This type of attack represents a new phenomenon for us. What we are seeing here is a scam that has been put together with a great deal of effort, in order to cause damage to a broad swathe of users. The app is obtained from legitimate applications; it collects personal data, accesses the mobile transfer paths and is promoted by way of questionable positive reviews. This is besides the fact, of course, that setting up a subscription without any user interaction is also extremely questionable from a legal viewpoint. Affected users should immediately seek assistance and take steps to remedy it
Premium SMS messages were the first attacks on Android users – almost six years ago, malware with this functionality was the primary risk. Since then of course, the malware landscape for mobile devices has moved on significantly. For this very reason, it is notable that a new type of subscription trap has been evident in the current Google Play store for several weeks now, causing Android users direct financial woe. It is a curious case.
The investigation turned up extensive information that we reveal here. Below is a brief summary of the facts that we have put together. Full information and details can be found under "The case in detail".
Brief summary
- Interesting distribution method: users are lured by a legitimate app into installing a malicious one called Blend Color Puzzle.
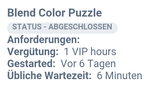
- New way of being lured into the subscription trap: the malicious app has been in Google Play since early November 2015. After being launched, it sets up two subscriptions with Dutch companies, without any intervention by the user. The app does so by shutting off the mobile device's WLAN connection and, as far as we know by now, uses WAP billing, a payment method for mobile devices.
- Previous WAP billing cases originating from apps resulted from the user having clicked on a web banner, for example. However, in the current case, no user interaction has been recorded.
- The subscription is paid for via an intermediary company, making it even harder for those affected to trace the perpetrators and take remedial action. We suspect that an even bigger international network of companies is behind this campaign.
- Negative reviews and inconsistent comments about the app that appear to have been arranged underline the questionable character of the game. Furthermore, there are no other apps from the supposed developer or company to be found.
- G DATA experts of course reported the incident to Google and the app was removed from the store shortly afterwards.
The case in detail
For the sake of understanding, let me tell you a story about a friend. She uses a dating app on her smartphone. She can purchase certain premium functions in the app, or she can "fulfil tasks" to earn these functions. But not to worry, she doesn't have to divulge anything immoral! Rather, she must select one or more apps from a list that is offered and perhaps carry out an additional action as well – launch the app at some point, for example, or something similar. Inviting friends and filling in questionnaires is also "rewarded". There are essentially no major obstacles and so the offers are usually taken up by users.
The providers of the dating app of course earn money by doing this. Every action carried out by flirtatious users earns them profits. "What could go wrong?" thought my friend each time, and exchanged "work" for premium time. However, a few days ago one of the apps she had downloaded turned out to be malicious.
The questionable app
The game offered is called Blend Color Puzzle. In it, people are asked to recognise and tap on shades of colour. At first look, it appears to be quite entertaining, so my friend decided to "work" this app. The dating app promised one hour of free premium functions as a reward for the action of installing and launching the color game. Compared to the example given above, this is a fairly small return, albeit for something that clearly doesn't require much effort.
Blend Color Puzzle has been in the official Google Play store since 3 November 2015 and has already recorded more than 50,000 downloads. That is astounding for what is supposedly a programmer's (fartye.polisertg@gmail.com) or a company's (GHR Corp) debut – both names can be found on the app's info page. No other apps by them have yet been found. The visual similarity to the very popular game Blendoku might be one reason that so many users are willing to try out the free game. Even the app images displayed by the publisher in the Play store show the name Blendoku on the left border of the play area. However, my friend would never have ended up downloading the game if it had not been offered via the dating app.
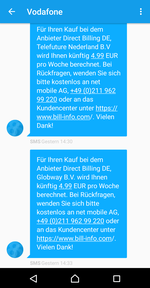
Shortly after launching the game, my friend received two SMS messages informing her that she had set up two subscriptions – which she obviously had not consciously done. Furthermore, she was no longer connected to her WLAN, which she normally always uses when she is at home. Therefore the app must have triggered a purchase that remains invisible to the user. This is a new form of attack, and we wanted to take a closer look at what was going on.
The permissions
The list of permissions that the app requests is unusually extensive for a simple game. This is where we also find the function for cutting off the WLAN connection. However, it only has permission to receive SMS messages, not send them. At the current time, the analysts assume that the app sets up the subscriptions via WAP billing.
- Device and app activity
- Calling up active apps
- SMS
- Receiving SMS
- Photos/media/files
- Changing or deleting USB memory content
- Reading USB memory content
- WLAN connection information
- Calling up WLAN connections
- Device ID and call information
- Calling up phone status and identity
- Other
- Disabling idle mode
- Access to all networks
- Calling up network connections
- Setting up and cutting off WLAN connections
- Changing network connectivity
- Launching on start-up
- Disabling screen lock
- Display via other apps
The app code
The developer has made it difficult for the analysts to take a look at the code in the app, because he has concealed (obfuscated) the program on multiple levels. As far as we currently know, and through partial decryption, the following data appears to be stored into a variable and is then presumably sent to a server:
- SIM provider info
- Network provider info
- WLAN status
- Battery charge status
- Device's language setting
- Device manufacturer
- Device model
- Screen resolution
- Android ID
- IMSI
- IMEI
- Telephone number
The domain that is contacted is currently hosted in Germany. However, it has been registered from the Bahamas – on 2 November 2015, one day before Blend Color Puzzle was put in the Google Play store. Overall the app code reveals a large number of variables and actions based on dependencies. For example, 60 seconds after switching from Wireless LAN to the mobile data network, initiated by the app, a so-called webview is called. This means that a website is invoked, although nothing is displayed to the user, not necessarily. The suspicion, prior to completion of the analysis, is that this is the connection used for transferring the billing data for the subscriptions under the WAP billing process. The app is of course detected by G DATA security solutions and rendered harmless.
