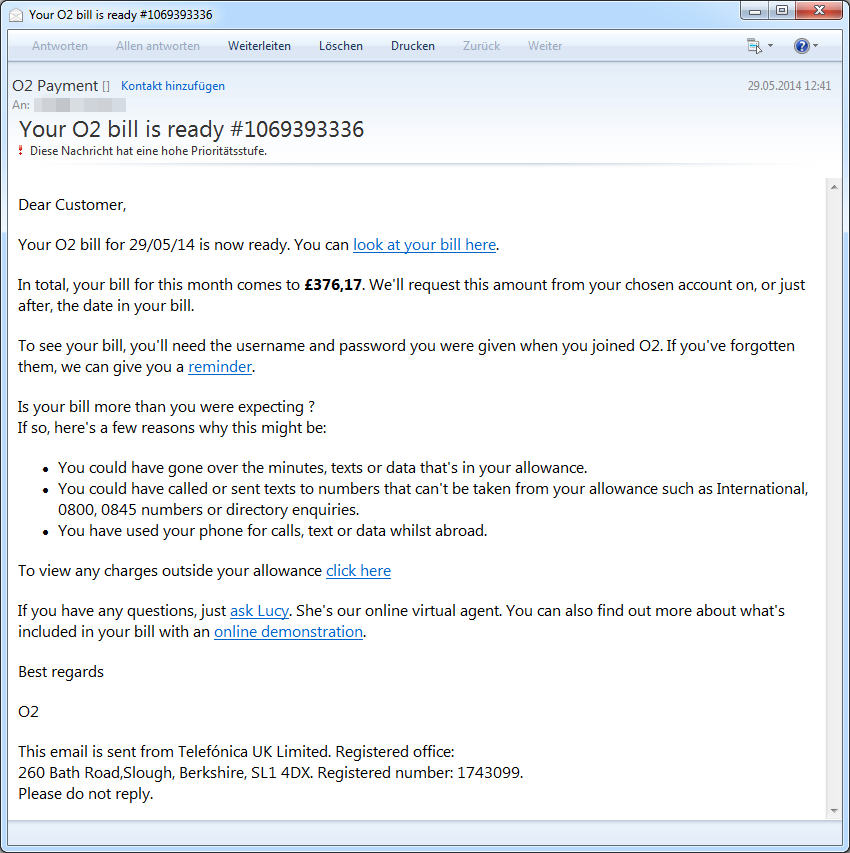
The bulk of the email is still designed as if it were an invoice from a well-known company or banking information. However, it is obvious that the list of top companies involved has expanded. In addition to telecommunications companies and banks, as previously reported, new well-known decoys have now been added to the two scams:
- Telekom
- Vodafone
- O2
- Volksbank / Fiducia
- Sparkasse
- UBS
- Weltbild
- ... and it cannot be ruled out that more are being circulated and new names are being added.
Scam 1: Swatbanker lurking behind URLs in emails
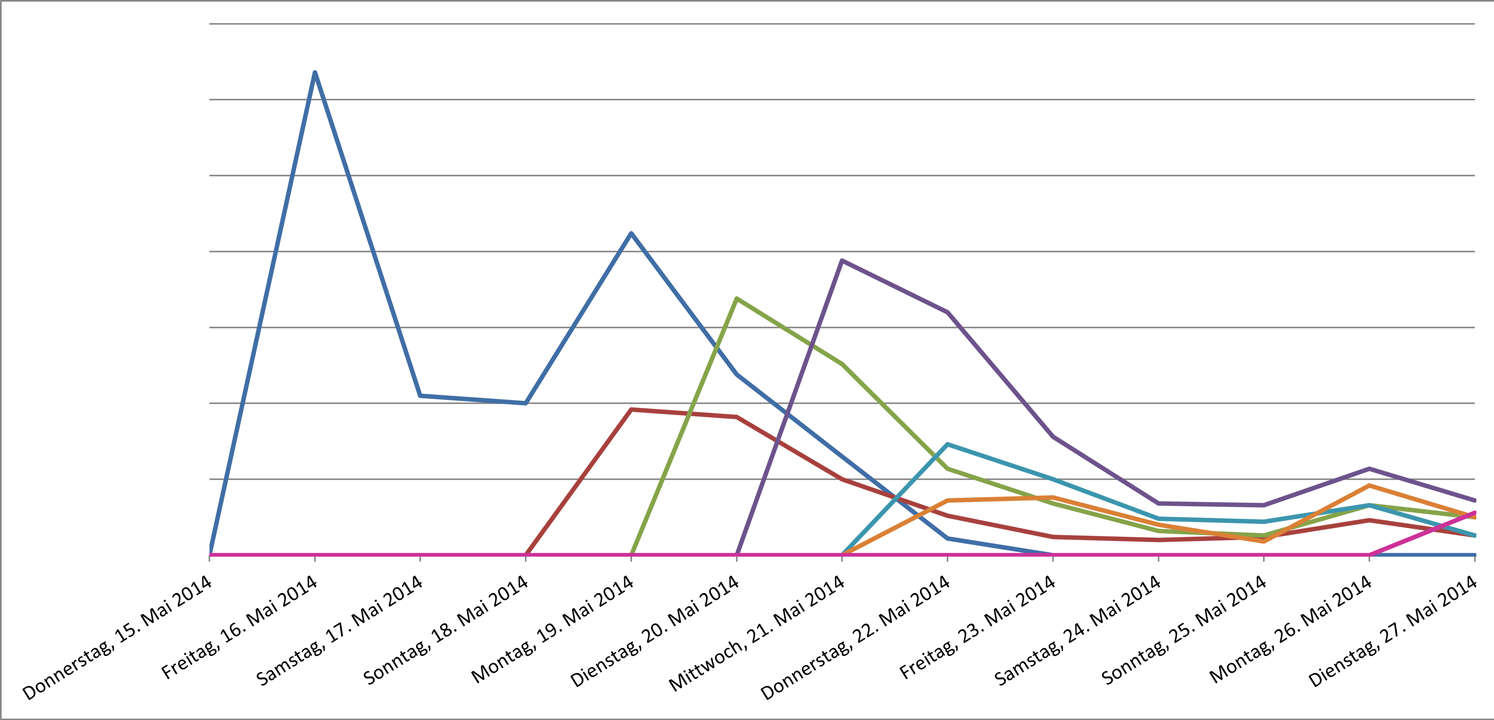
This scam, which is now well-known, continues to be active, and has been since mid-May. Over the last two weekends, G DATA experts have seen a drop in the number of people visiting infected websites in this case, and in the infections detected by BankGuard. Possible causes might be that either the attackers are also treating themselves to a break at the weekend, or that the campaign is mainly directed at business customers, who do not read work emails at the weekend.
The following graphic shows examples in the latest case of what effect the individual schemes are having. The number of websites blocked by G DATA that have been visited is shown. Waves can clearly be seen, with peaks at the start of a new phase.
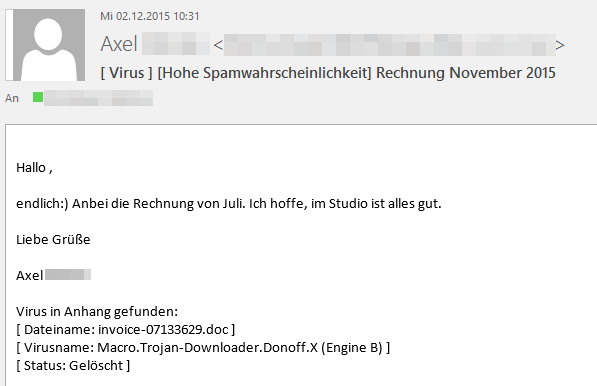
Scam 2: Bebloh sent as an email attachment
Not only are there more emails being circulated now that try to get the user to click on a link and infect them – they also contain the supposed invoice itself as an email attachment – generally as a .zip file. It is not new that Bebloh is being distributed as an attachment; however, it is conspicuous that the emails containing attachments are so similar to those in the first scam in terms of design.
