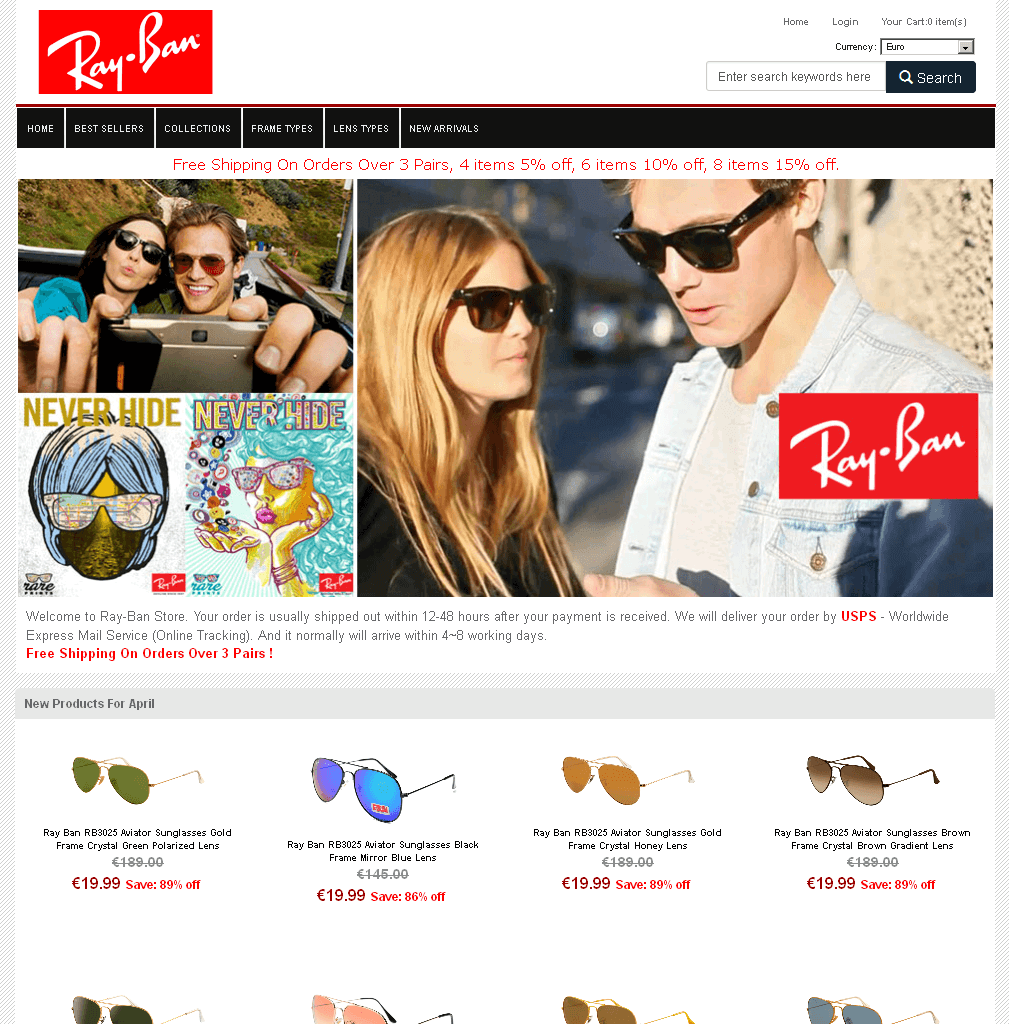
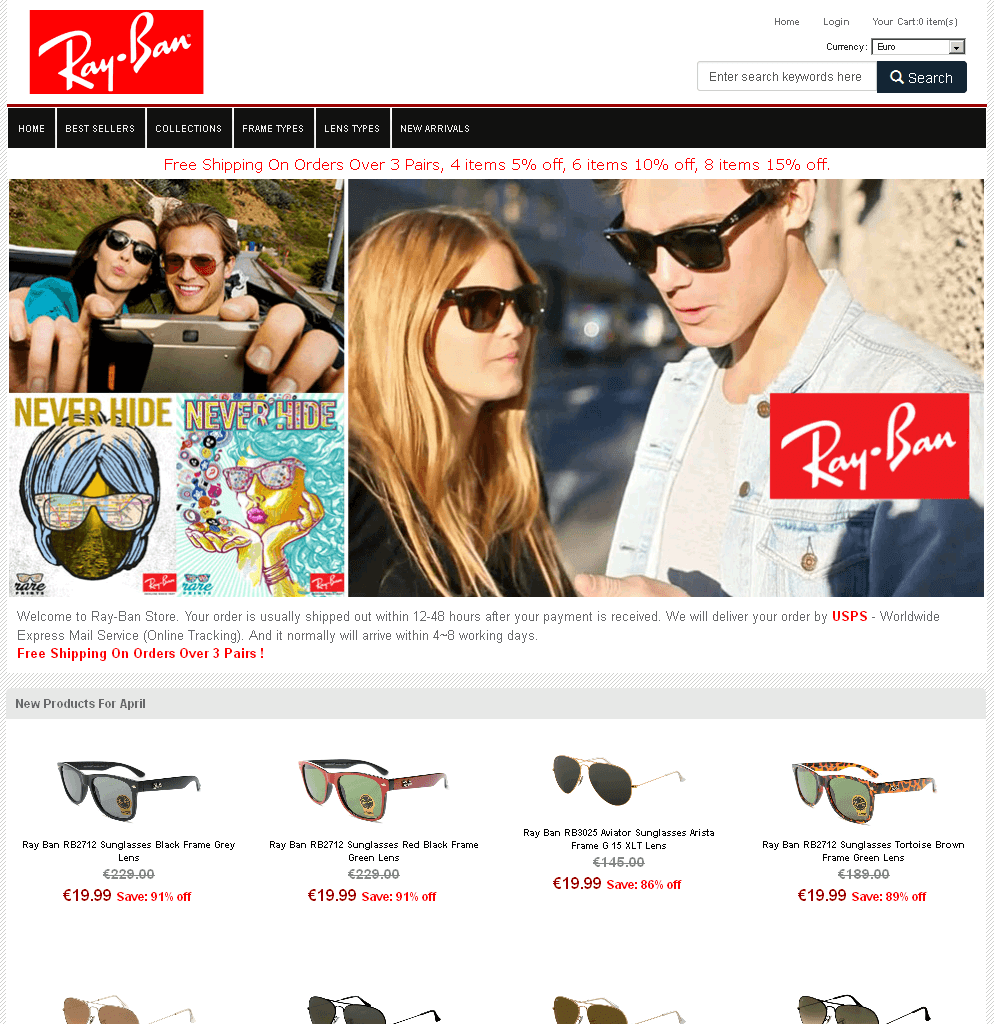
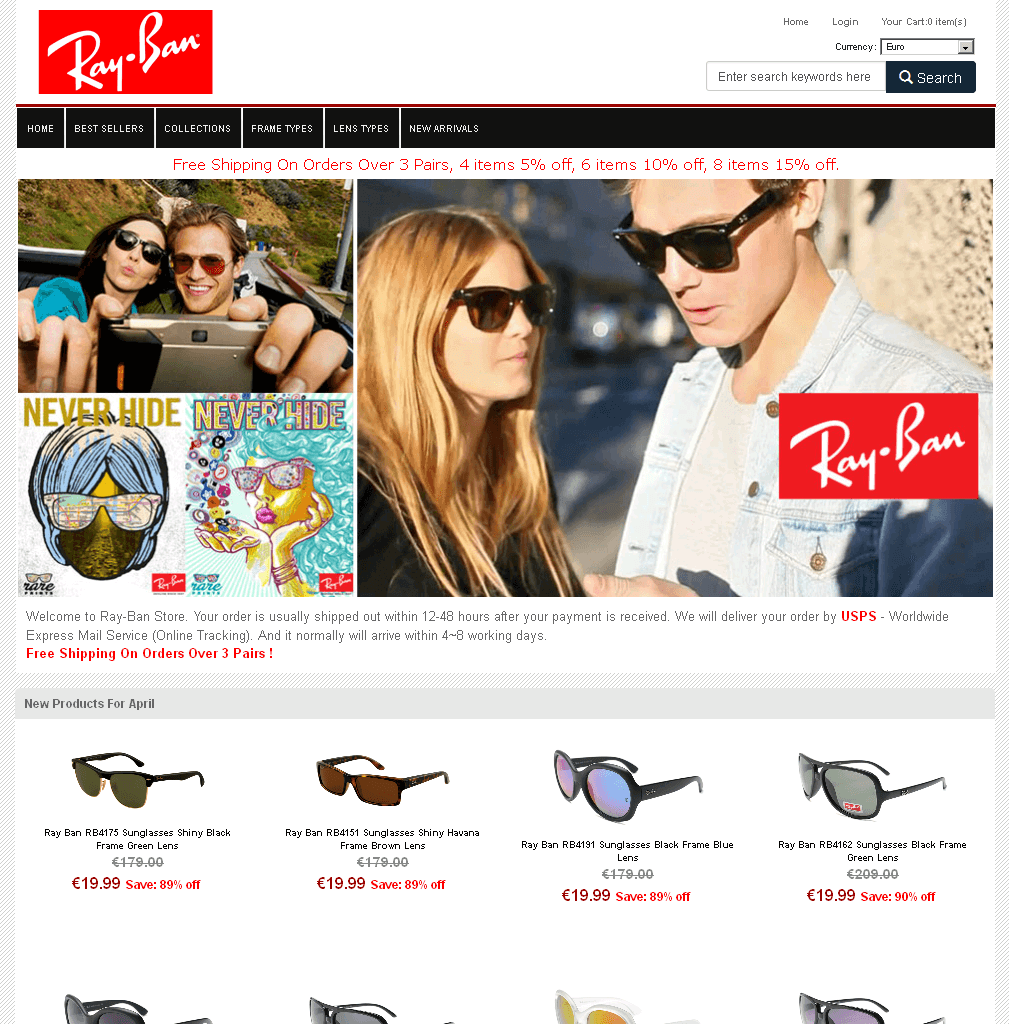
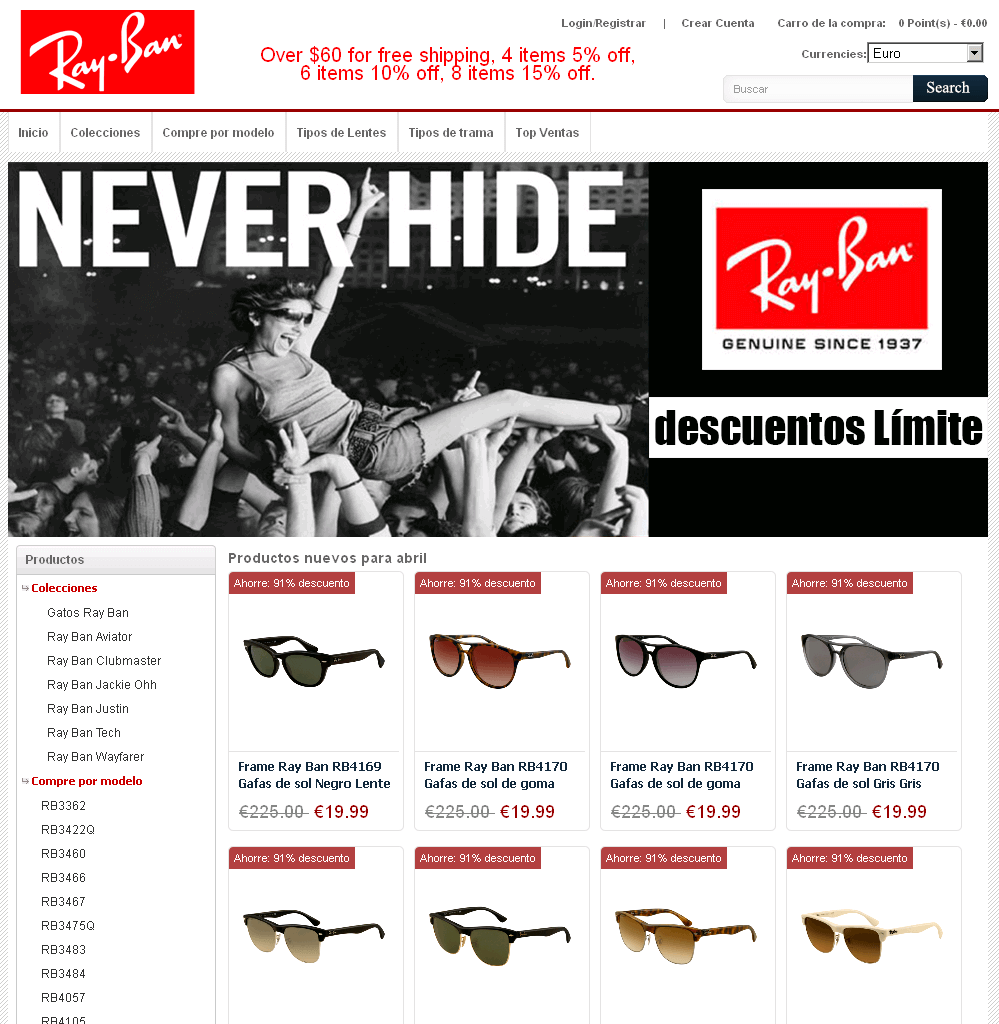
The supposed Shops
A selection of screenshots from these websites shows that they look very similar. The people behind them often use copies of the original websites, which are integrated into so-called phishing kits to enable quick adjustments. All the operator of a site has to do is to enter the target data for form fields and the like in order to place a supposed original shop site online without much effort.
