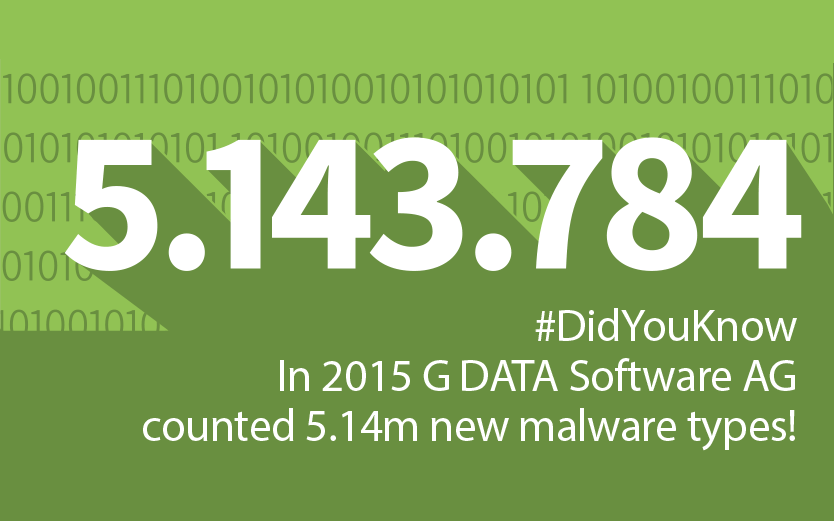
Various exploit kits being used
Media reports that refer to an article by MalwareBytes (https://blog.malwarebytes.org/exploits-2/2015/10/new-neutrino-ek-campaign-drops-andromeda/) only talk of attacks using the Neutrino exploit kit. However, G DATA SecurityLabs also noticed an increase in the number of prevented attacks by the Nuclear and Angler exploit kits since 17 October. The attacks by Nuclear only took place on 17 October, whereas the attacks by Angler only started to die down during the course of 18 October. On the same day, a massive wave of infection by the Neutrino exploit kit began, which is still going on.
How does the malware get onto the websites?
The company behind the online shop software assumes that webmasters are still using outdated versions. Attackers abuse known – but, in the old versions, still unclosed – security holes to infect the shops with malware. Operators that are affected should update their shop system immediately. 1
What is an exploit kit?
Depending on the version being used, an exploit kit is a tool that contains a number of different attacks on vulnerabilities (exploits). When a user visits a manipulated website, as in the current case involving Magento shops, the exploit kit is used to scan the configuration of the PC for security holes in applications (browsers, installed software or operating system). If one or even multiple vulnerabilities are found on the system, a suitable exploit is sent to the client. It then uses the discovered security flaw to secretly download additional malware code to the vulnerable computer (drive-by infection).
G DATA Exploit Protection checks the system for unusual behaviour
The exploitation of software security holes by so-called exploits is the most popular method nowadays for cyber criminals to infect computers with malware. Today, malware is principally distributed via websites that have been manipulated by cyber criminals. Exploits specifically look for vulnerabilities in the user's system. The site operators generally remain unaware.
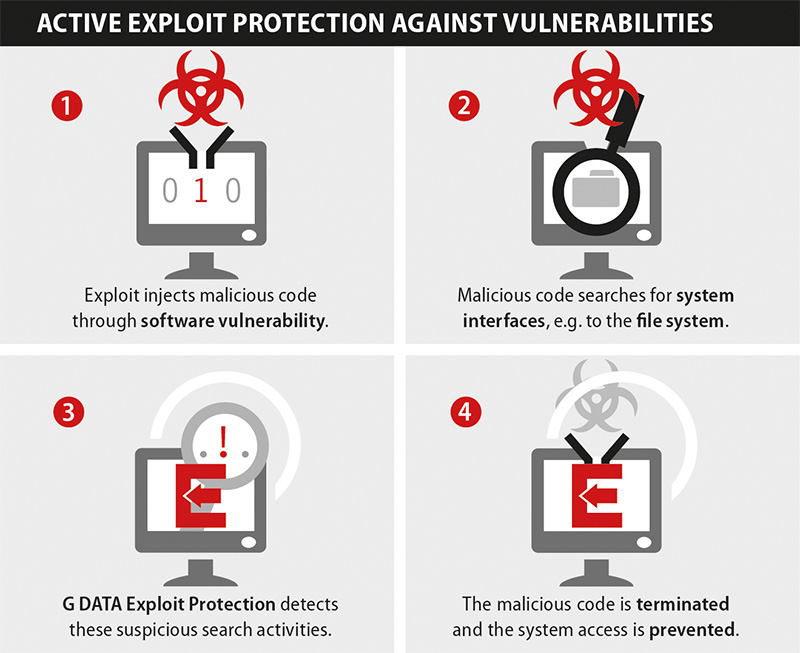
G DATA effectively blocks the exploitation of security holes and prevents malware infections. G DATA Exploit Protection constantly checks the behaviour of the installed software for irregularities. If any unusual behaviour is detected in a software process, the G DATA security solution blocks the attempted attack, stops the intruder and immediately raises the alarm. G DATA Exploit Protection even offers effective protection against previously unknown attacks, known as "zero day exploits".
[1] http://magento.com/security/news/important-security-updatemagento.com/security/news/important-security-update