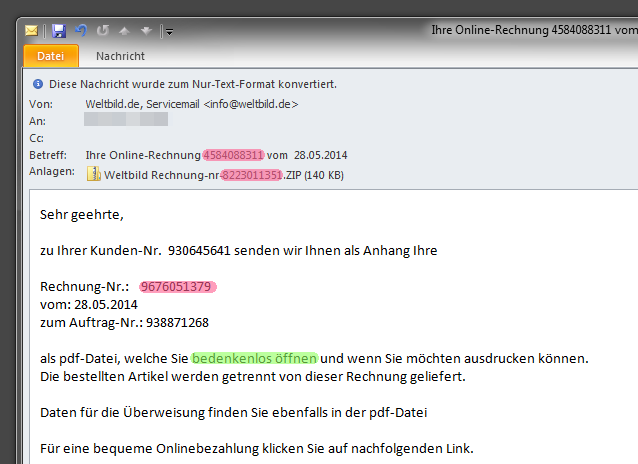
Such spam emails are often exposed by simple things, even when the visual design is highly reminiscent of the original.
- In the case shown above, there are often at least three different supposed invoice numbers – one in the subject line, one in the name of the attached file and a third within the text.
- Furthermore there is no personal salutation in the email. Many spammers have "upgraded" and use the recipient's original name. However, when this is not provided, it is a clear indication of possible fakery.
- The statement highlighted in green above, that the invoice can "be opened without hesitation", is of course a plain lie and would not even be mentioned in an actual invoice email from a proper company.
- After opening the supposed invoice and successful infection with a banking Trojan, the attackers try to urge the potential victims to pay the invoice via online banking: "Please click on the following link for handy online payment." However, it does not access a banking site.
Do both attacks originate from the same perpetrators?
Whether the new scam now involves copycats, or whether perhaps the senders of the email URL scheme are offering their services to other interested parties who have their own malware, is not clear. However, it seems unlikely that the attackers behind the first scam have drawn up the second scam for their own purposes. Although both sets of malware currently being distributed concern banking Trojans, Swatbanker and Bebloh are very different.
Update:
While compiling this article, experts at G DATA SecurityLabs have also discovered an English-language version of this email campaign! Based on the scheme already known about, these are emails containing URLs behind which the Swatbanker malware is lurking.