Malvertising
Attacks of this sort are known technically as "malvertising" – a combination of "malware" and "advertising". The distribution of advertising on the Internet is becoming an ever larger and more lucrative business. Almost every modern website carries advertising banners, and the more popular a site is, the more money can be made from such displays. Hence it is also worthwhile for cyber attackers to abuse this legitimate function for their own purposes. Consequently, slipping malware onto an advertising giant such as Google Ads is a major coup for the attackers. According to Google's own information, two million publishers of every size rely on AdSense! Publishers in this case are website operators that provide web space on their site for the service.
Website operators have the option of choosing among a wide range of advertising providers to earn money from the content shown. Time and time again there are reports that servers have been hacked by attackers and malware delivered instead of just advertising. This means keeping your wits about you when checking for banners to buy.
Google AdSense is without doubt one of the largest advertising networks and has a corresponding reputation, so a great number of website operators trust the service. Some 12% of the 100,000 most popular websites use Google AdSense as an advertising medium for appropriate displays. However, the strike zone for attackers is correspondingly large if they manage to infiltrate such a service.
What is an exploit kit?
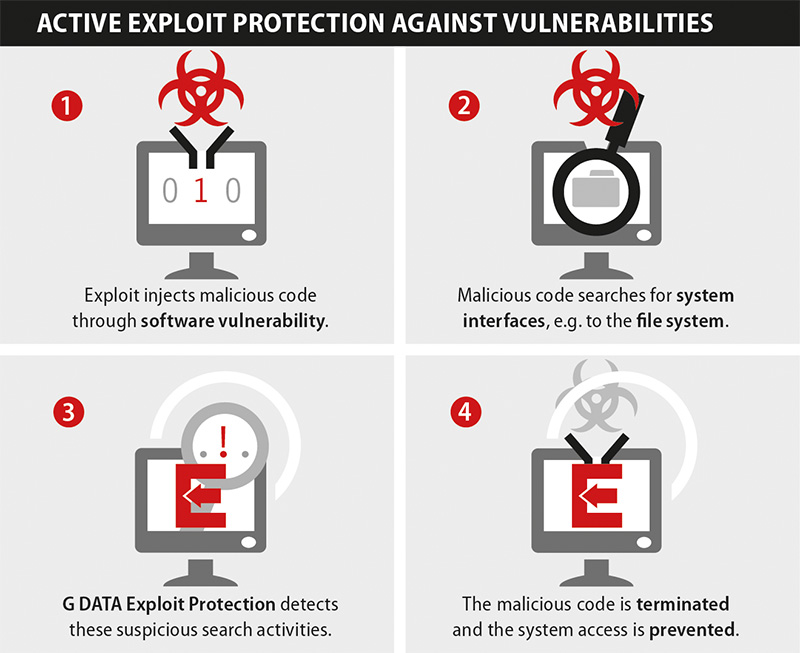
An exploit kit is a tool that, depending on the version being used, contains a number of different attacks on vulnerabilities (exploits) and is used as a means of attack. If a user visits a primed website, the exploit kit is used to check the configuration of the user's computer for applications that can be attacked (browser, software, OS etc.). If the configuration that is read contains one or more vulnerabilities, a suitable exploit is sent to the client to use the discovered security flaw. Subsequently, additional malcode may be secretly downloaded to the vulnerable computer (drive-by infection).
How the current infection chain works
- An advertising area is reserved on a website using Google AdSense – a perfectly normal operation.
- The web banner to be loaded is determined by the Google AdSense servers. They do this by providing JavaScript in the advertising space. This script downloads the content to be displayed from an advertising partner – in this case engagelab.com. This is also a perfectly normal process.
- But in the current case, this code contains a reference (an IFRAME) to a malicious address on another server.
- This iframe is loaded in the advertising space on the website and the potential victim is thus exposed to the exploit kit.