The reconstructed sites often look just like the originals and it is rather hard to spot mistakes; however they stick out because of bad translations. German text we saw, translated to English now, would be something like "discount crazy" or "view, find your style here" or "new entry block harmful light" or even “Free Shippng for Mini Order 1 Pieces”. The language the website is presented in – in case the web server does not adapt because of location sharing options – gives a hint at the intial target audience. Missing or very unusual information on Imprint pages can also be an indicator of copy cats. Some of the websites feature supposed certificates of authenticity and security certificates, which are also mere copies from original websites. For more tips on identifying such websites, refer to our info graphic on secure online shopping.
Who is behind these offers?
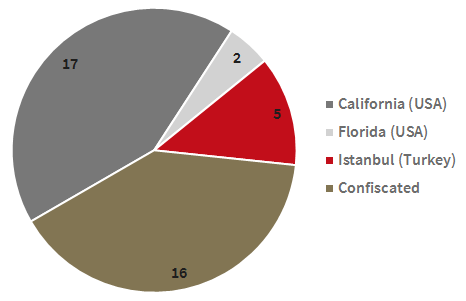
These are not the tricks of an individual person or organisation, but there are certainly overlaps in the instances of email and social media scams we have recently analysed: 24 of the 40 domains analysed were still active. All active domains were registered using Chinese registrar information and there were various names of registrars, registrant organisations and registrant names that appeared several times. Five of the active domains are currently stored on servers in Istanbul (Turkey), two in Florida (USA) and 17 in California (USA). In contrast, 16 websites are already under legal investigation, which the Luxottica S.p.A company has initiated against the operators.
Who is Luxottica?
Luxottica S.p.A (NYSE and MTA) is the world's largest eyewear company and has its headquarters in Italy. It unites glasses, sunglasses and retailers from this industry as well as medical services under one roof. The most well-known brands here are Ray-Ban and Oakley, as well as many others.
Ray-Ban, the brand most frequently used in this scam, is an American brand which now belongs to the Italian corporation. The previous owner Bausch&Lomb used to produce sunglasses for the US Army under the name Ray-Ban (do you remember the movie Top Gun?!) and sold Ray-Ban to Luxottica in 1999. After a year of abstinence, the products re-entered the market and have been the Italian company's best seller ever since. They are sold for approx. US$ 150 a piece whereby the sunglasses are currently sold for approximately 20 times their estimated production price. Last century, they were sold for approximately US$ 30.
Hence, it comes as no surprise that cyber criminals are exploiting this booming business and specifically target the global market leader with their sunglasses scams.
Do these suspicious shops exist only for sunglasses?
No, not at all. Many other industries and brands are also affected. There are "irresistible offers" for designer handbags, luxury watches, the latest sports gear and, last but not least, medication.
What are the Risks to Internet Users?
The possible effects are at least as varied as the scams described:
- The supposed shops might have been created only for phishing purposes. Here, attackers can use the entered personal and financial data for criminal activities (shopping with credit card data, selling data on the black market, identity theft ...).
- Irrespective of how the data could be used and abused further, there is a high risk that the money paid is lost. Payments made by credit card and some online payment service providers offer buyer protection but that is not always available or applicable. Some of the shops we have analysed even charged a cancellation fee of 30%, whereby cancellation is not supposed to be available after dispatch.
- If the suspicious shop actually ships the goods, it is possible that they are fake, stolen and/or even present a health risk. Our research has shown that there are many incidents where extremely cheap sunglasses and especially fake products offer no UV protection whatsoever. This is even more damaging to the eye than not wearing any sunglasses according to the scientists who performed the analyses.
- The website could also be prepped for a technical attack designed to install malware on the visitor's computer without their knowledge. This did not happen in the context of the current analyses but it is possible.
What can Users do to protect themselves against these Scams?
On the Computer
- Use a comprehensive security solution to protect yourself against malware and phishing attacks. A very good spam filter should naturally be included in the standard equipment!
- Install updates for operating systems, software and other components as soon as they become available to eliminate vulnerabilities, among other things.
- Be extremely careful when emails make promises that are too good to be true. Do not visit the advertised websites, do not forward the emails and do not respond to them! The only place they belong is the bin!
- Keep in mind the G DATA Tips&Tricks for safe online shopping and also consider to buy goods offline, directly from your local retailer.
On Social Networks
- Regularly delete your browser history and the created cookies to make tracking and target redirection more difficult.
- Check whether any bookmarks you might have set on a social media platform still point to the original website and not to some other site.
- Do not accept every single friend request; this helps you avoid unnecessary spam.
- If you notice something unusual about your profile or if it has been used to spread spam, make sure you change your password.