For a long time, gaming was just considered “a bit of a laugh” or “something for the kids”. Unsurprisingly, the security aspect did not receive a lot of attention – it just wasn’t seen as a problem or particularly relevant. But today’s gamers are not just two players sitting side by side as a dot pongs back and forth across the home computer screen. The opposite is true: with the advent of the internet, gaming has developed into a platform that feeds an entire industry and has spawned a billion-dollar business: Competitions with prize money well into the million dollars, are broadcast live. Thousands of players who live in a persistent game world at the same time equip their virtual character and go into battle against evil minions. Novel virtual reality technologies, which guarantee an excellent immersive experience also influence the adult entertainmanent industry. Hardware and peripherals manufacturers produce customised, high-performance graphics cards, processors, memory, mice, keyboards and monitors for the target audience. In short: Gaming is no longer “something that kids do”. Gaming has come of age and requires special attention, as the platform is an ideal target for cyber attacks. G DATA explains how gamers can reduce their degree of exposure to attack and what protection options are available.
From Pong to Ping
The history of gaming can be traced back to the early 1940s, when computer scientists began to program and develop the first simulations and very simple and trivial games for their own research. Mathematician John von Neumann and economist Oskar Morgenstern explored the general theory of games and showed how their Minmax algorithm can, in theory, also be applied to chess. The aim of these first steps into the world of gaming was to use the artificial intelligence (AI) of the computer lucratively to supplement human intelligence. They wanted to understand how and why the computer makes decisions in a particular algorithm to use the results for further research. Admittedly, the term “gaming” does not seem to fit quite right, as these attempts did not resemble games or gaming as we know them today. Nevertheless, the aspect of AI remains, and is still used today for non-player characters. It took a few more years before the first commercial and locally playable video game was released by Atari and dubbed Pong.
The year 1973 proved to be a milestone. Pong had a simple but entertaining concept. The point of the game was to move a rectangular paddle on one of the two sides of the screen up and down so that the advancing ball is successfully blocked and hit back to the opponent. If the player failed to stop and play the ball, the other player got a point. The ability to reacto in in real time was necessary in order to come out as the winner. The competitive aspect is still an essential part of today’s games, although by now they take place online. Thanks to the internet, such competitions are played on the virtual battlefield against players from all over the world. The decisive factor in so-called shooters like Counter-Strike is the ping of a player. The ping (in milliseconds) represents the time it takes for a data packet to be sent to the server and back again. The lower the ping, the faster the data packet and the faster a player can react to an opponent without a significant delay. But just as every business model that involves large sums of money, the arrival of online gaming also brought criminals on the scene
Hacked accounts: a whole new ball game
It is easy to understand why such efforts are made to hack accounts: Cybercriminals can exploit the personal data that a player shares on a platform and can sell it on for financial reward. In most cases, however, it is not worth targeting individual players. The return on investment would be too low. Instead the attackers try to lure the player to a compromised website that passes itself off as a login platform. This can be a copied login portal of a game manufacturer or directly a platform, where after entering account data you get a free serial number for a newly released game, a special costume or other items - supposedly. With these login data, the attackers can get hold of in-game items and account information. While losing virtual objects may not seem like a big deal for non-gamers, it is a huge blow for gamers. Hundreds of in-game game hours and real money have been invested to obtain rare and powerful equipment. These are what hackers can sell profitably on auction platforms. The same applies to personal data, such as gamer name, birthday, address, telephone number, e-mail address, accounting information to linked social media accounts, age, sex, and many more records. Of course, this information has a higher value than in-game items when traded on the Darknet.
Tip: To minimise account loss, a strong password should first of all be chosen. We have published a guide that takes a more in-depth look at the subject of "password security". Moreover, if available, two-factor authentication should be enabled. This makes access more difficult for the attacker. To protect against phishing sites and other malware, Security-Software from G DATA is recommended.
Social engineering: Think before disclosing information.
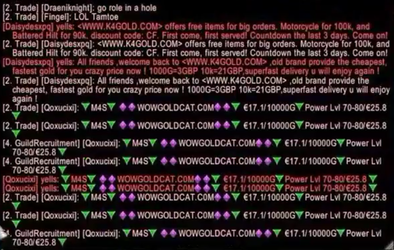
In Massively Multiplayer Online Roleplaying Games (MMORPG) in particular, bogus players pass themselves off as game masters (GMs). GMs are actually the support staff of a company who communicate via chat with a gamer during the game if he or his game character has any problems in the persistent in-game world. Some companies even have GMs who have their own in-game characters and who monitor the situation on the ground, inside the game. But that’s not the case for every game. That is why cyber-attackers impersonate game masters. When a problem needs to be solved, those fake GMs usually claim that user data such as user name and password are required before a problem can be addressed in any detail. What an inexperienced player either does not know or simply forgets is that a real GM would never ask for account information. A completely different method for obtaining account data, which also works via a game’s chat system, are so-called “Gold sellers”. This term is given to computer gamers who, collect large amounts of in-game currency or game items to sell them on. Leveling services are another source of danger. In this case, a player transfers his account information via a website to allow another person to play with his hero in exchange for real money, in order to speed up the process of getting a high-level game character. The paying player thus exchanges real money for time. However, the Terms and Conditions of most manufacturers strictly prohibit the transfer of the account data as well as the purchase of in-game items or in-game currency. Failure to comply can lead to the (temporary) blocking/banning or even termination of the account. And yet: Account leveling services or in-game currency are often offered on auction platforms. There is no guarantee as to whether the player will ever get his hero back again, especially with regard to the transfer of account information, despite the promises made by the service providers.
Tip: Always submit any support requests you have in relation to the game directly via the official site of a game operator or via in-game features such as a ticketing system. This spares you the risk of falling victim to a cyber attacker. At the same time: Do not buy any leveling services or other third-party services that compromise the account and disclose personal information. In short: if someone asks your account details in exchange for something, walk away from it.
In the event of a problem, quick action is called for
Anyone who uses the same passwords and user names for different platforms can very easily also become a victim of an attack in a gaming environment. You can use a special website to check if an account you are reusing a password for is potentially compromised. If search results are listed, it is necessary to act quickly, as this data is passed in or even sold on Darknet forums or web shops. The risk of the game account also being stolen cannot be ruled out either. If the account has been lost in spite of security efforts, the game operator must be notified as soon as possible. The support staff will look more closely at the IP. If a countrywide surge is recorded, the probability is high that the support reacts very quickly. Further instructions such as serial number of the game, last purchases, e-mail address or other security questions will be transmitted via the ticket system. This ensures that the right owner is sitting in front of the screen. The support staff will send a link via the ticket system, which should be clicked. It will ask for a new password, which should not be similar to the already hacked password.
After a few hours the account should have been reactivated again and the fun in front of the domestic screen continues. So with this advice in mind: happy and safe gaming!