The effect of this scenario for web users
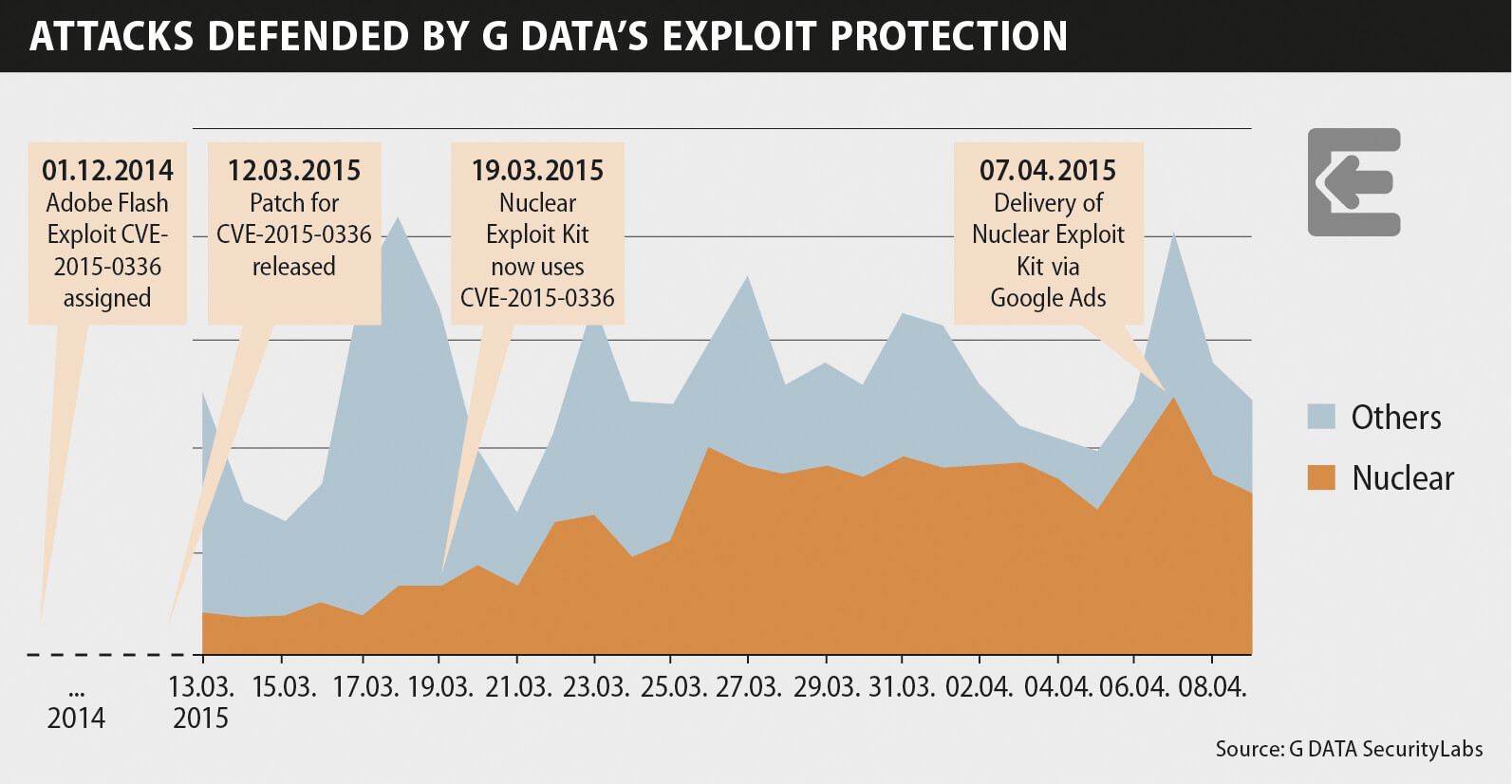
This combination is very explosive, "nuclear" if you like in this case. The attackers have decided to use the Nuclear exploit kit against visitors to the affected websites. This exploit kit can be purchased on the black market for around USD 1500. Since mid-March, Nuclear has been using an exploit against the Adobe Flash program that security experts know as CVE-2015-0336. Analysis by G DATA SecurityLabs clearly shows that the exploit kit has become more successful in its attacks since the integration of this exploit. The number of attacks being fended off is growing, reaching its current high on April 07, when the malware was distributed via Google Ads:
The security hole described in CVE-2015-0336 was registered back in December of last year. However, until a patch and details of the associated security hole were published by Adobe, there were apparently no starting points for the attackers behind the Nuclear exploit kit for exploiting the security hole. But appropriate malware appeared in the kit just one week later.
The attacks amount to nothing on systems that are fully up to date, i.e. that have the patch dated March 12 installed. In a business environment, so-called patch management solutions offer a convenient means for keeping every company computer fully up to date.
For a long time, the mantra for company computers was ’never change a running system’. This approach is a gold mine for attackers
Only people who keep the software and operating system of their computers fully up to date are protected against such attacks.
At least every PC that had not installed the available patch by March 19 has been open to attack by the Nuclear exploit kit in this instance – both private computers and PCs in a business environment. In the majority of cases, the attacks take place via security holes that have long been closed. So too in this case.
#
According to reports, the current malvertising campaign ran Pony Loader on the compromised computer following a successful attack. This is known to the G DATA security solutions as Gen:Variant.Graftor.182875 and blocked. The downloader then downloads any additional malware files it wants onto the PC.
G DATA Exploit Protection has been preventing attacks since the outset
Reactive protection technologies such as virus signatures are only partially helpful against an exploit as, because of their nature of offering only reactive protection, they often have too long a reaction time, as in this case. For effective protection here, proactive technologies – in addition to functioning patch management – are essential. Installing updates and patches has a positive effect on the protection of the computer, as this is the only way that known security holes can be effectively closed.
G DATA Exploit Protection is such a proactive protection component, and it has stopped infection by the Nuclear exploit kit. This particular protection component also protects users against previously unknown attacks, known as zero day attacks.
What this means for you, in summary
- An up-to-date, comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails is also useful. Proactive protection technologies such as G DATA BankGuard and G DATA Exploit Protection complete the security package. Tip for company networks: G DATA's business solutions offer G DATA PatchManagement as an add-on module.
- The installed operating system, the software, the browser and its components as well as the security solution installed should always be kept up-to-date. Program updates should be installed immediately to close existing security holes.
- In your web browser, we recommend deactivating the execution of plug-ins, scripts and also most advertising content by default and activating them only as needed. You can create these settings in the browser or use appropriate browser enhancements.