The G Data SecurityLabs published the Malware Report for the first half of 2015. Here are the most important findings.
- The first half of 2015 saw 3,045,722 new strains of malware. This is a growth of slightly more than a quarter (26.6%) below the record of the second half of 2014. But it is about two thirds (+64,8%) higher than the number of the same period last year. On average this is 12 new malware strains per minute. We expect that the number of new malware strains will be well above the level of 2014.
- The total of all malware strains since 2006 is now 22,393,098.
- The Top 10 of prevented malware attacks is dominated by Adware and Potentially Unwanted Programs (PUP). Dealply and Graftor are the most prevalent families in this field.
- Health care was the topic most prevalent of all websites identified as malicious (26,6%). Websites of this category also launched campaigns promising a rather dubious rain of money.
- The topic "personal advertising and dating" is new in the Top 10. Sites from this category offer to install paid premium services or launching expensive phone calls.
- Malicious and fraudulent websites are still most frequently hosted in USA, China, and France. Ukraine with 5% is new in the Top 10 and made it to position 4. It is unclear whether and how this relates to the political havoc in this region.
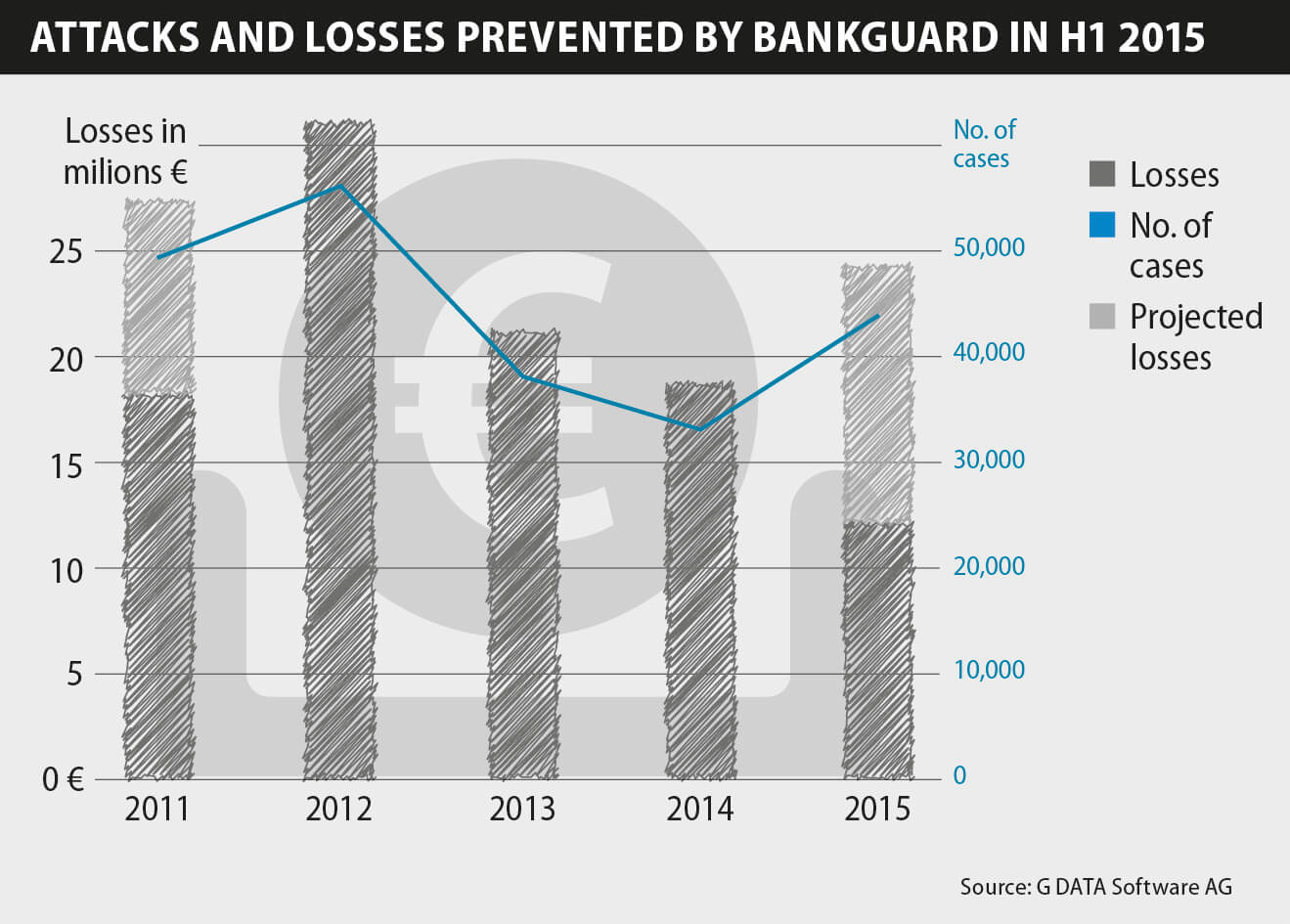
- The number of attacks carried out by Banking Trojans will presumably be rising in 2015 for the first time since 2012.
- The Swatbanker family caused an all-time-high of repelled attacks in March 2015, due to successful email campaigns. Its main targets were bank customers from Germany, Austria, and Poland. The activities continued until June 2015.
- During the first half year of 2015 the sum of prevented damage by BankGuard passed the mark of 100 million Euro.
- Exploits for vulnerabilities are integrated into exploit kits after just a few days. Users who do not keep their systems up-to-date easily fall victim to cyber criminals. Attackers use exploit kits to silently and automatically check PCs for a large number of vulnerabilities at a time and to subsequently compromise PCs, e.g. during the visit of a website (drive-by-infection).
- The vulnerabilities in Adobe Flash were most frequently abused to silently, and automatically attack and compromise PCs (Exploit). Exploits based on Java were scarcely used, due to the implemented "click-to-play" function default in the most popular browsers. “Click-to-play” might also help to minimize the use of Flash exploits in the near future.
- On January 21st the Angler Exploit Kit integrated an exploit for a new and undisclosed vulnerability in Adobe Flash (CVE-2015-0311). In the subsequent weeks the experts of the G DATA SecurityLabs measured new records for the prevention of exploits.
- Another peak in the number of repelled exploit was caused by the integration of the Nuclear Exploit Kit in advertisements of a Google AdSense content supplier. The attackers deployed the Nuclear Exploit Kit with the aim of infecting millions of users with malware.
Read the full report for more information.