Markus Wortmann, a criminologist and police scientist (M.A.), has a similar view. The founder of not-for-profit association Sicheres Netz hilft e.V. reports: "A number of affected users have contacted us looking for help following an unpleasant incident on the net. Subscriptions that are set up because the user hastily accepts the displayed terms and conditions or usage agreements without having actually read them are no longer a rarity. However, technical implementation of a subscription like this, without further action on the part of the user, is new to us too."
A look at the reviews
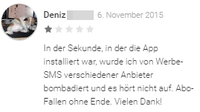
It is conspicuous that, of over 1,000 reviews submitted, almost 25% were negative (awarded fewer than three stars). The first negative comment was registered on 6 November 2015, just three days after the app was launched in the store. Many more negative comments followed this one.
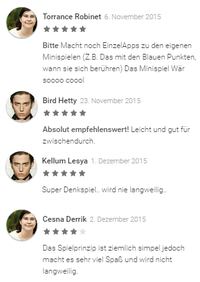
The positive comments should be looked at more closely too. On closer inspection, it is clear that something is not right with many of them. Some users refer to a completely different developer company, or mention the number of levels reached. But the game does not have any levels that can be played – the game is against time and always starts again at zero. A comment that a female user wants a mini game on the level "with the blue dots when they touch each other" is also meaningless. There are no blue dots in this game, no more than there are brain teasers or challenging mind games, as is mentioned elsewhere.
Besides the fact that many of the names used by people posting positive comments sound exotic and sometimes totally artificial, there are even people using the exact same photo. Torrance Robinet and Cesna Derrick are supposed to be men, according to their Google+ profiles. You wouldn't think so from their photos.
The photos in these two examples are obviously of other people. The man is Jackson Rathbone, an American actor, and the woman is apparently a professor of history at the University of Rio de Janeiro in Brazil.
Their images are being misused here. Obviously it is not unusual for users to have an image of their idol as their profile image, but in this case we put the whole thing down to the inanity of an organised scam.
Some of the reviews that do not match the content of the game also connect other apps with the subscription trap. Besides the dating app addressed by us, at least two other programs are mentioned from which users have been directed to the questionable game. Hence it is no longer surprising that the number of downloads for the app has risen so quickly.
The companies behind the subscriptions
The SMS messages received indicate that three companies are involved – net mobile AG from Germany, Telefuture Nederland B.V and Globway B.V., both Dutch.
The two products that were foisted onto my friend were called ABO MOBIMANIACS DOWNLOADS and ABO DE.APPTIPS.ME. They each cost € 4.99 for 7 days. We will not go into the connections behind these two product names or the websites and companies associated with them in any detail here.
net mobile AG is involved with payment transactions between mobile service providers and the two Dutch companies, and so is simply a mediator. My friend was able to call them and have the subscriptions that had been set up immediately cancelled. However, she would have to make arrangements with the Dutch companies, the service providers, to get her money back – according to the information from net mobile AG's customer service representative in Düsseldorf.
Globway B.V. is part of the Telefuture Group, so it is not surprising that both company offices are just a few metres from one another, a few kilometres north of the centre of Rotterdam. And the companies are not unknown in user forums and complaints offices either. There are countless messages about unwanted subscriptions having been set up in connection with the names.
On its website, Globway B.V. quite openly provides information about the payouts in various countries and using different payment methods. One example for Germany and the mobile billing service is that, if a service costing € 4.99 is sold to a user via T-Mobile, there is still € 2.68 profit left after taxes and fees. In the Vodafone network, it is € 2.86 profit according to the example calculation. Indeed, other costs will still need to be met by the purchasers, but these examples are a good indication of the potential profits from these transactions.
Conclusion
We can be certain that subscription traps represent a risk to mobile users. In the case described, the trap has been sprung in a particularly perfidious way. The subscriptions have been set up with no detectable consent or action on the part of the user, and this approach is something new.
This is further proof that "free" is not always the cheapest option. With hindsight, my friend would have preferred to set up the premium services directly in the flirting app, as an in-app purchase. For € 9.99 she would have received 250 virtual coins, which, according to information on the Internet, would have meant at least a month (!) of premium use. That would have given her considerably more usage time than the one hour for the activity she carried out, and it would have been cheaper for her too. That is quite apart from the time she has now had to invest to put in a complaint and cancel the subscriptions.
How to protect yourself
- Contact your mobile service provider and have them block third party provider services for your number. This will mean that no payments that you do not know about to third parties can be triggered. However, it also means that legitimate services can no longer used, such as paying for car parking and the like.
- Install a comprehensive security solution on your smartphone. G DATA Internet Security for Android offers effective protection for your smart device.
- Look at the reviews and comments about the apps, especially the negative ones.
But if it still happens
- Contact your mobile service provider and register a complaint about the payment. The "Letter template of Germany's consumer advice centre" can be useful here.
- Obtain all the available information about the mediators and third parties from your mobile service provider.
- Contact a specialist lawyer and get advice on whether legal action is a practical option in your case.
- The Federal Network Agency (Bundesnetzagentur) is a good port of call for information on unclear invoice items and the appropriate method of preserving evidence if the worst comes to the worst.