Microsoft have patched four highly critical security flaws in their Exchange mail server application. Those flaws allowed an attacker to access confidential information. No passwords are needed to exploit the vulnerabilities. Affected organizations should apply the patches immediately.
An attacker group called HAFNIUM has exploited a total of four previously unpatched vulnerabilities in Microsoft Exchange to access companies' internal communications. This was made possible by an attacker impersonating an Exchange server to an accessing client. In the further course, the attackers were able to store files on the mail server. This enabled the group to leverage the placement of a backdoor that would put them in a position to access the entire database of the mail server at any time. Among others, a successful attack would give the perpetrators the ability to extract entire address directories and even entire mailboxes. The security vulnerabilities are all listed in the NVD:
Who is affected?
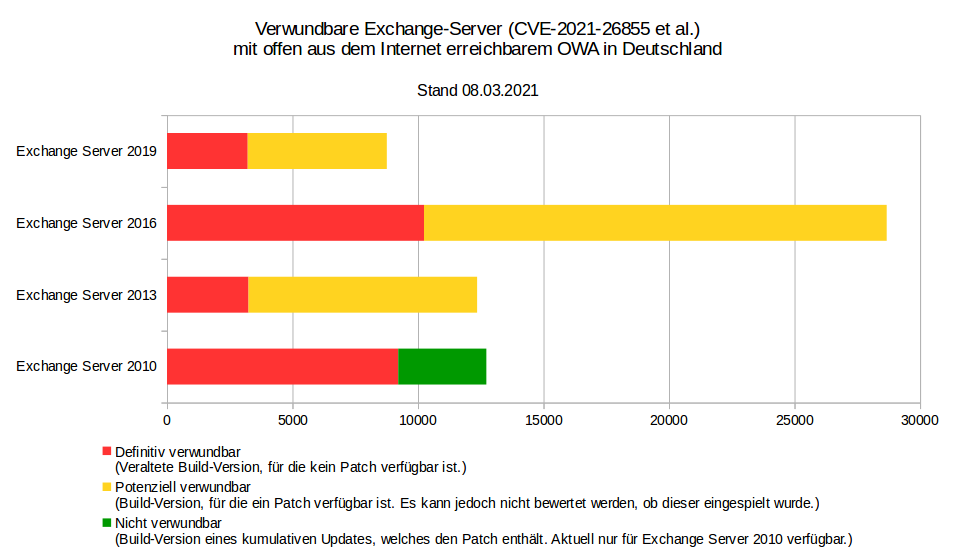
All on-premise installations of Microsoft Exchange 2013, 2016 and 2019 are affected by the vulnerabilities. Updates for these versions are available and should be installed immediately. Updates are also available for Exchange 2010 SP3 to prevent exploitation of the vulnerabilities on these systems. No action is required for the cloud versions of Microsoft Exchange.
What are the risks?
If an attacker like HAFNIUM (or a copycat) exploits the vulnerabilities, it is possible to access all of a company's internal e-mail communication. Since one of the vulnerabilities also allows files to be stored and executed, a successful attack could also result in a permanent foothold of the attacker inside the network. Access via a web shell would be possible at any time. The confidentiality and integrity of mails would no longer be guaranteed. Furthermore, it is possible for an attacker to create and export memory images of running processes. Useful information can also be obtained from this. Other tools are also reloaded from the Internet for exfiltrating information, sometimes from Github. In preparation for data exfiltration, archive files are often placed in %ProgramData%, which are later transmitted to the attackers via a file-sharing platform.
A complete Listing of Indicators of Compromise is available on the Microsoft website (link will open in a new browser window) einsehbar. According to the German CERT-BUND, there are up to 58.000 systems still potentially vulnerable in Germany alone, roughly one week after the general public was made aware of the flaws. It is very likely that this figure is significantly higher on an international scale.
Is my organization affected?
Microsoft has published a script that specifically checks whether the vulnerabilities are/were exploited. It is available on Github, including the associated documentation. Administrators can use it to determine if there has been activity that may indicate the presence of activity associated with the HAFNIUM group (or other copycats). However, the most important thing is to install the updates for the vulnerabilities immediately.
Who or what is HAFNIUM?

According to previous findings, HAFNIUM is a so-called APT group that very likely operates out of Asia. In most cases, APT groups have government support and are therefore well-positioned financially and in terms of personnel. Unlike in a purely profit-oriented criminal setting, APT groups have no requirement to produce quick results. The operations conducted by APT groups are usually planned long in advance and are sometimes designed to go on for years. The goals range from simply gathering information to manipulating data and processes to the detriment of the target. Traditionally, government bodies and authorities are the primary target, but the same is also true for companies that either supply government bodies or support them with services. Organizations outside the government can also become the target of an APT group, especially if these organs have an indirect or direct stake in political decisions. HAFNIUM also follows this pattern.
Note for users of G DATA solutions
One of the indicators for exploiting of the vulnerabilities is the presence of certain archive files in %ProgramData%.
However, G DATA's ManagementServer and Client also stores some archive files in this directory. The following folders are typically part of an existing G DATA installation, which may also contain other subfolders. These are either update files created by G DATA ManagementServer, belonging to G DATA's Exchange plugin, or created by G DATA SecurityClient. Installation logs can also be found in these directories.
C:\ProgramData\G Data\AntiVirusKit Client\P2PUpdates\
C:\ProgramData\G Data\Setups\Logs\
C:\ProgramData\G Data\AntiVirus ManagementServer\LinuxRepo
C:\ProgramData\G Data\AntiVirus ManagementServer\Patches
C:\ProgramData\G Data\AntiVirus ManagementServer\Updates
The fact of the matter is: There are some very clear indications that the security flaws previously described are being actively exploited, both by the HAFNIUM actors as well as other parties who copy HAFNIUM's operating procedures. Therefore it cannot be hammered home far enough to those in charge of an organization's Exchange servers: Installi the patches issues by Microsoft as soon as possible if you have not done so already.
Update: Flaws known to Microsoft since early January; more patches released
According to various reports, the security vulnerabilities in Exchange have been known to Microsoft since the beginning of January. The first reports had already been sent to the manufacturer on January 5. By the end of January, signs were accumulating that something big was up. The security vulnerabilities were originally scheduled to be fixed on yesterday's Patch Tuesday. However, since a large number of Exchange servers were suddenly compromised with the help of these vulnerabilities before this date and various attackers worldwide were specifically scouring the Internet for vulnerable machines, the update was released early. This means that it has already been possible for weeks to compromise an Exchange server without being noticed. This has serious consequences. It is not enough to simply install the patches - anyone operating an Exchange server that is vulnerable to attack must actually actively search for signs of compromise and specifically eliminate them. The security vulnerabilities in Exchange are so serious that Microsoft has yet to release an update to fix them, even for the long-discontinued 2010 version.
Furthermore, there is a real risk that criminals will install ransomware on compromised Exchange servers and attempt to blackmail affected companies, authorities and government organizations. This brings back memories of a patch Microsoft rolled out a few months before the Wannacry outbreak. Again, due to the severity of the vulnerability, legacy operating systems were once again secured with a patch. However, because the patch was not installed everywhere, Wannacry was able to cause billions of dollars in damage worldwide. The vulnerabilities that have now been patched have the potential to cause similar damage. This makes it all the more important that the patches are installed immediately and that affected systems are specifically checked and cleaned up. Those who fail to install the security patches now risk outages and damage from which the company may not be able to recover.
In addition to the four already known vulnerabilities, Microsoft has now also added patches for three more vulnerabilities. Two of them (CVE-2021-26412 and CVE-2021-27078) allow remote code execution and are also classified as highly critical.